Google blacklists up to 6,000 websites EVERY DAY for serving malware. Almost all of these sites are classified as “compromised sites”, which means it was infected with malware without the knowledge of the site owner.
A malware infection could lead to loss in SEO ranking, and business reputation. Building back the site traffic could take weeks, if not months.
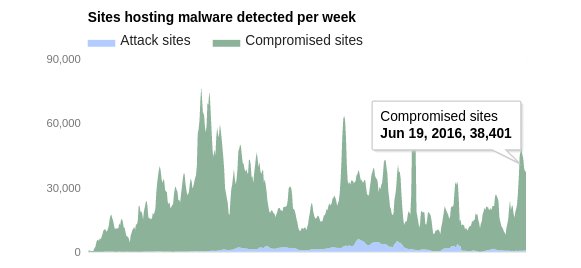
From Jun 19 – Jun 25, malware was detected in 38,401 sites. That’s 5485 sites infected per day.
In our role as Support Engineers for web hosts, we perform these four tasks to keep your server free off malware.
1. Setup file upload scanning
Malware gets into the server primarily by two means:
- Software exploits – Web application vulnerabilities like Cross Site Scripting (XSS), Remote File Inclusion (RFI), etc. enable attackers to upload malware.
- Using stolen login details – Attackers use phishing mails, brute force attacks, or drive-by-downloads to steal FTP or web application login details. It is then used to infect websites.
To counter these channels of infection, use an upload-time file scanner for Web, FTP and Web disk services.
Many FTP servers allow integration with anti-virus tools. Similarly, malware-scanning tools can be integrated with Web Application Firewalls such as ModSecurity.
However, note that, this can result in legitimate uploads to be flagged as virus. So, it is important to keep an eye on logs, and create custom rules to match your server.

ClamAV anti-virus can be integrated with ModSecurity web app firewall to detect malware uploaded via web interfaces
[ Running a hosting business doesn’t have to be hard, or costly. Get world class Hosting Support Specialists at $12.99/hour (bulk discounts available) ]
2. Configure process scanning
A “process” is a task being performed by server. For eg. if your browser asked for an image from a website, a task (aka process) is created with a unique ID to send you that image.
Typically, such user requests are completed within a few seconds. So if a user’s task is seen to run for more than 10 seconds, it’s likely to be malicious.

Long running processes that’s initiated by a user script could be malicious
Many anti-virus tools in Windows have process tracking (aka scanning) on by default. But in Linux servers, you may need to specifically install and configure process tracking using tools such as Linux Failure Daemon (LFD).
[ Use your time to build your business. We’ll take care of your customers. Hire Our Support Engineers at $12.99/hr. ]
3. Setup file scanning based on filesystem change
Scanning files during upload is a great way to snag malware, but in some servers it may not be possible to monitor all channels (such as file share, web panel upload, etc.).
In such cases, you can setup anti-virus tools to monitor changes in the filesystem, and scan all newly modified (or created) files.
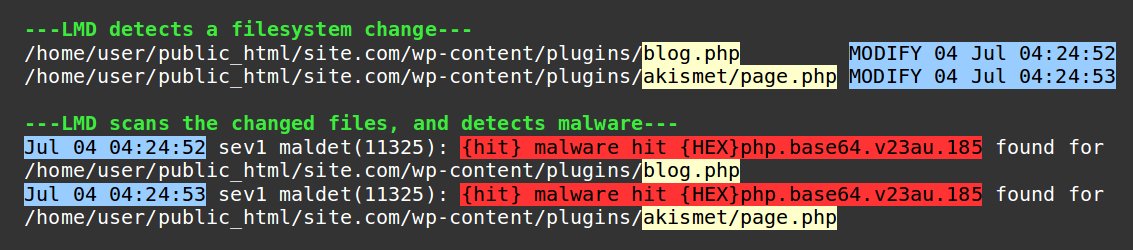
In Linux servers, filesystem changes can be monitored using a Kernel feature called inotify. Maldet (aka LMD) is one such tool that uses inotify to trigger malware scans.
[ You don’t have to lose your sleep to keep your customers happy. Our Support Engineers cover your servers and support your customers 24/7 at just $12.99/hour. ]
4. Schedule periodic full server scanning
Anti-virus databases are not always up-to-date. So, it is possible that some malware could get uploaded to the server before it’s signature was available in the anti-virus database.
So, it’s a good practice to scan the whole server for malware at least once a day.
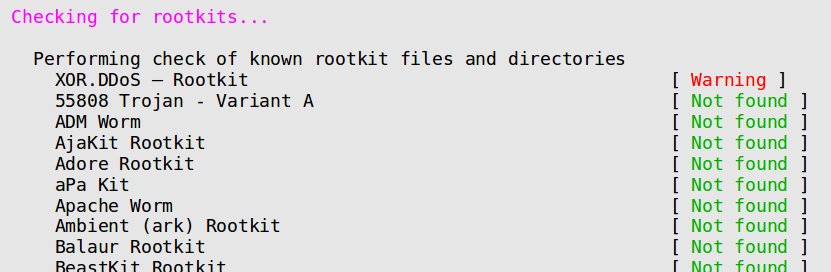
Some tools such as RkHunter, ChkRootkit and Lynis can detect administrator level compromises. Here’s a screen shot from RkHunter.
For web space scanning, you can use Maldet, ClamAV or any such other scanners.
Read : How to detect and intrusion in your server
Bonus tip – Use multiple anti-virus databases
No single provider can cover all malware that’s on the internet. So, it is best to collect malware signatures from a wide range of vendors.
There are many free malware signature databases like SaneSecurity, ScamNailer, ExtremeShock, etc. that can improve your server’s malware detection rates.
In Windows servers, use multiple anti-virus tools such as ClamWin, Malwarebytes, and Microsoft Security Essentials.
In short..
Thousands of websites get blacklisted every day due to malware infection. By following a few best practices in malware scanning, it is possible to block almost all of these infections. Today we’ve gone through the top 4 ways to setup and use anti-malware tools.
Bobcares helps online businesses of all sizes achieve world-class security and uptime, using tried and tested solutions. If you’d like to know how to make your server more reliable, we’d be happy to talk to you.




0 Comments