Learn how Mirai Variant V3G4 targets Linux systems. Our Server Management Support team is here to help you with your questions and concerns.
Mirai Variant V3G4 targets Linux Systems | Latest Security Update
You must have already come across several news reports about how the infamous Mirai malware has been causing trouble for cyber defenders with its constantly evolving offensive capabilities.

According to our experts, the Mirai botnet variant known as V3G4 first made its appearance in mid-summer 2022. It targets Linux-based servers and networking devices.
As per the Palo Alto Networks Unit 42’s research, this malware can be attributed to a single hacking collective. This is based on the hardcoded C2 domains containing the identical string, the same XOR decryption key, and shell script downloaders, in addition to other offensive capabilities with similar patterns.
The Mirai Variant V3G4 has already caused a severe security impact on affected systems. Once devices are left vulnerable by V3G4, these devices can be controlled by attackers and even become a part of further attack campaigns.
How does the V3G4 Mirai variant work?
Unlike earlier other Mirai variants using the same key for string encryption, the recent V3G4 variant relies on different XOR encryption keys for various scenarios. In fact, V3G4 comes with a set of default or weak login credentials that is used for brute-force attacks via Telnet and SSH network protocols and spreads to the other machines.
Then, it sets up contact with the C2 server and patiently waits for the commands to launch DDoS attacks against the targets.
In fact, V3G4 attacks start by exploiting one of the vulnerabilities seen below:
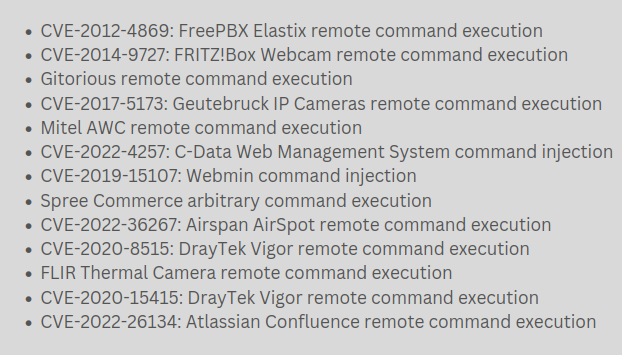
Once the target device is compromised, a Mirai-based payload is dropped on the system. This in turn tries to connect to the hardcoded C2 address.
Furthermore, the botnet tries to stop a set of processes from a hardcoded list, which includes other competing botnet malware.
V3G4 is different from other Mirai variants due to its four different XOR encryption keys rather than just one. This makes it far more difficult to reverse engineer the malware code and decode its functionalities.
Finally the compromised devices reverie their DDoS commands directly from the C2, including TCP, SYN, UDP, and HTTP flooding methods.
Changing the default password and installing the most recent security updates are the best ways, in the opinion of our experts, to protect your devices from infections similar to Mirai.
[Need assistance with a different issue? Our team is available 24/7.]
Conclusion
In summary, our Support Techs demonstrated how Mirai Variant V3G4 targets Linux systems.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.







0 Comments