Let’s see how to allow unauthenticated invocations in Google Cloud Run. As part of our Google Cloud Platform Support Service, Bobcares provides answers to all of your questions.
How to Allow Unauthenticated Invocations in Google Cloud Run?
A service may allow unauthenticated invocations if the allUsers member type is given the IAM Cloud Run Invoker role. To set up verification on a Cloud Run service, we need to have the run.services.setIamPolicy permission. This role is part of both Cloud Run Admin and Owner roles.
Steps to Take
1. Go to Google Cloud console.
2. Click the checkbox at the left of the service we want to make public. (Don’t click on the service itself.)
3. In the details pane in the top right corner click the Permissions tab. If the pane isn’t visible, we may need to click Show Info Panel, then click Permissions.
4. Click Add principal.
5. In the New principals textbox, enter the value allUsers.
6. From the Role dropdown menu, select the Cloud Run Invoker role.
7. Click Save.
8. We will be prompted to verify that we would like to make this resource public. Click Allow public access to apply the change to the service IAM settings.
9. For a new service we are creating, create the service but make sure we select Allow unauthenticated invocations in the Authentication tab to make the service publicly available. Selecting Require authentication will make the service private.
Gcloud :
To make a service publicly accessible, use the gcloud run services command to add the special allUsers member type to a service and grant it the roles/run.invoker role:
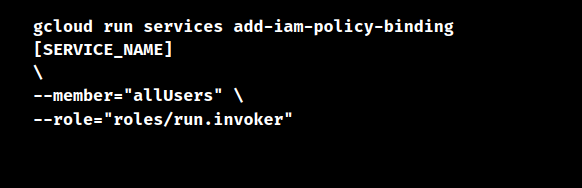
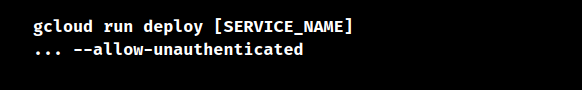
Also, when we deploy the service, we can use the below code to make it publically accessible:
[Need to know more? We’re available 24/7.]
Conclusion
In conclusion, the article offers the steps from our Tech team to allow Unauthenticated Invocations in Google Cloud Run.




0 Comments