Cache poisoning on Cloudflare is the act of inserting misleading information into Cloudflare DNS cache, causing DNS requests to return an inaccurate response and users to be sent to the wrong websites. At Bobcares, with our Server Management Services, we can handle your Cloudflare issues.
Cache Poisoning On Cloudflare
DNS cache poisoning, also known as DNS spoofing, is the act of inserting false information into a DNS cache, causing DNS requests to return an inaccurate response and redirecting people to the wrong domains.
How Does Cache Poisoning Work?
A malevolent user can mislead the origin into producing a “poisoned” version of index.html with the same cache key as an innocent request by crafting an HTTP request. Other users may receive this file after caching. Since an attacker can inject any data or resources into a customer’s website, we take this vulnerability very seriously.
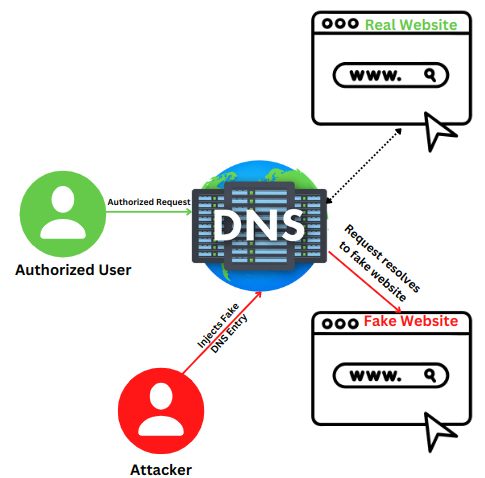
Some origins transmit information from HTTP headers that are not in the cache key. In order to know better, let’s consider an example.
REQUEST
GET /2019/08/20/cache.html HTTP/1.1 Host: blog.bobcares.com X-Forwarded-Host: bobcares.bloghost.com
RESPONSE
HTTP/1.1 200 OK Cache-Control: public, max-age=604800
<html> <img src="https://bobcares.bloghost.com/img/share.jpg"/>
This returning data from the origin unescapes and hackers can exploit it in terrifying ways.
REQUEST
GET /2019/08/20/cache.html HTTP/1.1 Host: blog.bobcares.com X-Forwarded-Host: a."><script>alert(1)</script>
RESPONSE
HTTP/1.1 200 OK Cache-Control: public, max-age=604800
<html>img src="https://a. "><script>alert(1)</script>
Now the attacker can get arbitrary JavaScript to execute on this webpage. Other variations of the attack could deceive a client into downloading an undesirable but benign-looking resource, which would have negative effects. The X-Forwarded-Host header can be in many requests that have passed via another proxy before coming to Cloudflare. Some origins may use this value to serve web pages.
Preventive Strategies For Cache Poisoning
- Know the cache poisoning: Firstly, having a better understanding of the issue helps us to take the appropriate preventive measures.
- Truly static cache files: Also, make sure we are caching static files that do not in any way rely on user input by reviewing the cache configuration for the origin web server.
- Never rely on data from HTTP headers: HTTP headers are frequently used to exploit client-side vulnerabilities, such as cross-site scripting. So, never rely on HTTP header data.
- Don’t rely on GET Request bodies: We cannot rely on the GET request bodies and must not use them to change a response’s contents. Consider bypassing the cache or utilizing a POST request if a GET body can alter the contents of the response.
- Monitor web security: It is equally important to monitor web security advisories on a regular basis. The most popular advisories include Drupal Security Advisories, Zend Security Advisories, and Symfony Security Advisories.
[Searching for a solution to another question? Get in touch with us.]
Conclusion
Cache poisoning is a major threat that can affect the security of the system. In order to prevent such attacks, we here provide some simple preventive strategies from our Tech team for cache poisoning on Cloudflare.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.







0 Comments