We may have heard about recent ransomware targeting ESXi servers. In this article, we’ll look into the details of the attack. Bobcares offers 24/7 Server Support as a part of our Server Management Services.
Ransomware targeting ESXi servers – A new wave of attacks
The ESXi servers are currently the target of a wave of attacks. The attack started by taking advantage of a two-year-old remote code execution vulnerability in the VMware ESXi servers. The security weakness, identifiable as CVE-2021-21974, results from a heap overflow problem, in the OpenSLP service. Unauthenticated threat actors exploit it in low-complexity attacks.
As of right now, ESXi hypervisors in versions 6.x and before 6.7 are the target systems. On infected ESXi hosts, the ransomware encrypts files with the .vmxf, .vmx, .vmdk, .vmsd, and .nvram extensions and generates a .args file with metadata for each encrypted file.
We may sometimes see ransom notes named “ransom.html”, “How to Restore Your Files.html”, or plaintext files on the affected systems. Although the attacker may claim to have data taken, this is not necessarily the case. For instance, in a similar incident, an infected machine had more than 500 GB of data but only 2 Mbps of normal daily usage. Analyzing traffic statistics over the previous 90 days reveals no proof of outbound data movement.
The ESXiArgs ransomware campaign has exposed over 3,200 VMware ESXi servers globally.
How the attack is launched?
When a server compromises, the file such as encrypt, encrypt.sh, public.pem, motd, and index.html will be in the /tmp folder. The public RSA key file, the file to encrypt, the data chunks without encryption, the size of an encryption block, and the file size are all command line arguments to launch the encryptor when a shell script file runs it.
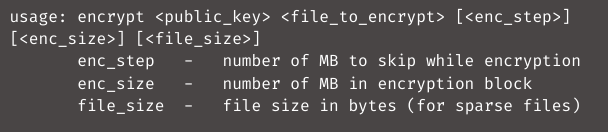
The encrypt.sh shell script, which serves as the attack’s logic starts this encryptor. When the script starts, it will run the below code to change the strings ‘.vmdk’ and ‘.vswp’ in the ESXi virtual machine’s configuration files (.vmx) to ‘1.vmdk’ and ‘1.vswp,’ respectively. The script then kills (kill -9) any processes that include the string “vmx” to force-terminate all operating virtual machines.
The script will use the below code to get a list of ESXi volumes:
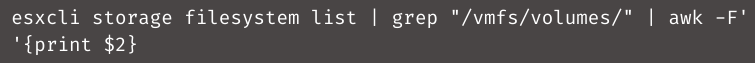
These volumes will be searched by the script for files with the below extensions:
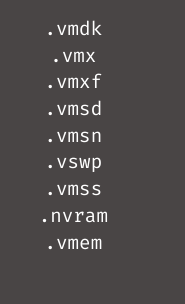
The script will produce a [file_name].args file in the same folder for each file it finds, and it will include the size of the file, the computed size step “1”. The script will then use the ‘encrypt’ to encrypt the files using the specific parameters. After encryption, the script will replace the server’s motd file and the ESXi index.html file with the ransom notes.
Finally, the script conducts some cleaning, deleting several lines from the following files, and removing what looks to be a backdoor to /store/packages/vmtools.py:
In order to ensure the deletion, all admins should check for the presence of the vmtools.py file. If we find it again, remove the file right away to avoid the attacks. In order to update the settings in the /bootbank/state.tgz file and to launch SSH, the script executes /sbin/auto-backup.sh at the end.
[Looking for a solution to another query? We’re available 24/7.]
Conclusion
The article briefly introduces us to the recent ransomware attacks targeting ESXi servers, along with showing how the attack is carried out.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.




0 Comments