Learn more about integrating Linode Nodebalancer Kubernetes. Our Linode Support team is here to help you with your questions and concerns.
Linode Nodebalancer Kubernetes | Integration
Expanding your Kubernetes cluster for external traffic needs seamless integration with a load balancer.
By adding the right configurations to your setup, we can set up Linode NodeBalancers to manage external access easily.
Setting Up NodeBalancers
To start the integration, add the following lines into either a new configuration file or add them to a Service file. When we apply the configuration to the cluster, Linode NodeBalancers will be up and running. Thereby, enabling access via a public IP address.
These NodeBalancers direct external traffic to services hosted on healthy nodes within the cluster.
To inspect NodeBalancers operating within the cluster:
kubectl get servicesFor detailed information about a specific service and the NodeBalancers run:
kubectl describe service example-serviceEnabling TLS Encryption with Linode NodeBalancers
As protecting the external connections is important, Kubernetes uses Secret objects to store sensitive data.
We can follow these steps to create a Kubernetes secret containing Transport Layer Security (TLS) certificates and keys:
- To begin with, generate a TLS key and certificate via OpenSSL. We have to replace the CN and O values with our domain information:
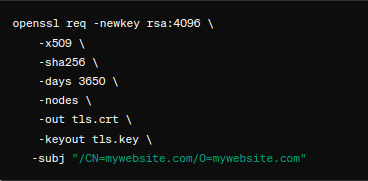
- Then, create the secret as seen here:
kubectl create secret tls $SECRET_NAME --cert tls.crt --key tls.keyMReplace, `$SECRET_NAME` with the chosen identifier.
- Now, make sure the Secret is stored by running this:
kubectl describe secret $SECRET_NAME
Configuring TLS within a Service
By default, Kubernetes services lack TLS termination over HTTPS. To enable HTTPS, we have to modify the Service. This is done by adding the following snippet to the Service file to enable TLS termination on NodeBalancers:
File: example-service.yaml
metadata:
annotations:
service.beta.kubernetes.io/linode-loadbalancer-default-protocol: http
service.beta.kubernetes.io/linode-loadbalancer-port-443: '{ "tls-secret-name": "example-secret", "protocol": "https" }'
In order to direct traffic consistently to specific pods and boost performance add these lines to the Service configuration file:
spec:
type: LoadBalancer
selector:
app: example-app
sessionAffinity: ClientIP
sessionAffinityConfig:
clientIP:
timeoutSeconds: 100
Furthermore, we can remove a NodeBalancer and its associated Service with the Service manifest file we used during creation. All we have to do is run the delete command with the file name using the `-f` flag:
kubectl delete -f example-service.yamlAlternatively, we can delete the Service by name:
kubectl delete service example-serviceAfter deletion, the NodeBalancer will be removed from our Linode account.
Serving Multiple Applications with a Single Load Balancer
- If no application is running, start a sample application deployment:
kubectl create deployment my-dep --image=gcr.io/google-samples/hello-app:2.0 --replicas=3 --port=8080
- Then, install the NGINX Ingress Controller:
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.3.1/deploy/static/provider/cloud/deploy.yaml
- Next, verify deployment success:
kubectl get all -n ingress-nginx - Now, it is time to define a service exposing the previously deployed application:
# File: my-dep-service.yaml
apiVersion: v1
kind: Service
metadata:
labels:
app: my-dep
name: my-dep
spec:
type: ClusterIP
ports:
- name: http
port: 8080
protocol: TCP
targetPort: 8080
selector:
app: my-dep
- We can apply the configuration with this command:
kubectl apply -f my-dep-service.yaml - Then, create an Ingress object to route incoming traffic to the service:
kubectl apply -f my-dep-ingress.yaml - Now, verify the Ingress object creation:
kubectl get ingressNow, we can access the application via the provided IP address, now directed through the Ingress object.
[Need assistance with a different issue? Our team is available 24/7.]
Conclusion
In brief, our Support Experts introduced us to Linode Nodebalancer Kubernetes integration.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.







0 Comments