The ‘RDP authentication error has occurred’ error occurs after installing the latest security updates on Windows 10 desktop.
Here at Bobcares, we have seen several such Windows-related errors as part of our Server Management Services for web hosts and online service providers.
Today we’ll take a look at the causes for this error and see the fix.
Why does the ‘RDP authentication error has occurred’ problem to arise
This RDP error mainly occurs after installing the latest security updates on Windows 10 desktop. However, these updates fix a serious vulnerability in the CredSSP protocol used for authentication on RDP servers.
But these updates are not installed on the RDP/RDS server-side, and the NLA (Network Level Authentication) is enabled for remote desktop access.
So the computer blocks the remote desktop connection to a server that uses the vulnerable version of CredSSP.
For instance, the error appears as below.
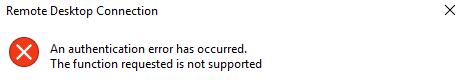
How we resolve the ‘RDP authentication error has occurred’ issue
Here are the different ways our Support Engineers follow to resolve this error.
Method 1
The best way to resolve this problem is to install the latest cumulative Windows security updates on a remote computer or RDS server.
Method 2
We try to disable the NLA (Network Level Authentication) on the RDP server side. Here are the steps for it.
If NLA is enabled on the RDP server then it means that CredSSP is used for RDP users’ pre-authentication. So, we disable the Network Level Authentication in the System Properties on the Remote tab by unchecking the options “Allow connection only from computers running Remote Desktop with Network Level Authentication (recommended)” (Windows 10 /8.1 or Windows Server 2012R2/2016). Here is a screenshot of the same.
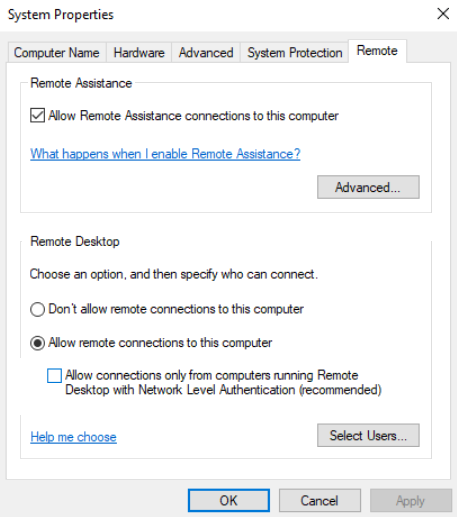
In Windows 7 (Windows Server 2008 R2), this option is called differently. On the Remote tab, we select the option “Allow connections from computers running any version of Remote Desktop (less secure)“.
We also try disabling Network Level Authentication (NLA) using the Local Group Policy editor – gpedit.msc.
We either do it by running the gpedit.msc in Windows 10 Home edition or by using the domain group policy management console – GPMC.msc.
In the policy editor we go to the section Computer Configuration >> Administrative Templates >> Windows Components >> Remote Desktop Services >> Remote Desktop Session Host >> Security, here we find and disable the policy “Require user authentication for remote connections by using Network Level Authentication“.
Also, we select the ‘RDP’ Security Layer in the “Require use of specific security layer for remote (RDP) connections” policy settings.
Finally, we update the group policies on a local computer (gpupdate / force) or reboot the desktop to apply the new RDP settings.
Method 3
We re-configure the desktops by allowing them to connect to the Remote Desktop with an unsafe version of CredSSP.
In order to do it, we change the registry parameter AllowEncryptionOracle. For that, we run the below command.
REG ADD
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters /v AllowEncryptionOracle /t REG_DWORD /d 2Or else, we change the local policy Encryption Oracle Remediation by setting its value to Vulnerable.
This is the only way to access a remote server via RDP if we can’t log in on the server locally (via the ILO, virtual machine console or cloud provider web-interface). We connect to a remote server in this mode and install the latest security updates.
After updating the server, we do disable the policy or return the value of the registry parameter AllowEncryptionOracle to 0. Here is the command that we run
REG ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters /v AllowEncryptionOracle /t REG_DWORD /d 0[Are you still stuck with authentication error? – We are here to help you]
Conclusion
In short, this error occurs after installing the latest security updates on Windows 10 desktop. Today, we saw the solution provided by our Support Engineers.




0 Comments