Learn more about the Kubernetes Deny All Network Policy. Our Kubernetes Support team is here to help you with your questions and concerns.
Kubernetes Deny All Network Policy
Did you know that the “deny all” network policy in Kubernetes lets us prevent network communication between pods within a Kubernetes cluster?
This policy stops all traffic by default, except for permitted connections. This creates a “zero-trust” security model.

By default, Kubernetes permits communication between pods within the same namespace. However, by applying a “deny all” network policy, we can deny all traffic between pods unless allowed by other network policies.
The “deny all” network policy acts as a proactive measure. It stops network communication between pods within the cluster.
By defining a policy that denies all ingress and egress traffic, we can create a secure network environment.
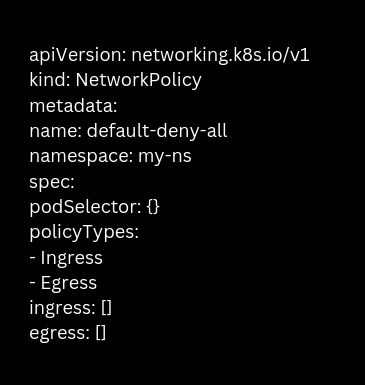
This configuration ensures that all network traffic, including unexpected elements like DNS lookups, needs explicit NetworkPolicies for permission.
Furthermore, we can add other policies to allow specific types of traffic between pods. These rules override the default deny behavior.
Our experts would like to point out that the “deny all” network policy comes in handy in setting network isolation between different namespaces in a Kubernetes cluster. It stops pods in one namepsace from communicating with pods in other namespaces.
Implementing a “deny all” network policy in Kubernetes is a smart move. It boosts the security posture of our cluster. By adopting a “zero-trust” model, we can strengthen our containerized applications.
[Need assistance with a different issue? Our team is available 24/7.]
Conclusion
In brief, our Support Experts introduced us to the Policy and how it improves security.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.







0 Comments