Is your server a possible target of the ModSecurity Denial of Service CVE-2019-19886 attack?
ModSecurity helps us to stop attacks on our web application.
But the recent ModSecurity vulnerability CVE-2019-19886 published in January 2020, can make vulnerable servers standstill.
Here at Bobcares, we always patch our customer servers against such possible attacks as a part of our Server Management Services.
Today, let’s discuss ModSecurity and it’s CVE-2019-19886 vulnerability in detail.
Why we use ModSecurity?
ModSecurity is an open-source web application firewall. By monitoring the HTTP traffic, it helps us stop attacks against applications. It supports a flexible rule engine. Thus, we can perform simple and complex operations.
Generally, it blocks code injections and increases the security of the server.
As of January 2020, Version 3.0.4 is the stable version of the rewrite of ModSecurity using a different architecture with many improvements.
ModSecurity Denial of Service Vulnerability
Now its time to see more details of the CVE-2019-19886 vulnerability aka DoS vulnerability.
In simple words, this vulnerability depends on the Cookie parser as such. A Cookie-parser is a framework that lies between the operating system of the server and the software. It parses cookies attached to the client request object.
If a person targets this ModSecurity Denial of Service CVE-2019-19886 vulnerability, he will be able to send malformed HTTP Cookie header to the server.
It causes an out of range exception in the server. As a result, the ModSecurity in conjunction with the Nginx will crash the Nginx worker thread. The Nginx worker process thread is responsible for handling the request in Nginx.
Thus sending multiple requests to the server will crash worker threads. It even makes the server go down since the requests are faster than what the worker process can handle.
Overall, the vulnerability, in turn, could lead to a Denial of Service on the server.
How to fix ModSecurity Denial of Service CVE-2019-19886
Let us discuss how to overcome the vulnerability.
This vulnerability affects the server running Modsecurity version 3.0 to 3.0.3.
Therefore, the first step is to identify the version of ModSecurity running on the server. On Ubuntu/Debian servers, we find this by executing the command:
apt-cache show libapache2-mod-security2A sample output shows up as :
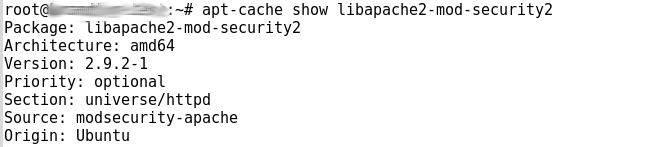
As seen, the server runs Version 2.9 and that’s not an affected version.
Similarly, in CentOS machines, we execute:
yum info mod_securityAnd, if the version shows up as between 3.0 and 3.03, we proceed further with the patch.
1. Upgrade to the latest version to fix Denial of Service
To fix the ModSecurity Denial of Service CVE-2019-19886 attack, we need to upgrade the ModSecurity to the latest version.
The vulnerability has been fixed in the latest version. Thus, we upgrade it to the ModSecurity v3.0.4 version.
Upgrading the ModSecurity might affect the normal functioning of the website. Therefore, our Dedicated Engineers take enough backups of the server configuration files. If an error occurs we analyze and fix the errors for our customers.
2. Apply the Patch file of ModSecurity
Recently one of the customers contacted us to fix the vulnerability. However, he did not want to upgrade to the latest version.
Our Support Engineers had to apply the ModSecurity_cookie_parsing_fix_303.patch which was released to fix this vulnerability. This patch works on top of the previous stable release preventing further exploits.
[Need any assistance ModSecurity upgrade – We can help you fix it]
Conclusion
In short, we have discussed the ModSecurity Denial of Service CVE-2019-19886 vulnerability. Also, we have discussed how our Support Engineers help our customers to overcome it.

0 Comments