Have you been confused about how to harden the SSH server on Ubuntu?
As a part of our Server Management Services, we help our customers to secure their SSH servers by performing SSH hardening.
Server SSH hardening improves the level of protection and the server becomes less vulnerable to hacking.
In this Guide, we ‘re presenting the best SSH hardening tips from our realistic experience.
Best ways to Harden SSH Server on Ubuntu
Vulnerabilities in the Secure Shell (SSH) protocol can be minimized via SSH hardening.
Why is SSH hardening so Important?
If the SSH service is not sufficiently secure, the chance of hacking would increase exponentially. If you don’t follow best practices to harden the SSH server properly, the server can still be targeted and broken.
Here, let’s see how our Support Engineers harden the SSH server on Ubuntu.
1. Switch Default SSH Port
The default port of SSH service is 22. The majority of hackers who are looking for OpenSSH launches brute force attacks against the default SSH port. Consequently, the load on the server may increases which leads to the server down.
However, the Ubuntu server allows customizing SSH port for the server. This protects the server against automated attacks.
How to change the port on the Ubuntu server
1. Firstly, we connect to the server via SSH.
2. Then, we open the configuration file /etc/ssh/sshd_config/ and disable the line that begins with Port 22. After that, we, add a new port line and specify the desired port to bind SSH.

3. After making the above changes, we restart the SSH daemon for the changes to get reflected.
2. Disable Root Login
The root user has full privileges on Linux server distributions. The hackers attempt to break the password of root user with brute force attacks. If the server gets compromised, the hacker can access all the data.
So, the server security increases when disabling the root user. To disable the root user, we follow the below steps,
1. Initially, we SSH to the server as root.
2. Then, we open SSH main configuration file, /etc/ssh/sshd_config, and change PermitRootLogin yes to PermitRootLogin no.
# Authentication: PermitRootLogin no MaxAuthTries 6
3. Finally, we restart the SSH service.
3. Limit max authentication attempts
A brute force attack is a common hacking method that attempts to crack a password or username. The effective way to protect the server from brute-force attacks is to limit the number of attempts against the user.
So, we tweak the MaxAuthTries setting in the SSH main configuration file, /etc/ssh/sshd_config,
MaxAuthTries 6 MaxSessions 10
4. Disable Password-Based Logins
SSH keys authentication provides an additional security layer that disables the use of the server password. So, this type of authentication ensures that passwords need not be sent over the network, and SSH keys symbolize the passwords instead.
Also, this is another way to keep the server safe from brute-force attacks.
Before enabling SSH keys authentication, we check if SSH key-based authentication is working for the account that has access to the server.
Therefore, we do the below steps to enable SSH keys authentication:
1. We SSH to the server as root.
2. Then, use a text editor to open the sshd_config file.
vi /etc/ssh/sshd_config
3. Look for the line that says PasswordAuthentication and change to PasswordAuthentication no.
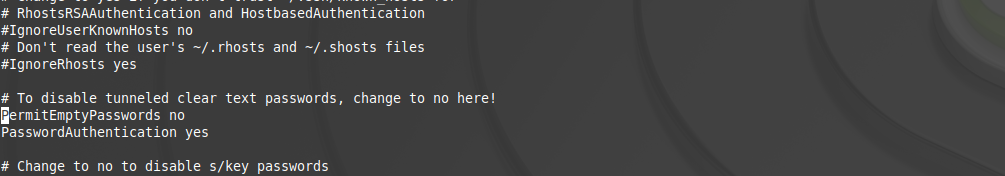
4. Finally, we save the changes and restart the SSH service to apply the changes.
5. Block SSH Access Using IPtables
IPtables is a very powerful security tool for monitoring/filtering incoming and outgoing traffic to the server. Based on the defined rules IPtables block unwanted traffic. It also protects against Denial of Service attacks (DoS).
So, we will set firewall rules to restrict the incoming SSH traffic by accessing the server log.
[Need help with SSH hardening on Ubuntu – Our Support Engineers will help you.]
Conclusion
In short, SSH hardening improves the level of protection and the server becomes less vulnerable to hacking. Today, we saw 5 best ways to Harden SSH Server on Ubuntu and how our Support Engineers harden the SSH server.







0 Comments