Let us take a closer look at Cloudflare and intermediate certificate with the support of our server management support services at Bobcares.
Intermediate certificate
Most certificates of authority, or CAs, do not immediately sign the SSL certificates they give to clients with their root certificates. They instead utilize intermediate certificates.
The chain of intermediate certificates can be of any length, and it can convey trust from the root to the final certificate by the web server. Even more difficult, one intermediate certificate may have many parent certificates that attest to its authenticity.
Bundle methodologies
After sending an SSL certificate to the Cloudflare edge, it may add to intermediate and root certificates to help the user agent identify a chain to a publicly trusted root. By selecting a bundling approach, we can regulate the packaging of the Certificates.
Compatible
Compatible mode is the default, and it completes the chain with common and widely circulated Cloudflare intermediate certificates, ensuring that the finished bundle is compatible with as many customers as feasible.
Modern
Modern efforts to make the chain as efficient as feasible, frequently through the use of newer or fewer Cloudflare intermediary certificates.
User-defined
The user-defined option allows to paste the certificate chain and display it to customers. Following the leaf, and indicate any intermediates to employ it. Use this option when using a self-signed certificate.
The length of the Cloudflare intermediate certificates in a chain might vary, but every chain has one leaf and one root.
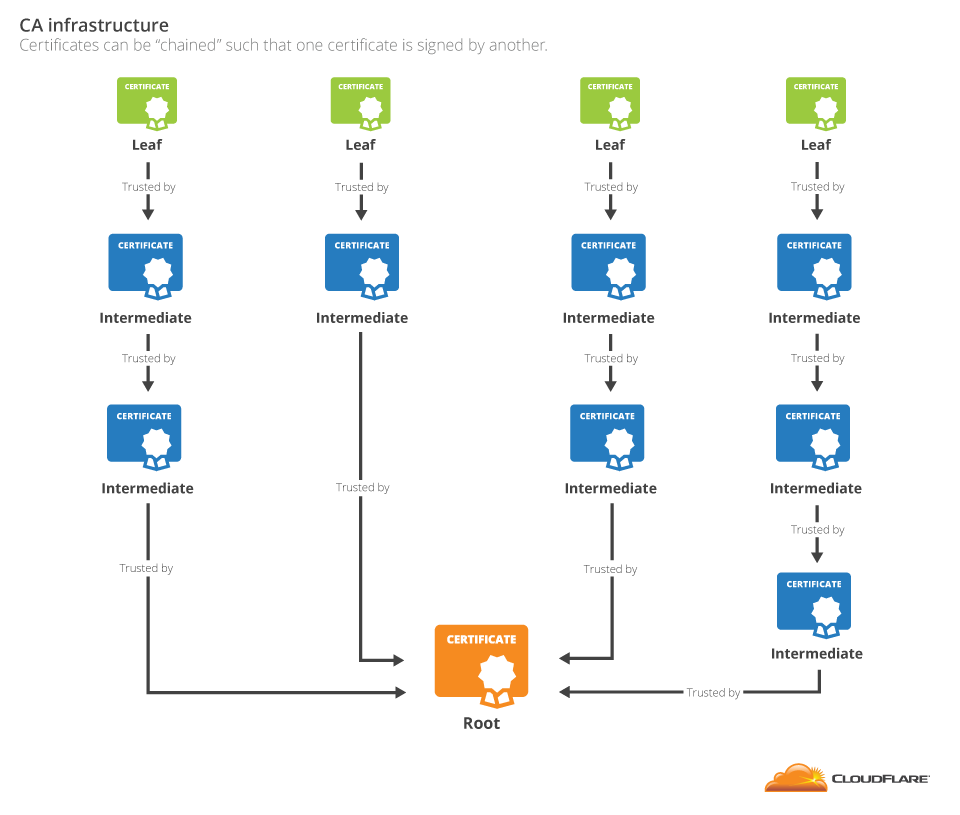
Unfortunately, there is a catch for the owner of the leaf certificate: often, simply displaying the leaf certificate to the browser is insufficient.
As the browser won’t recognize the intermediate certificates, the website must provide them with the leaf certificate. A certificate bundle is a collection of certificates that the browser needs to validate a certificate.
It should contain all the certificates in the chain up to the first certificate known to the browser. In the case of the CloudFlare website, this bundle contains both the cloudflare.com certificate and the GlobalSign G2 intermediate.
Cloudflare SSL was created to facilitate certificate bundling.
How CFSSL Makes Certificate Bundling Easier?
CFSSL or Cloudflare SSL can generate an Intermediate certificate bundle after running a website (or possibly another TLS-based application) and needing to install a certificate. Begin by issuing the following command:
$ cfssl bundle -cert mycert.crt
This will generate a JSON blob containing the chain of certificates as well as pertinent information retrieved from it. In addition, anybody may operate the CFSSL service, which replies to queries through a JSON API:
$ cfssl serve
This command starts a localhost HTTP service that accepts requests. To bundle using this API, make a POST call to http://localhost:8888/api/v1/cfssl/bundle with a JSON request like:
{
"certificate": <PEM-encoded certificate>
}
CloudFlare’s SSL service will respond with a JSON response of the following format:
{
"result": {<certificate bundle JSON>},
"success": true,
"errors": [],
"messages": [],
}
To construct a certificate bundle with CFSSL, we must first determine whose certificates are trusted by the browsers to whom we intend to show information. This is normally straightforward in a controlled corporate environment because every browser is set up with the same settings; however, it gets more complex when constructing a web bundle.
[Need assistance with similar queries? We are here to help]
Conclusion
To sum we have now seen more on the Cloudflare intermediate certificate with the support of our tech support team.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.





0 Comments