In 2013, Docker introduced an easy way to build and ship applications. Currently at version 1.11, Docker is now perhaps the most popular light weight virtualization technology used by application developers.
However, Docker now has a competitor – rkt (aka rocket) which offers some unique features. So, what’s the difference?
What’s the difference between Docker and Rkt?
The rkt project was initiated in Dec 2014, when Docker was found to have several security issues. Rkt was designed to be a more secure, inter-operable, and open container solution in comparison to Docker.
Since then, Docker has covered a lot of ground in addressing all critical security issues. However, it is worth while to note how these two platforms differ in their various capabilities.
Here’s a list of the top differences:
1. Container image security
A great thing about Docker is that there’s a public registry from which anyone can download optimized application server images. So, if you want an Nginx server optimized for Magento web application, you’d get one from the Docker registry.
However, there’s a hidden danger in this. It is possible for an attacker to replace a server image with another one infected with malware.
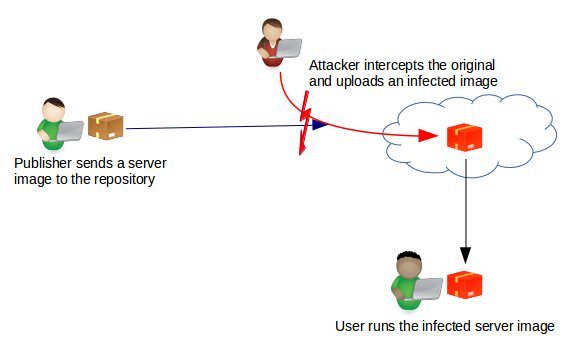
Prior to version 1.8, Docker didn’t have a way to verify the authenticity of a server image. But in v1.8, a new feature called Docker Content Trust was introduced to automatically sign and verify the signature of a publisher.
In rkt, signature verification is done by default. So, as soon as a server image is downloaded, it is cross checked with the signature of the publisher to see if it is tampered in any way.
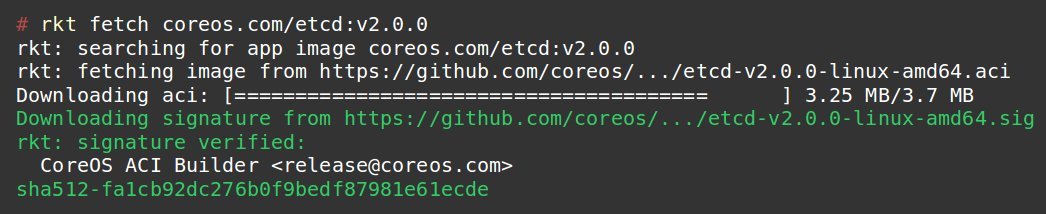
So, as long as you are running the latest version of Docker (v1.12) or Rkt (v1.3), you’re safe from this issue.
[ Make your container deployments and maintenance stress free. Our Server Maintenance plans start at just $74.99/server/month. ]
2. Preventing “root” privilege escalation attacks
Docker runs with super-user privileges (aka “root”), and spins off new containers as its sub-process. The issue with that is, a vulnerability in a container, or poor containment can give an attacker root level access to the whole server. CVE-2014-9357 was one such vulnerability.
Sure, Docker always recommended running containers within SELinux or AppArmor, but many server owners consider it too complicated, and skip the step.
Rkt came up with a better solution where new containers are never created from a root privileged process. In this way, even if a container break-out happens, the attacker cannot get root privileges.
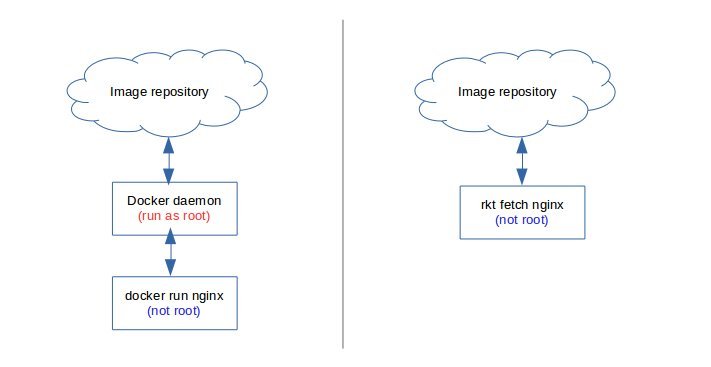
As a way to contain this threat, Docker loads AppArmor security modules by default. This prevents one user (container) from seeing another user’s files or memory content.
In addition, many additional features like user name spaces, un-privileged execution, etc. can be configured to keep Docker containers secure.
[ You don’t need to compromise on quality or cost for expert server management services. Our virtualization experts give you real-time solutions at affordable pricing.]
3. Flexibility in publishing or sharing images
When developing applications, it might be necessary to share container images with your technology partners. If you want to share Docker containers, you’ll need to setup a special private registry in your servers, or host it in a Docker paid account to share it with your partners.
For rkt, you just need your web server for it. rkt uses HTTPS protocol to download images and uses a meta description on the web server to point to the location. So, that’s one less server to maintain, and easier for partners to access.
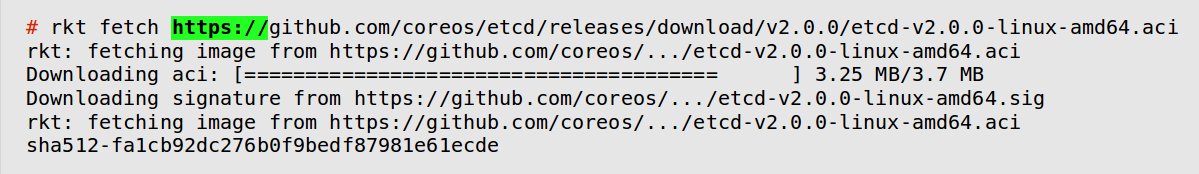
HTTPS is just one way to distribute ACI files. Using rkt torrent pull command, images can be downloaded over torrents.
4. Size of code base
Docker adds all it’s features to a single monolithic program file, which means, the number of code lines keep increasing as each new version comes out. And here lies a security problem. A single vulnerability in any of the thousands of lines of code can compromise the entire program, and essentially give root access to an attacker.
rkt, in contrast uses a modular architecture where features are developed as independent binaries by different vendors. The base code is kept as small as possible to reduce the attack surface area. This makes sure that even if a sub-component such as etcd is compromised, the damage would be limited to what that program can access.
[Update] – As of v1.11, Docker is moving away from the monolithic model, and are introducing functionally independent parts such as “containerd”, “runC”, etc.
[ Docker or Rkt, have you planned for backups in case of a failure? Don’t worry, our container management plan covers everything from setup to backup. ]
5. Portability to other container systems
New container systems come out all the time. What if tomorrow there’s a better container technology? With Docker, migrating to a new container technology could be a problem, as it uses a proprietary image format.
In contrast, rkt uses an open source container format known as “appc”. So, any server image created using rkt can be easily ported to another container system as long as it follows the “appc” open format.
By adhering to an open standard, rkt doesn’t enforce a vendor lock-in. This helps system owners migrate painlessly to another container system that suits their requirements better.
[Update] – As of v1.11, Docker is adopting an open standard called “Open Container Initiative”. Efforts are on to merge these standards together. However, it should be noted that Docker images are fully compatible with Rkt.
Inter-operability of OCI (of Docker) and Appc (of Rkt) – Status as of 2015. [Image from CoreOS.com]Which one should you choose?
If you have already invested well into a Docker system, and have locked it down tight, you don’t have a reason to switch right away. But if you are planning on moving away from traditional dedicated servers to a virtualized system rkt might be worth checking out.
Either way, it is important to know that site reliability is dependent on how well you are able to predict production system fault points, and design system redundancies to counter it. A knowledge of pros and cons of competing technologies can come in handy while designing such a system.
Bobcares helps business applications achieve world-class performance and uptime, using tried and tested server architectures. If you’d like to know how to make your server infrastructure and operations more efficient, we’d be happy to talk to you.

0 Comments