Google cloud services give flexibility and redundancy to cloud bases websites.
However, website management often needs remote access. And, one of the quickest ways is to set up Google cloud compute engine ssh access.
Google Cloud services allow access through the public web or through a dedicated network connection.
At Bobcares, we often get consultation requests on the best GCP connectivity method as part of our Google Cloud Platform Support services.
Today, we’ll see how our Cloud Engineers make instances accessible over SSH.
Why we need remote access on GCP?
Just like any other server, managing websites need remote access to Google Cloud Platform too. Additionally, managing files via ssh can save a lot of time. SSH is a popular network protocol that provides encrypted data communication between two computers.
The remote access to Google Cloud servers can vary based on the type of computer from which the user connects. For instance, when you are connecting from a Windows machine, it involves using third-party tools like PUTTY.
Fortunately, Linux machines come with native SSH support, which makes things easier.
How to set up Google cloud compute engine ssh access?
It’s time now to see how to access the Google cloud compute engine using ssh. We’ll quickly have a look at the top 3 ways that our Cloud Engineers use to set up the access.
1. Using SSH keys
One of the simplest and quickest ways for instance access is using SSH keys. In this method, we first need to generate an SSH key pair to connect securely to the virtual machine.
On the computer from which we are connecting, we generate the public and private key using:
ssh-keygen -t rsa
We just follow the on-screen instructions regarding key storage location, passphrase, etc. Finally, there will be a private key at ~/.ssh/id_rsa and a public key ~/.ssh/id_rsa.pub.
The next step is to copy the public key to the Google Cloud instance. We then access the Security tab from GCP and add the SSH key field in Google Cloud and hit Create button.
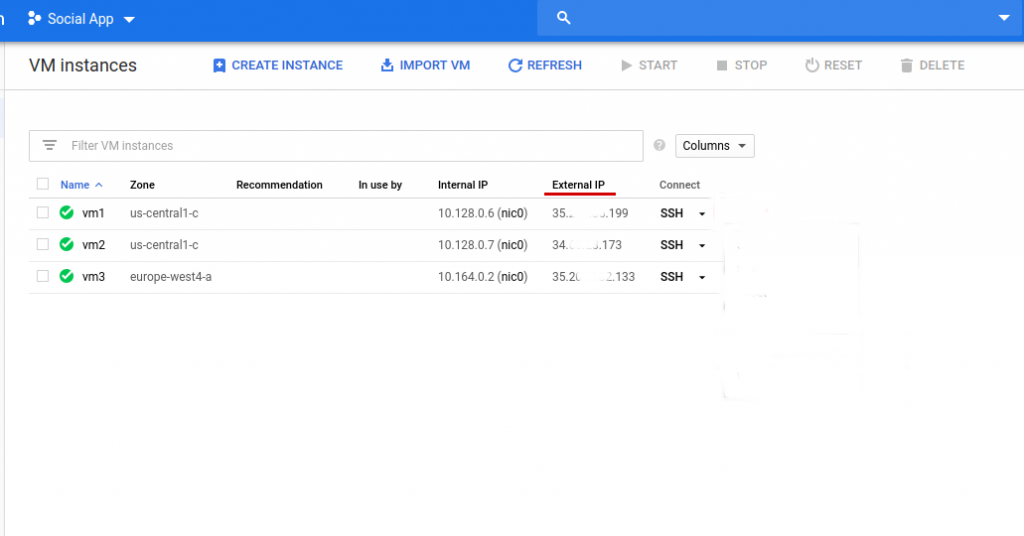
That’s it. Now we can use the External IP of the virtual machine for SSH access.
In google cloud, unless there is static IP allotted for your instance, public IP will change after shutdown. Therefore, we always check the external IP address from the GCP. The interface shows the virtual machine details including IP address.
2. Accessing from Gcloud tool
To access the Google cloud compute engine, we can also use the gcloud compute command-line tool.
Here, first we need to install and setup the latest version of gcloud compute using Google Cloud SDK. It contains tools like gcloud, gsutil, etc. that helps to easily manage resources and applications hosted on Google Cloud Platform.
We download the latest stable version of the google-cloud-sdk-xx package. Then we extract and install the package. As the next step, we run gcloud init to initialize the SDK.
To connect to the Google cloud instance, we use:
gcloud compute ssh instance_name --zone us-central1-a
Google Cloud Platform Console
Similarly, Google allows instance access via browser too. To access the server, we access the GCP Console and go to the VM Instances page.
In the list of virtual machine instances, we click the SSH option in the row of the instance that we want to connect to.
This connects to the instance and shows up as below.
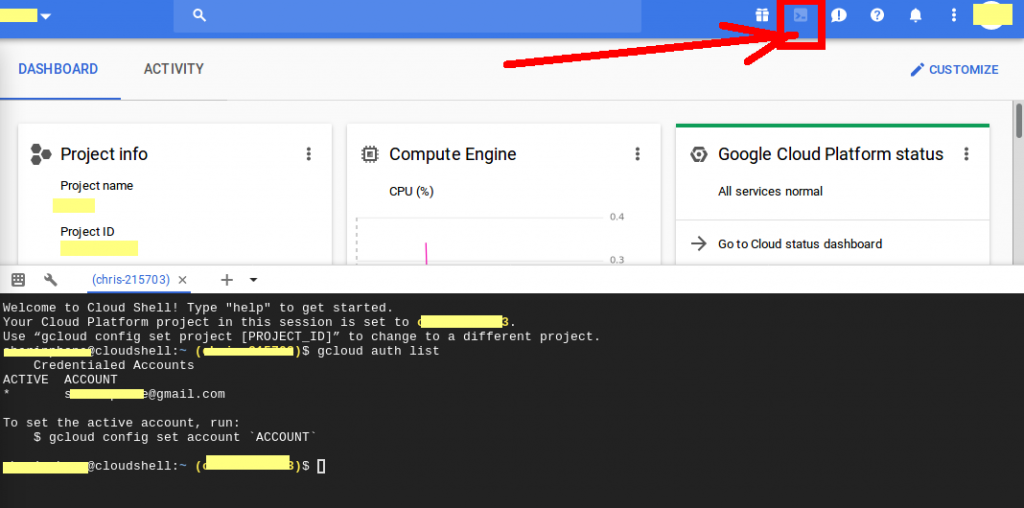
Here, we use the terminal to run commands on the Linux instance. For security reasons, after finishing the work, we just disconnect from the instance by using the exit command.
Common errors with access
Unfortunately, Google cloud compute engine ssh access often result in connectivity errors. We’ll now see how our Dedicated Engineers troubleshoot and fix them.
1. Permission problems
A rather common reason behind the connectivity errors will be the wrong permissions of the SSH key file.
Recently, a customer reported this error while connecting to his instance.
Permission denied (publickey,gssapi-keyex,gssapi-with-mic). ERROR: (gcloud.compute.ssh) [/usr/bin/ssh] exited with return code [255].
On checking, we found that the compute instance had the entry PermitRootLogin no in its SSHD configuration. And the user was trying to log in as root. Therefore, our Cloud Engineers suggested the customer use a login name other than root.
Again, a similar error pops up when someone else in the same Google cloud project set the per-instance metadata for ssh keys. This overrides the project-wide metadata and SSH access fails.
2. Firewall misconfiguration
In general, the Google Cloud Platform VPC network must have one or more firewall rules that allow SSH connections on port 22. Again, the firewall rules must allow SSH connections for the IP ranges or specific IP addresses from which users try to connect.
The exact firewall rules in one of the Google cloud instance appear as:
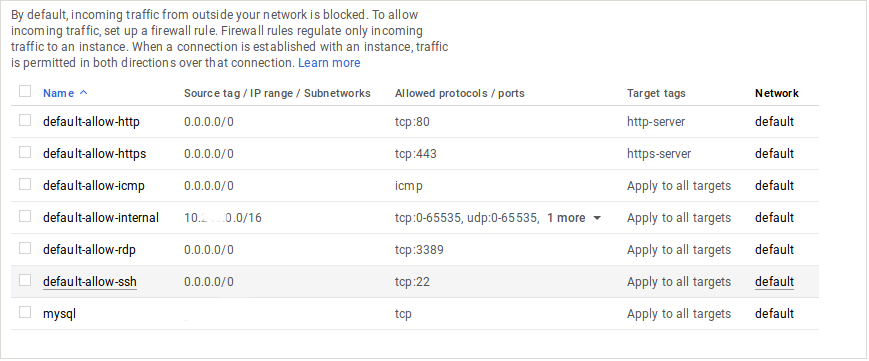
If SSH listens on another port, our Cloud Engineers allow the custom port in the firewall as well.
Conclusion
In short, the Google cloud compute engine ssh connection can be set up mainly in 3 ways. Today, we saw how our Cloud Engineers setup access and fix top errors related to it.







0 Comments