With most businesses moving online, internet security has become a crucial aspect. Vulnerabilities are being exposed so constantly in the web world that any day you can wake up to a new exploit or a hack.
To be on the safer side and to protect the data and transactions from attackers, all server owners have secure protocols such as SSL or TLS installed in their servers.
See how we add value to your business!
SSL is a protocol that is used to securely transfer data in the internet. The SSL versions, when enabled in both the server and the client such as web browsers, help establish secure connection to transmit confidential data via web.
But if the secure protocol that you use for the data transmission itself is vulnerable, chances are that the hackers can exploit it and sniff out your confidential data.
What is SSLv3? Why is it unsafe?
SSL has released two protocol versions namely SSLv2 and SSLv3. Though SSLv2 was widely used initially, it was found insecure later on. SSLv2 was followed by SSLv3, which improved upon the former by adding stronger ciphers and certificate authentication.
But SSLv3 was based on a weaker key derivation process, which makes it insecure and unsafe. As a result, it is important to disable SSLv3 and replace it with secure TLS protocol.
[ A single downtime can affect your business. See how our 24/7 expert team helps you deliver zero downtime services. ]
Why is SSLv3 dangerous?
In October 2014, Poodle attack, that exploits the security issues in SSLv3 protocol design, was revealed. This SSLv3 vulnerability allowed an attacker to easily track the contents transferred in SSLv3 connections.
Since most web browsers support and use SSLv3 protocol, this was a wide-spread attack and caused panic among internet users. The security of all confidential transactions went for a toss.
The solution for this vulnerability is to disable SSLv3 version from the web server and enable TLS encryption, which is considered more secure than SSL.
At Bobcares, our 24/7 Security expert team immediately alerted us about this vulnerability and this helped us to secure our customers’ servers pro-actively to avoid hacks by disabling SSLv3 in the servers.
[ Take care of your customers, before your competitors do. Get world-class support specialists to delight your customers. ]
How to disable SSLv3 in webservers
While online transmissions happen through all common internet services such as email, web, etc., it is through the webservers that the maximum data transfer takes place.
Today we’ll see how to disable SSLv3 protocol in the commonly used web servers – Apache, NginX & IIS.
How to disable SSLv3 in Apache
If you are using apache web server, here is how you can disable SSLv3 protocol:
- Edit the apache SSL configuration file at ‘ /etc/apache2/mods-available/ssl.conf ‘ using a text editor such as vi.
- Go to the section of SSL directives and edit the line
to SSLProtocol All -SSLv2 -SSLv3SSLProtocol all - Add the CIPHER text:
SSLHonorCipherOrder On
SSLCipherSuite ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:RSA+AESGCM:RSA+AES:!aNULL:!MD5:!DSS
4. Save the file, test the new configuration and restart the apache service.
/etc/init.d/apache2 restart
You can also do this security update from the WHM of the webserver at the ‘Apache Configuration’ screen -> Global Configuration -> SSL/TLS Protocols section.
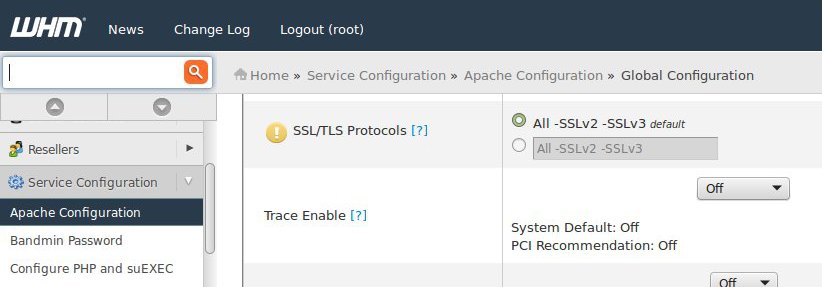
Disable apache SSLv3 protocol from WHM
After making the changes, ‘Save’ the settings and the vulnerable SSLv3 protocol would be disabled upon the Apache webserver restart.
How to disable SSLv3 in NginX
If you are using NginX as web server, update the Nginx configuration (/etc/nginx/nginx.conf):
Change the line:
ssl_protocols SSLv2 SSLv3 TLSv1 TLSv1.1 TLSv1.2;
to
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
Restart Nginx and confirm that SSLv3 is disabled.
How to disable SSLv3 in IIS
To disable the SSLv3 protocol in IIS servers, you would have to edit the registry entries. The location of the registry key may vary with the Windows server version.
In the ‘Registry Editor’ window, find the section ‘SSL 3.0’ under Protocols file:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel\Protocols\
To disable the protocol, create a new ‘DWORD’ value in the server subkey of the protocol and set it to “00 00 00 00.”
Registry changes may require server restart to come into effect. Also, adequate backups and caution has to be taken during registry edits, as it can mess up the server if not done right.
[Don’t lose your sleep over server attacks! Our 24/7 server experts will maintain your servers secure and lean, at affordable pricing. ]
Testing after disabling apache SSLv3
After disabling SSLv3 for your webserver, you can verify that using the command :
openssl s_client -servername domain.com -connect IPaddress:443 -ssl3
In the output that shows, you can see that ‘Secure Renegotiation is NOT supported’, which shows that SSLv3 is disabled in your server.

Confirm that SSLv3 is disabled
Once you confirm that SSLv3 is disabled for your webserver, everything is good to go and you don’t need to worry about the POODLE attack.
In short..
Here we’ve seen why SSLv3 is unsafe how to disable it in different web servers. For web server configurations with separate SSL sections for each virtual host, the changes would have to made in those sections too.
For additional security, we also disable SSLv3 in other services such as SMTP, FTP, POP/IMAP, cPanel, HAProxy, etc. The entries to be changed can vary based on the version of each service.
Along with disabling SSLv3 in server, the vulnerable protocol should be disabled in the browsers such as firefox, google chrome etc. too, for additional security.
At Bobcares, we minimize the risk of exploits by implementing certain TLS/SSL best practices that helps to lock down the encrypted communication for our customers.
Bobcares helps online businesses of all sizes achieve world-class security and uptime, using tried and tested solutions. If you’d like to know how to make your server more reliable, we’d be happy to talk to you.







0 Comments