WannaCry ransomware is all over the news now, causing the internet world to shake in doubt and fear. With over 200,000 computers in 150 countries being affected, the damage is really wide-spread.
For businesses and servers that are affected by this malware, the impact of this attack is huge and can lead to loss of business. As a result, it is important to secure your servers for ensuring their normal functioning.
How WannaCry ransomware affects your Windows 2003 and 2008 servers
WannaCry ransomware is a malware that affects all outdated Microsoft Windows servers that did not apply the critical security patch released by Microsoft in March 2017.
By encrypting the files on the infected servers, the hackers make the users unable to retrieve their data and demand ransom for releasing the data back to its owners.
This ransomware spreads from one server to others in its network, by using a vulnerability in Server Message Block (SMB) implementation of Windows systems, called ETERNALBLUE.
The Server Message Block (SMB) Protocol is a network file sharing protocol. Due to the security vulnerabilities in Microsoft’s implementation of SMB protocol, it has become a primary attack vector for intrusion attempts.
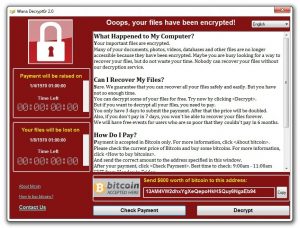
The malware can spread to other servers via emails that are sent from the infected server. After infecting, this Wannacry ransomware displays following screen on infected system:
WannaCry encrypts files such as commonly used Office documents, archives, media, emails, databases, encryption keys, certificates, virtual machine fines and other project files.
The files are modified in bulk using a batch script and the extension ‘.WCRY’ gets appended to the end of these file names. It also leaves a file ‘!Please Read Me!.txt’, that contains details of what has happened and how to pay the ransom.
A version 2 of the WannaCry ransomware malware is also circulating now, which is worse than the initial one. It is, therefore, crucial to protect your servers RIGHT NOW!
[ Securing your servers doesn’t have to be hard, or costly. Get world class Server Maintenance services at $74.99/server/month ]
How to protect your Windows 2003 and Windows 2008 servers from WannaCry ransomware
If your servers are running Microsoft Windows Server 2003 or Windows Server 2008 OS, and other vulnerable or outdated versions, then you are at risk.
To protect your servers, it is important to perform these security measures:
- Microsoft has released the security patches for all prominent OS versions, and the relevant security patch should be applied to your Windows 2003 and 2008 servers, at the earliest.
- It is crucial to backup all the critical server data and store them in a safer external storage.
- Mail servers should be secured and all outgoing and incoming emails should be scanned for malicious attachments or viruses.
- Configure the updated anti-virus programs that are smart enough to track these malware.
- Scan the server for WANNACRY ransomware hashes in files and remove the ones that are affected.
- Secure the server files and network to protect it from hackers and regularly audit the servers and network for any vulnerabilities.
- All software downloads should be monitored and controlled to prevent users from installing malicious scripts in the server.
- Use strong spam-filtering techniques to prevent inbound spamming and methods to avoid email spoofing.
- Disable the outdated SMBv1 protocol and block incoming traffic in SMB port 445.
- If the server is already infected, you need to temporarily disable SMB or block SMB ports and retrieve the infected files, or even do a fresh install and restore the files from backups.
Since some security patches are not available ready-made, and permanently disabling SMB can lead to functionality issues, the best strategy for your server should be chosen only with an expert help.
Though Microsoft had released security patches earlier, many server owners missed out in applying it on their Windows 2003 and Windows 2008 servers, causing them to be vulnerable to the attack.
[ You don’t have to lose your sleep over your server security. Our server specialists secure your servers at just $44.99/hr. ]
How can we help secure your Windows 2003 and Windows 2008 servers
At Bobcares, our security experts help secure servers for web hosts by updating them with the latest security patches and hardening the network and services.
With our regular top-down security audits and multi-layered security defenses, we enable our customers’ servers to stay impenetrable against any new threats or vulnerabilities.
Some of the security measures that our 24/7 server specialists perform in our customers’ Windows 2003 and Windows 2008 servers to protect them from attacks, include:
- Maintaining the Windows server software and applications updated with the latest security patches.
- Disabling email spoofing with the help of RDNS (Reverse DNS), Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) tools for domains.
- Monitoring the server logs and processes 24/7 for any suspicious activity and taking prompt corrective actions.
- Restricting user privileges and application permissions to block unwanted binaries from messing up the server.
- Deploying web and email filters to scan and block suspicious domains and email attachments from reaching the server.
- Configuring the latest anti-virus and other malware scanning tools that can identify and block malicious scripts.
- Setting up a fool-proof backup policy for critical server data and regularly validate the data integrity.
- Enabling data encryption for all critical services and securing web browsers with appropriate content controls.
- Securing the server using firewalls, disabling unwanted ports and protocols and segregating network into security zones.
- Conducting periodic security audits and Vulnerability Assessment and Penetration Testing (VAPT) to detect any exploits.
Much like how a fort is secured by a moat, canons, archers and steep walls, effective server security can be ensured only with multiple layers of defenses.
Bobcares helps online businesses of all sizes achieve world-class security and uptime, using tried and tested solutions. If you’d like to know how to make your Windows servers more secure, we’d be happy to talk to you.

0 Comments