If your website runs on WordPress v4.5.3 website, attackers can now bring down your site through a Denial of Service attack. This is possible through two vulnerabilities that were disclosed on 22nd Aug:
- CVE-2016-6897 – This is a Cross Site Request Forgery vulnerability by which an attacker can take over an authenticated user’s session (privilege escalation) using a forged HTML page.
- CVE-2016-6896 – This is a Directory Traversal vulnerability which can be used by an attacker to crash the web server.
Fortunately, the vulnerability was disclosed to general public only after a patch was issued by WordPress. BUT, the patch was included in a major release of WordPress – Version 4.6.
So, just do the update, right?
Well, maybe not. For many websites, a major upgrade can lead to broken websites.
Why some WordPress sites can’t be upgraded
WordPress usually releases security fixes in minor revisions such as 4.5.2, 4.5.3, etc. These are small bug fixes, that do not radically change the core functions.
Whereas, major releases such as 4.5 and 4.6 changes core functions that can break current themes, plugins, or even introduce new server dependencies. It can lead to an upgrade failure, or in some cases, a broken website.
Bobcares provides of WordPress maintenance and server support for online businesses. In an online store that we manage, the upgrade failed with the below error:
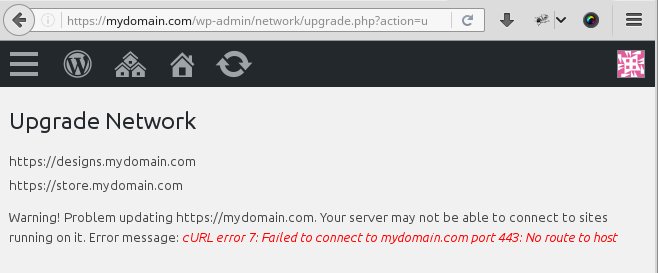
Here the upgrade failed due to incorrect DNS settings
There are other factors that makes an upgrade difficult:
- Users report a multitude of curl errors (like the one above) that indicates v4.6 needs PHP 5.6, MySQL 5.6 (or MariaDB 10.0) or greater. Resolving this may need server upgrades.
- Since the new version was released just over a week ago, many plugin/theme authors are yet to confirm their plugin’s compatibility with the new functions.
- Many websites, especially large online stores use customized WordPress themes and plugins. All these custom themes and plugins need to be thoroughly tested for compatibility, before it can be released in production.
All this leads to pretty long delays in upgrading to WordPress v4.6.
These websites are then sitting ducks for attackers.
Vulnerability mitigation without WordPress upgrade
Leaving a website un-patched is not an option.
So, for our customers, we employ alternative vulnerability mitigation strategies to prevent attacks. These are:
1. Blocking attacks using Web Application Firewalls
A solution that we’ve found to be very effective is to use Web Application Firewalls (aka WAFs). A WAF sits between the web server and website, and blocks website visits that looks malicious.
Now, it is important to note that WAFs are not silver bullets to block all attacks. New kinds of attacks come out every day, and WAF filters must be tested and customized to ensure 100% protection from a new threat.
For eg. NAXSI and ModSecurity are two popular WAFs we use to protect WordPress websites. Both these WAFs have “paranoid” mode rules that block Directory Traversal attacks (like in CVE-2016-6896). But it’s disabled by default because it blocks valid visitors as well.
So, to mitigate DoS attacks using CVE-2016-6896, Bobcares created custom WAF rules for NAXSI and ModSecurity that blocked accesses to “/dev/random” which is widely used in the DoS attacks.
Take away : If you have just one website in a VPS or a physical server, install NAXSI or ModSecurity, and enable Directory Traversal protection. Unless you have a heavily customized website, you run a low risk of blocking valid visitors.
2. Precise patching of affected functions or files
A vulnerability of any software, be it a CMS like WordPress or an operating system like Linux, often boils down to just one tiny bit of code.
For eg. in the case of CVE-2016-6896, the vulnerable code was in a function called wp_ajax_update_plugin() in the file ajax-actions.php.
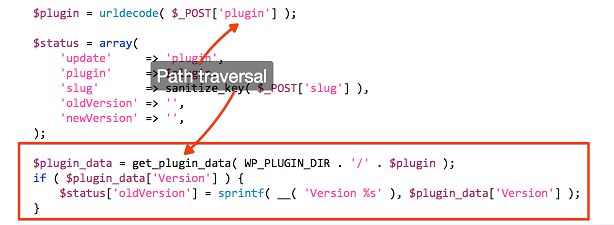
The vulnerable function. Image from : sumofpwn.nl
In such cases, we attempt to patch the vulnerable function to block exploits.
To fix CVE-2016-6896, we tracked down the official patches in WordPress bug tracker, and found that only 3 files need to be updated. These changes were carefully verified to make sure no other WordPress function will be affected by the patches.
Then, in the websites that could not be upgraded immediately, we applied these patches to blunt any possible attacks.
Take away : If you are comfortable tinkering around with WordPress files, download the patched files from WordPress bug tracker, and replace the old files with this one.
Of course it goes without saying that you’ll need to test your site functions thoroughly in a test environment before making it live.
In short..
WordPress 4.5.3 is affected by two vulnerabilities (CVE-2016-6896 and CVE-2016-6897) that can enable attackers to take down websites through DoS attacks. The official solution is to upgrade to 4.6, but such a major upgrade can break many websites.
Today we’ve seen alternate mitigation strategies for CVE-2016-6896 and CVE-2016-6897 in websites that need more time to test the new version.
Bobcares helps online businesses of all sizes achieve world-class security and uptime, using tried and tested solutions. If you’d like to know how to make your server more reliable, we’d be happy to talk to you.

0 Comments