Learn more about integrating Cloudflare Nginx Fail2ban. Our Cloudflare Support team is here to help you with your questions and concerns.
Cloudflare Nginx Fail2ban Integration
Tools like Fail2Ban and Cloudflare offer a strong defense against malicious attacks.
By combining their powers, particularly in a Linux environment, we can boost our website’s defenses and safeguard against threats.
Today, we are going to take a closer look at integrating Fail2Ban with Cloudflare.
Configuring Fail2Ban for Cloudflare Integration
Before we begin, we have to set up Fail2Ban using linuxserver’s swag container. With Fail2Ban in place, let’s move on to the Cloudflare integration:
- To begin with, go to the appdata location and locate the action.d folder (e.g., appdata/swag/fail2ban/action.d).
- Then, create a new file named cloudflare-apiv4.conf and add configuration settings to it.
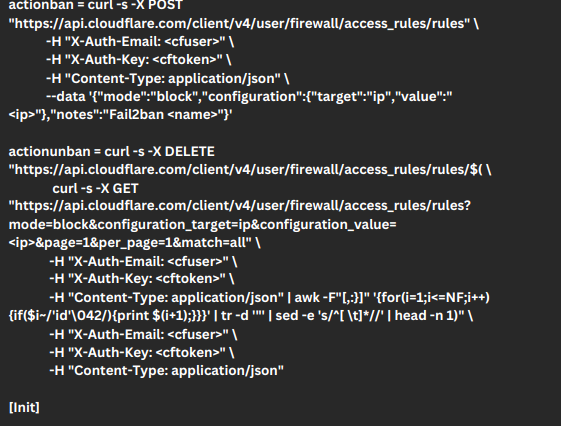
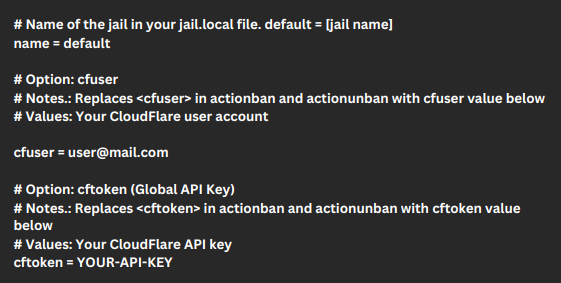
At the end of the config file we have to add our cloudflare email on the “cfuser” line and add the Cloudflare token on the “cftoken” line.
How to Update the Jail Configuration
- First, access the jail.local file located in the fail2ban directory within appdata.
- Then, add or update jails with the action set to cloudflare-apiv4. We have to mention the actions to be taken when banning an IP address.
- Next, we have to customize the ban duration and ignore IP settings as per our needs.
If we are managing multiple sites on Cloudflare, we can modify the actionban and actionunban URLs to specify the target site’s zone ID.
Additionally, we can prevent accidental self-bans by adding our WAN IP to the Cloudflare whitelist through the Firewall settings.
Nginx Configuration
To ensure Fail2Ban bans the actual visitor IP and not Cloudflare’s CDN IP, we have to configure Nginx to record the original visitor IP.
So, add the necessary set_real_ip_from and real_ip_header directives to the nginx.conf or include file.
We can also use scripts to automatically update the Cloudflare IP list used by Nginx for IP resolution. Inf act, we can stay up-to-date with Cloudflare’s IP changes by scheduling the script to run periodically.
Alternatively, we can integrate the ngx_http_realip_module to record the original visitor IP instead of Cloudflare’s.
[Need assistance with a different issue? Our team is available 24/7.]
Conclusion
In brief, our Support Experts introduced us to Cloudflare Nginx Fail2ban integration.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.




0 Comments