The AWS secrets manager with Terraform module helps to create secrets in the Amazon AWS Secrets manager. It can protect and manage secret user credentials. Bobcares answers all queries, large or small, as part of our AWS Support Service.
AWS Secrets and the Secrets Manager
AWS Secrets and AWS secret manager is a service. It helps the users protect their application, services, and IT resource access secrets. Before AWS, database or application passwords were all saved in files. Consequently, updating the information used to take hours. Subsequently, the whole application will crash if a single file is lost. Therefore, the files would get corrupted without regular care.
To deal with this issue, the AWS Secrets Manager Service uses automated recovery of the secrets or passwords. The AWS secrets Manager rotates user information at scheduled periods to keep them safe.

After restoring secrets from Secret Manager, the program connects to the database, as shown in the image above. Admin collects secrets from the AWS Secret Manager and stores them in the database.
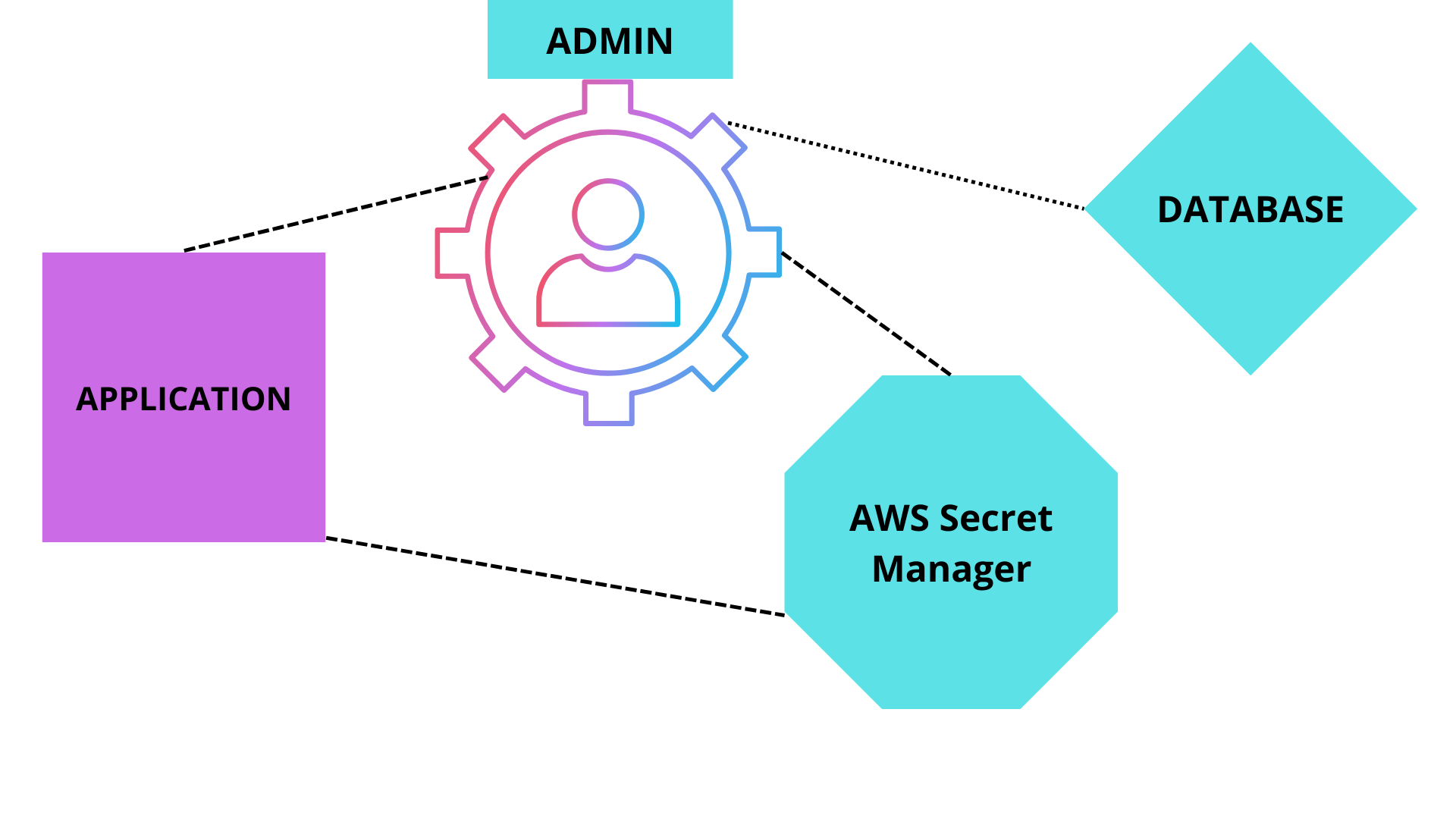
Importance of AWS Manager
The AWS Secrets Manager is the most reliable way to save confidential user credentials. Protecting sensitive information and managing them is vital for ensuring user security. The AWS secrets manager will let the user save the information such as Database credentials, SaaS applications Credentials, Third-party API keys, SSH or secure shell keys, and on-premise resource info.
The AWS manager is equipped with many features to ensure credential safety. Automatic secret rotation, replication, usage auditing, program-based retrieval of secrets, and finally, Compliance. These features let the user save and manage all of their credentials effortlessly. Therefore, the service lets the user manage and rotate database credentials, other credentials, and API keys throughout the life cycle.
Automatic Rotation of Secrets
Automatic secret rotation is one of the advanced features of the AWS secret manager. With the Secrets Manager console, AWS CLI, and AWS SDK, users can schedule or rotate the info on demand. For example, at the initial stage of storing the credentials, the user can configure the database type, rotation frequency, and master database credentials.
In short, secret rotation in AWS refers to periodically updating the user secrets. The automated rotation feature of the AWS secret manager ensures the user has an extra layer of security.
Secret Usage Auditing and Monitoring
Monitoring, AWS logging, and notification services are integrated with AWS secret manager. Hence, the users can audit and monitor secrets through the AWS manager. For example, consider the activation of CloudTrail for an AWS region. And the user can check the CloudTrail log to audit the details of the secrets.
Similarly, when the secrets are left unused for a certain period, the AWS will notify it through the mail. The user can configure these features with the Amazon Notification services.
Requirements for AWS Secret Manager
- Ubuntu machine 20.04 version is a great choice. And, if the users do not have a machine, they can build an AWS EC2 instance on their AWS account. The minimum machine requirements are 4GB RAM and at least 5GB of storage space.
- The Ubuntu system must have an IAM role connected. It also must have access to the AWS Secret Manager or administrator abilities to create AWS secrets.
Terraform Files and Directory Sturtcure
Terraform setup files are in a tree layout structure. This allows to ease the code with .tf format or .tf.json or .tfvars format. The configuration files are available inside the Terraform modules. Terraform modules are at the top of the hierarchy with the configuration files. More than that, terraform modules can call another child to terraform modules from the directories, disc, or the Terraform registry.
Terraform consists mostly of five files: main.tf , vars.tf , providers.tf , output.tf, and terraform.tfvars. And, their functions and rules are listed as listed down below.
- main.tf– Terraform main.tf file contains the main code to define the resources to build, update or manage secrets.
- vars.tf – The input variables that are customizable and defined in the main.tf configuration file, which is contained in the terraform vars.tf file.
- output.tf: In this file, the user can declare the output parameters after the execution of Terraform apply command.
- terraform: This directory has the latest backend configuration in addition to the cached providers, modules, and plugins. Terraform controls this and creates it once the user issues the ‘terraform init’ command.
- terraform.tfvars: The file holds the values for variables referred to in the main.tf but declared in vars.tf file.
- providers.tf – The most important file where the user sets terraform providers, including terraform aws provider, terraform azure provider is porvide.tf. The files authenticate the cloud provider.
Terraform Configuration for Creating AWS Secrets and Secrets Versions on AWS
To build AWS secrets, let’s create the Terraform configuration files.
- Firstly, use the preferred SSF client to log in to the Ubuntu system.
- Secondly, switch to the ‘terraform-demo-secrets’ folder created in the opt directory
mkdir /opt/terraform-demo-secrets cd /opt/terraform-demo-secrets - After that, create and name the file as ‘main.tf in the/opt/terraform-demo-secrets’ and copy/paste the ‘below content’. The file generates a secret password for the user ‘adminaccount’ on AWS(Masteraccoundb). And it will also create a secret version with AWS secret ((Masteraccoundb).
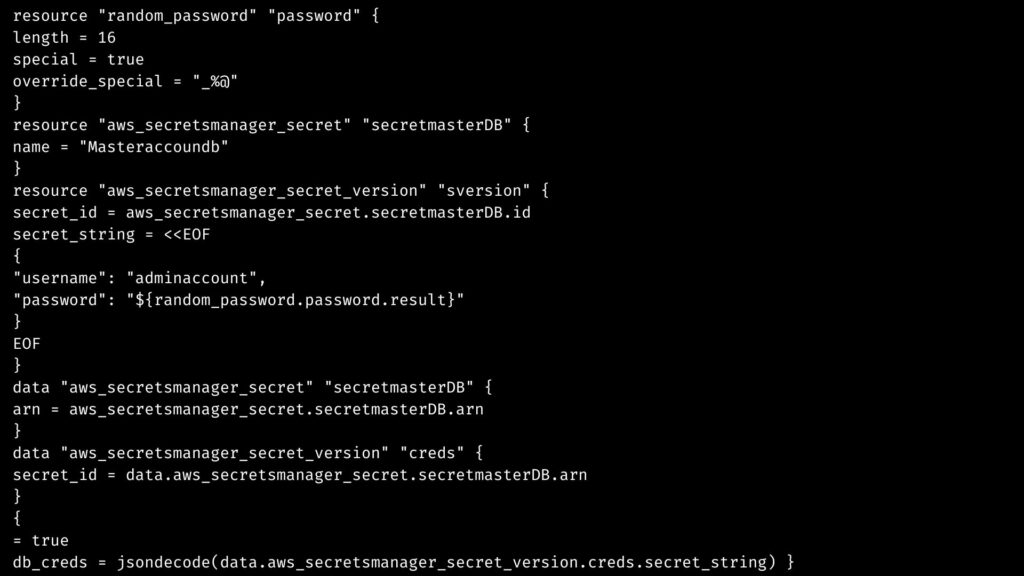
- Finally, make a new file with the name ‘provider.tf’ and place it in the /opt/terraform-demo-secret dictionary. And, the file lets Terraform communicate with the AWS cloud using the AWS API.
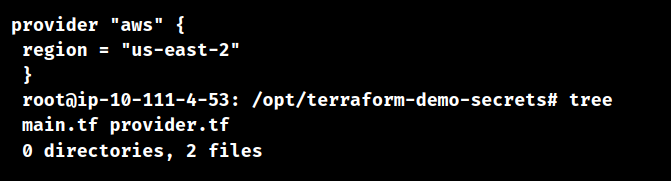
Checking files in the Terraform Demo Secrets Folder
- Firstly, use the terraform init command in the /opt/terraform-demo-secrets’ directory to initialize the terraform.
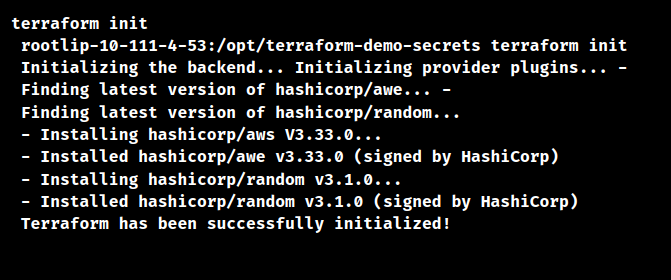
As a result, the terraform will be in the Initializing stage using the Terraform unit command.
- Secondly, to get the details of the deployment we have to run the plan command. Run the terraform plan to confirm the availability of the details or the resources.
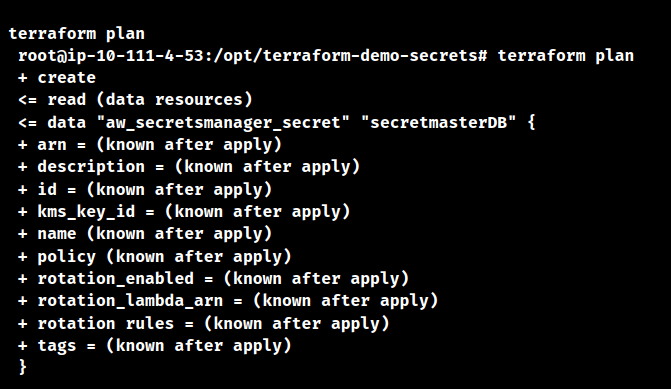
As a result, the terraform plan command will be in the running stage.
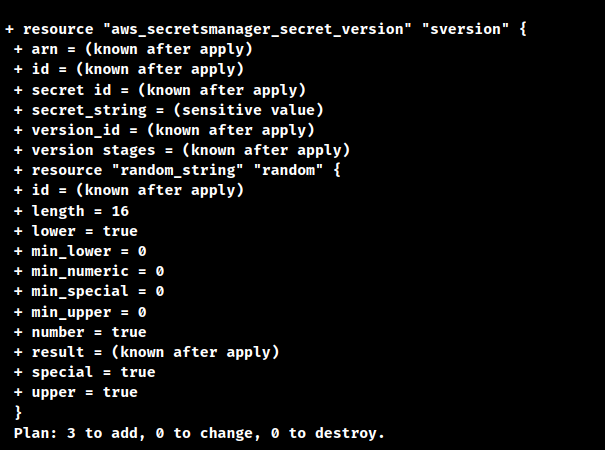
As a result, the terraform plan command output will open up as shown above.
- Finally, after the verification and output generation, we can use the terraform and apply the command for deploying the code.
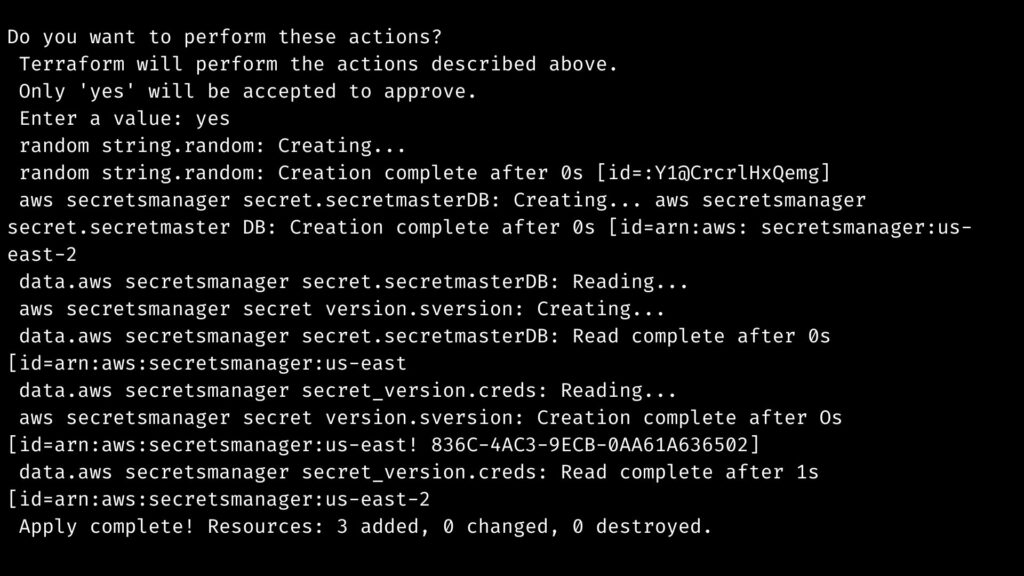
As a result, the apply command will be run.
As a result of the process, the user can see the new secret in the AWS account. A user can view the value of the retrieved secret by clicking on the secret.
[Need assistance with similar queries or want to learn more about AWS secrets manager terraform? We are here to help]
Conclusion
To conclude, it is vital to keep user credentials secure. The AWS secret manager can save and manage user info. The AWS secrets manager terraform module helps to create secrets in the AWS manager.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.







0 Comments