Secure website transaction involves a key exchange between the server and the browser. And, when an attacker is ever able to get hold of this key, they can decrypt your SSL session. Thus, the whole process fails.
Perfect Forward Secrecy (PFS) eliminate the use of such key in SSL communications. However, enabling Apache Forward Secrecy may not look easy for many server owners.
At Bobcares, we often get requests to tweak Apache settings as part of our Server Administration Services.
Today, we’ll see how our Support Engineers setup Apache Forward Secrecy and fix related errors.
Why to use Perfect Forward Secrecy ?
Before going deeper, let’s first get to know more about Perfect Forward Secrecy.
In normal SSL communication, the primary step involves the creation of a session key that matches browser and server capabilities. Usually, this session key uses a popular key exchange mechanism called RSA.
This RSA process creates a link between the server’s key pair and the session key created for each unique secure session. Unfortunately, it is possible to decrypt data by any one who has access to the server’s private key. Thus, attackers primarily focus on snatching these details to get hold of secure information from SSL session.
Perfect Forward Secrecy (PFS) uses the Elliptic Curve Diffie-Hellman (ECDHE) key exchange method. In this method, the session keys are not linked to the server’s key pair. Thus, it eliminates the possibility of decrypting SSL session using server’s private key.
Naturally, it’s a common security measure that our Dedicated Engineers often offer to Apache web server owners.
Steps to enable Apache Forward Secrecy
We now know the benefits of Forward Secrecy. It’s time to check how our Support Engineers enable it in Apache Web server.
1. Prerequisites set up
As part of enabling Forward Secrecy, we first login to the server and ensure that the server satisfies the following requirements.
- OpenSSL 1.0.1c+
- Apache 2.4x
On servers with lower versions, we first do an upgrade, so that Apache web server and SSL/TLS library supports the new key exchange process.
2. SSL Protocol Configuration
Secondly, we edit the SSL configuration of the website. To get the complete list of SSL websites, we execute the command:
grep -i -r "SSLEngine" /etc/apache
We then edit the configuration of the particular domain and add the following parameters.
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1 SSLHonorCipherOrder on SSLCipherSuite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH+aRSA+RC4 EECDH EDH+aRSA RC4 !aNULL !eNULL !LOW !3DES !MD5 !EXP !PSK !SRP !DSS !RC4"
Here, these values helps to avoid timing attacks. Again, from our experience, we see that faster ECDHE suites greatly increase the web server performance. However, the SSLCipherSuite parameter may affect the browser support too. Therefore, our Support Engineers set it after considering the server requirements too.
3. Restarting Apache
Final step for enabling Apache forward secrecy is to restart the web server. To make the new configuration work, we execute:
apachectl -k restart
Now, checking the website in SSL checkers will show Apache Forward Secrecy. The results for a website will look as shown.
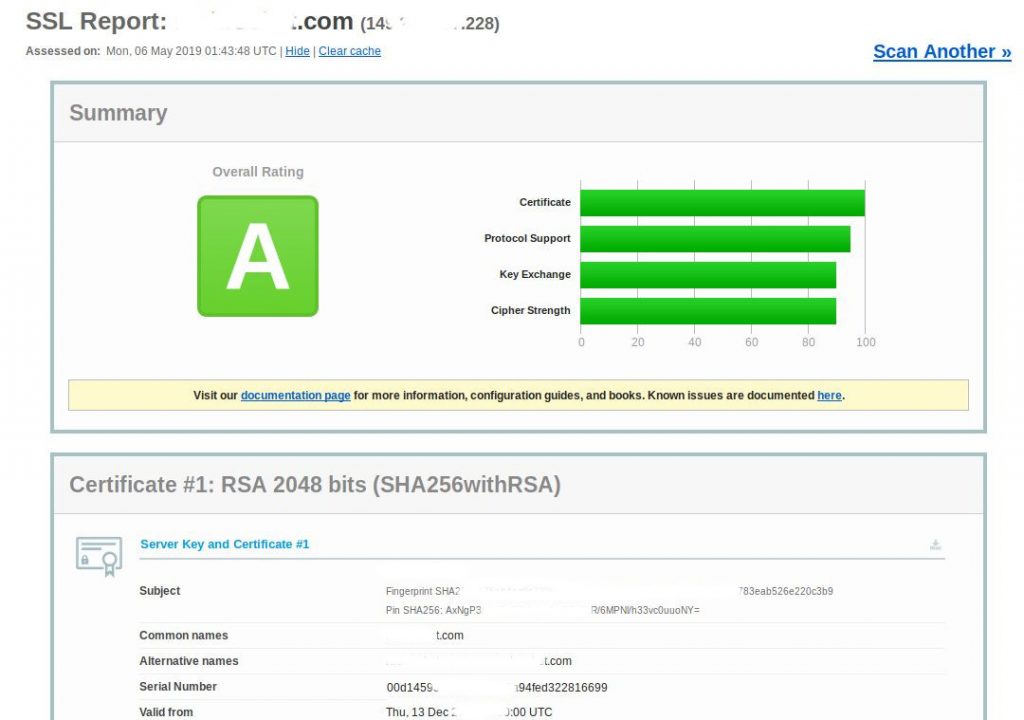
Common errors and fixes in Forward Secrecy
From our experience in managing Apache servers, we often see errors after enabling Forward Secrecy. Let’s take a look at them.
1. Limited browser support
A common problem noted after enabling Forward Secrecy is lack of old browser support. Basically, when you alter the Ciphersuite settings in the Apache configuration, it stop supporting browsers like Internet Explorer6
Although, discontinuing old and outdated browser support is the best security practice, some customers may still need it. In such cases, our Security Experts edit the Apache configuration for selected websites, keeping additional security checks in place. This would include limiting the website access to selected IP addresses.
2. Incorrect SSL report
At times, configuration errors can also create issues with Forward Secrecy.
Recently, one of our customers was getting a bad report for his website even after enabling Forward Secrecy. On a detailed check, we could see that there was problem in picking ciphers in the correct order.
Therefore, our Support Engineers added the following setting to the website settings.
SSLHonorCipherOrder on
And, that solved the problem for the customer.
[Having trouble with enabling Apache Forward Secrecy? We can fix it right away.]
Conclusion
In short, Apache Forward Secrecy helps to enhance security of SSL communications. Today, we saw the benefits of enabling it and how our Dedicated Engineers set up Forward Secrecy for websites and fix related errors.







Hello,
Everything looks good except SSLProtocol all -SSLv2 -SSLv3. To make it A+ in SSLlab test disallow TLSv1 and TLSv1.1 too as they are obsolete too and have weaker Cipher supports to provoke attacks.
Hello Subhomay,
Yes, since January 2020, SSL/TLS servers that use TLS 1.1 and TLS 1.0 get a lower grade in the SSL test. Updated the content. Thank you for the inputs.