Virtualization using Docker containers has gained popularity in application hosting, owing to its light-weight design and fast-deployment features.
Docker architecture is in such a way that the containers can connect to the outside world by default. But you cannot access the container directly from outside.
While disabling external access is a good security measure, there maybe many instances where you need to access the container data from outside, such as application testing, website hosting and so on.
Setup and manage your Docker system
To allow external access to Docker containers, you would have to expose their ports by mapping a container’s port to an external port in the host. Today we’ll see how to expose docker ports to make them accessible from the internet.
What is port binding in Docker?
Suppose you want to run an NginX web server application in your Docker container. You can install the nginx image and start a container but you cannot directly access it from outside network.
Docker containers have an internal network and each container is associated with an IP address that can be accessed from the Docker host machine.
Being internal IP, this IP cannot be used to access the containers from external network. But the Docker host machine’s main IP is accessible from outside.
For a webserver application, you’d obviously need to enable user access to it from the external network. So, the solution we use is to bind the internal port 80 of the Docker container to a port on the host machine, say 9000.
With this port forwarding or port binding feature, users can access the webserver at container port 80 using the host machine port 9000. Users may not even notice this backend forwarding while accessing the webserver.
[ Are your spending too much time managing your Docker containers? Our Docker experts take care of your infrastructure and ensure its smooth functioning. ]
How to expose docker ports during container creation
Exposing Docker ports can be done using the ‘-p’ option with ‘docker run’ command to bind the port when launching the container:
docker run -d -p 9090:80 -t nginx
This command will create a container with the image ‘nginx’ and bind the container’s port 80 to the host machine’s port 9090.
You can verify this using ‘docker ps‘ command:
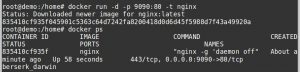
Expose Docker port during container creation
To see the port bindings of a specific container, use the ‘docker inspect [container-id]’ command:

Port bindings of container
Once the port exposure is complete and the container is up and running, the internal port 80 of the container can be accessed using the host machine IP and port, at http://host-ip-address:9090/ .
[ Running a Docker infrastructure doesn’t have to be hard, or costly. Get world class Docker management services at affordable pricing. ]
How to expose multiple docker ports
We saw how mapping one container port to one host port is done during container creation. But this one-one mapping may not be feasible in the case of a multiple container setup where it is not practical to allot one host port dedicated to a container.
In such instances, it is possible to map a range of ports in the docker host to a container port, using the command:
docker run -d -p 7000-8000:4000 web-app
This would bind port 4000 in the container to a random port between 7000 and 8000 on the host, depending upon the port that is available in the host at that time.
To update Docker regarding the ports that the container listens on, the parameter ‘EXPOSE’ can be set in Dockerfile:
EXPOSE <CONTAINERPORT>
Expose Docker port to a single host interface
By default, the ‘-p’ flag will bind the specified port to all the network interfaces on the host machine. But this may not be required in all scenarios and there may be cases where need to restrict the port binding to a single interface – say, localhost – only.
This can be done by mapping the container port to the host port at a particular interface, as follows:
docker run -p 127.0.0.1:$HOSTPORT:$CONTAINERPORT -t image
The command ‘docker port [container-id]’ can be used to see the port mapping of a particular container.
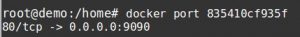
Verify container port mapping
Expose docker ports randomly during build time
To randomly map any network port inside a container to a port in the Docker host, the ‘-P’ option can be used in ‘docker run’:
docker run -d -P webapp To see the port mapping for this container, you can use ‘docker ps’ command after creating the container.
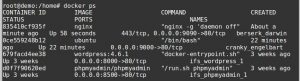
Docker container ports
Summary
Today we saw how to make the Docker containers accessible from outside, using the ‘docker port expose’ method. But port mapping is not a trivial task and should be done with utmost care to avoid conflicts.
Firewall rules would also have to be configured to block unauthorized access and to ensure container security. The ports assigned for containers would vary depending on the application running in it and the business purpose served.
If you’d like to know how to manage your Docker system and to get the best out of them for your business, we’d be happy to talk to you.







how do you go the other way: To access a port outside of a docker container on another machine?
Hi,
Please contact our support through live chat(click on the icon at right-bottom).