pfSense offers a Captive Portal for the user’s network. Read the article to learn more about it. At Bobcares, with our pfSense Support Services, we can handle your issues.
Overview
- An Introduction to Captive Portal by pfSense
- Setup Steps for a Basic Portal without Authentication
- Setup Steps for a Basic Portal with Authentication
- Portal Page Personalization
- Other Settings
- Conclusion
An Introduction to Captive Portal by pfSense
pfSense offers a simple solution for configuring a captive portal on our network. We may require users on the network to see a certain webpage before they are permitted to access the internet by using the portal. The website may consist of a straightforward page with terms of service and instructions or it may require a login and password in order to authenticate.
Wireless hotspots are the most typical use for captive portals. If we have ever connected to a wireless network at a hotel or airport, we have probably had to navigate through a gateway in order to access the internet. Additionally, they may be utilised in the house, in business centres, and at internet cafés with wired connections.
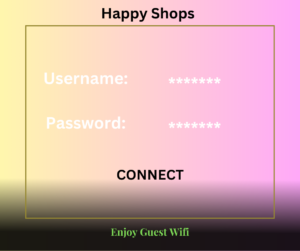
Once the portal has been enabled any computer that points to the pfSense router as the gateway will be automatically redirected to the portal landing page.
Setup Steps for a Basic Portal without Authentication
Let us examine how to create a simple portal that does not require login. The HTML page of our choosing will be displayed to clients that join the network. We may choose what message or image this page displays. Before being able to enter the network, users need to click the proceed button on the portal.
1. Click the captive portal, located in the pfSense services menu, to activate the portal. Check the “Enable captive portal” box.
2. The LAN interface will be chosen by most users. pfSense is not able to function as a reverse portal, and the captive portal can only operate on one interface at a time.
3. To use it as a landing page for customers connecting to the portal, we need to upload an HTML/PHP file. Click the “Choose File” button and choose the HTML page we wish to use in the “Portal page contents” area. To save the changes when we’re done, click the save button at the bottom of the page.
Click the “view current page” button, which is located just below the HTML file upload box, to confirm that the HTML file was uploaded successfully.
4. To verify that everything is functioning properly, just attempt to view a webpage from a networked computer.
The landing page will be shown in the browser if everything is operating as it should. Upon selecting “Continue,” the browser ought to proceed to the URL that was first requested.
Check that the HTML file was submitted successfully if the gateway page does not load. Also, make sure that the parent VLAN isn’t allocated to another interface if the captive portal is operating on a VLAN interface.
Setup Steps for a Basic Portal with Authentication
Providing a mechanism for user authentication prior to granting access to the internet is another common justification for the usage of captive portals. The network will not allow access to users without a working login and password.
1. The easiest method of configuring authentication on pfSense is to use the local user database. Since radius authentication is considerably more versatile, I would suggest utilising it if we have a large number of people to handle. Either install the FreeRadius package directly on pfSense or set up the captive portal to refer to a distant radius server. Radius easily interfaces with the current active directory and other authentication systems.
2. So, to get started, activate the captive portal and choose an interface by following the instructions in the preceding section above.
3. Also, we must use a slightly modified HTML landing page with login and password boxes for this to function. In order to upload the page, adhere to the directions in step 3 of the preceding section.
4. On the main captive portal settings page, choose either local or radius authentication to enable authentication. Also, to make the changes effective, click the save button.
Local User Creation
We will need to create some users if we choose the local user manager as the authentication mechanism. We suggest switching from the local database to Radius, LDAP, or Active Directory if we intend to build up a large number of users.
This option is good if we don’t plan on creating a lot of accounts because it’s really straightforward. It is also quite acceptable to allow users to share a login and password in some situations.
Open the user manager (located under the system menu) in order to create users in pfSense. Then, to add a new user, just click the + sign.
User Account Setup
All we have to do to establish a basic account is input the username and password. Still, there are a couple more helpful choices that are well worth looking into.
Expiration Date: We can choose the date on which the account will automatically expire using this option. Thus, this will spare us the effort of having to manually disable the account if we are aware that it is only temporary. When we omit this option, the account will remain active always.
Group Membership: We may organise the users with the help of groups. Access to administer specific areas of the pfSense web GUI can be granted to groups. Groups aren’t all that helpful for the portal’s objectives.
Portal Page Personalization
We can add our own graphics and custom PHP code to the gateway home page to give it a prettier appearance.
Click the file manager tab in the captive portal settings to upload a picture. Files must include the prefix “captiveportal-” in their names in order for the portal to use them. The files can then be referenced using regular HTML image tags.
Other Settings
We can change a lot of different options on the main captive portal page to personalise the way the portal works. The settings for a few of the ones are described below.
Idle timeout:
A user will be automatically disconnected after a predetermined amount of inactivity, usually thirty minutes. To prevent the pfSense system’s resources from becoming overloaded, we must establish an idle timeout. Even lowering the timeout to eight hours can assist. We don’t want to make it too low, since this will irritate the users.
Redirection URL:
By default, after navigating the portal, visitors will be sent to the webpage they initially requested. With this feature, we may make customers connect to the page of our choice by default. The user may then go to a new URL and use the internet as usual.
Concurrent user logins:
If this option is enabled, each user will only be able to connect to the portal once. By doing this, users won’t be able to create numerous accounts with the same password and username.
[Want to learn more? Reach out to us if you have any further questions.]
Conclusion
It is quite probable that we are sharing a single internet connection with several users if we are operating a captive portal system. If so, we advise setting up pfSense to function as a transparent proxy server in order to save bandwidth on the internet.
We can also consider of using traffic shaping to enhance the functionality of the shared connection even further. One way to stop users from misusing bandwidth when downloading files is to utilise traffic shaping.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.




0 Comments