When you hear the term “hacker”, you picture a computer whiz kid in a dark room, typing away mysterious code on a green lit computer – or that’s what the popular image is.
The depiction of a hacker may change, but one thing is common – They all attack from a remote location over the network. No one pictures a hacker physically accessing your server to steal the data.

Unless you’re thinking of Tom Cruise in Mission Impossible, of course
Now, assuming that you are not targeted by a super secret spy agency, virtually 100% of attacks on your server will be through the network – Many of which can be blocked by a well configured firewall.
Read : A complete guide on how to secure a server
Today, we’ll take a look at how to configure firewall in Linux servers.
Which Linux firewall should you choose?
A quick Google search will give you a long list of firewalls for Linux. You’d come across IPTables, Netfilter, Shorewall, Endian, CSF, APF, and more.
In reality, the de-facto firewall in Linux is IPTables (aka Netfilter). All others are built on top of it with varying degrees of user friendly configuration settings.

IPTables is the wine packaged in different bottles like Endian, Shorewall, etc.
It really doesn’t matter which one you choose, as long as you know what to look out for. This post is about what are the common threats, and how to mitigate them.
So, without further ado, let’s get to it.
For as low as
$74.99/server/mo
Get full spectrum infrastructure management services – including setup, monitoring & maintenance.
Never again face a critical business downtime. We keep your servers secured, optimized and updated at all times. Our engineers monitor your servers 24/7 and fix issues before it can affect your customers.
1. Make the firewall Stateful
When a new “packet” of data reaches a server, it can be safely let in, if it is part of a recognized user session. Many attacks forge network packets to look as if it is part of an established session. These attacks can be blocked by making the firewall stateful.
When IPTables is used in stateful mode, it can categorize data packets that belong to “known” and “unknown” sessions. Then stricter filtering rules can be applied on “unknown” packets.
A Linux Kernel module called “ip_conntrack” should be loaded to make IPTables stateful.

Loading the module is the first step. Firewall rules need to be modified to use stateful connections
2. Close all ports – Open only what you need
Many malware such as Bots or RATs (Remote Access Trojans) open back door access to the server through random ports. Attackers can then issue commands via these ports to initiate outbound DDoS, spam campaigns, etc.
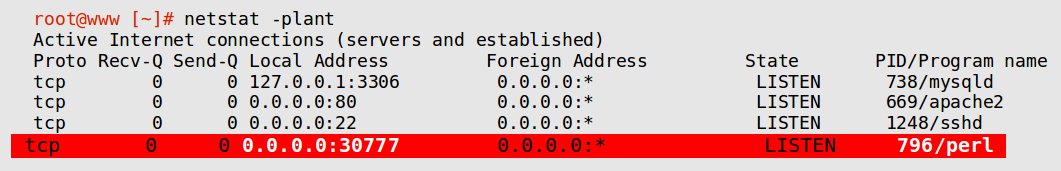
A malware with process name “perl” is listening for commands at a non-standard port “30777”. A strict firewall could have blocked this.
So, configure the firewall to DROP all connections by default, and then open ONLY the ports you need (like Apache (80), SMTP (25), etc.).
3. Block connections from bogus IP addresses
It is quite easy to find the location of an attacker with their IP address. So, hiding the IP address is a fundamental precaution taken by all hackers. This is called as IP spoofing.
IP spoofing can be difficult to detect in most cases, but in some cases, attackers use invalid public IP addresses.
For eg. IPs of the range 192.168.xxx.xxx is reserved for private communication (like LAN). So, if an internet connection comes with a “192.168.XXX.XXX” source address, it’s very likely to be spoofed.
Data packets from known invalid IPs are called Martian packets or Bogons
IPTables can be configured to block connections from such bogus IP addresses. The full list of reserved IP addresses can be obtained from reputed sources like Team Cymru. Here’s the IPv4 list and IPv6 list.
Note that the list keeps changing, and you need to update the firewall rules frequently. Alternatively, you can use a IPTables manager like CSF or APF to get this automatically done for you.
Read : How to setup CSF/LFD firewall in Linux servers
For as low as
$74.99/server/mo
Get full spectrum infrastructure management services – including setup, monitoring & maintenance.
Never again face a critical business downtime. We keep your servers secured, optimized and updated at all times. Our engineers monitor your servers 24/7 and fix issues before it can affect your customers.
4. Detect network scans and block source IPs
Much like how spies are used to find weaknesses in enemy defenses, hackers scan your network interfaces to detect vulnerabilities or open ports. Here are a few tips to block such scans.
-
Block IPs that try SYN / Connect scans on closed ports
The simplest scan is to try opening a connection on all ports in a server. The attacker can use a full connection (Connect) or a half-connection (SYN). If the server responds with an RST signal, the attacker will know the port is closed. If not, they’ll know that it is open.
So, setup the firewall to log all connection drops at closed ports. Then configure a tool such as CSF or PortSentry to monitor port blocks and black list the IPs that resulted in multiple connection failures.
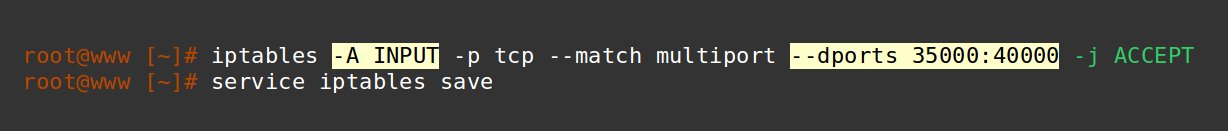
Legitimate IPs are often blocked in servers enabled with Passive FTP. Allow connections to passive FTP port range like this.
-
Drop TCP FIN, Null, XMas scans
Applications use a “FIN” signal to terminate a connection. So hackers figured out that if a “FIN” signal is sent to a closed port, it’s not a connection attempt, and won’t be detected by a firewall.
But if the server responds with an “RST” signal, the attacker will know that the port is open. It’s a stealthier way than SYN or Connect methods to scan a server.
Two variations of this kind of scan is the “Null packet” scan and “Xmas packet” scan. Here’s how it can be blocked in IPTables:
---Drop NULL packets--- root@www [~]# iptables -A INPUT -p tcp --tcp-flags ALL NONE -j DROP ---Drop Xmas packets--- root@www [~]# iptables -A INPUT -p tcp --tcp-flags SYN,FIN SYN,FIN -j DROP ---Drop TCP FIN scans--- root@www [~]# iptables -A INPUT -p tcp --tcp-flags FIN,ACK FIN -j DROP
Note: These rules don’t log the drops. Logging needs to be configured separately.
-
Block Idle scans
Probably one of the stealthiest ways to scan is to connect to a server disguised as a trusted IP.
Let’s say, server A trusts allows connections from server B. An attacker sends a connect request to server A with the IP disguised as server B. Now, by observing how server B behaves, the attacker can figure out if server A’s port is open. This is called Idle scanning.
To protect against this, you should enable Stateful Packet Inspection and block external connections from known internal IPs (IP spoofing), as explained above.
For as low as
$74.99/server/mo
Get full spectrum infrastructure management services – including setup, monitoring & maintenance.
Never again face a critical business downtime. We keep your servers secured, optimized and updated at all times. Our engineers monitor your servers 24/7 and fix issues before it can affect your customers.
5. Harden the server against DoS/DDoS attacks
Your server can take care of only a limited number of connections at a time. Attackers exploit this limitation by opening thousands of connection requests, thereby effectively blocking out valid connections. This is called a Denial of Service attack.
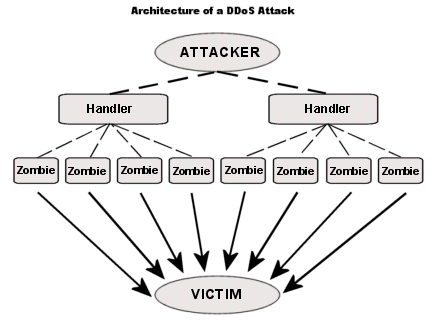
Attackers use infected “Zombie” computers to simultaneously connect to the victim server.
Here are a few ways in which you can configure your firewall to block DoS attacks
-
-
Block SYN flooding
A SYN signal is a server’s way of saying “hello”. The trouble is that, a server keeps the connection open until it hears a “hello” back so as to track the user session.
Attackers exploit this feature, and send several thousand SYN signals to the server, and never respond back. The server keeps these connections open, causing legitimate users from timing out.
To combat this, Linux uses a feature called SYN cookies. If this is enabled, the server doesn’t wait for a return “hello”. Instead it uses a connection ID to track a session.
SYN cookies should be enabled in the kernel using the sysctl command:
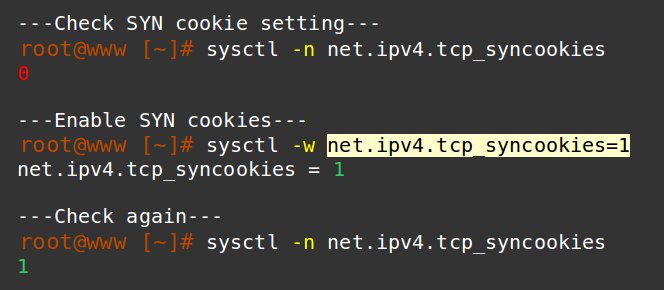
To make the changes permanent, add “net.ipv4.tcp_syncookies = 1” in /etc/sysctl.conf
-
Protect against ICMP PING flood and Smurf attacks
Ping is a tool that’s used to debug network issues. It uses ICMP protocol, and works by analyzing the “echo reply” of a “hello” sent to a server.
Attackers disguise their IP as the victim’s IP, and send ping requests to hundreds of computers on the internet. They respond “back” to the victim, causing the victim machine to shut down.

Ping floods and Smurf attacks saturate the network and block valid connections
To solve this, ICMP should be blocked by default, and be opened only to trusted servers. You can also rate limit ICMP replies to a reasonable limit (like 1 per second). You can do this by:
root@www [~]# iptables -A INPUT -p icmp -m icmp --icmp-type address-mask-request -j DROP root@www [~]# iptables -A INPUT -p icmp -m icmp --icmp-type timestamp-request -j DROP root@www [~]# iptables -A INPUT -p icmp -m icmp -m limit --limit 1/second -j ACCEPT
Note : Server troubleshooting can be affected by this rule. So, use these rules judiciously.
-
Drop fragmented packets
When sending any data, the operating system breaks it down to small pieces, which is re-assembled at the destination. This is called “fragmentation”. A serial number is used to re-assemble the data.
Attackers exploit this feature to send thousands of fragmented data bits that contain nonsensical serial numbers that cannot be assembled. It quickly exhausts server resources.
To block these attacks, block fragments that are not part of an established session.
root@www [~]# iptables -A INPUT -f -j DROP
Note : Stateful Packet Inspection must be enabled for this to work reliably
-
Setup connection limit for all services
In real life, one browser wont open more than 50 simultaneous connections to a web server. Anything more that that is likely to be a Denial of Service attack.
So, it’s a good practice to limit the number of connections that can be made from a single IP.
You can do it for port 80 by:
root@www [~]# iptables -A INPUT -p tcp --syn --dport 80 -m connlimit --connlimit-above 50 -j REJECT --reject-with tcp-reset
Note : The number of simultaneous connections is dependent on your web application. Use this judiciously
Use similar settings for other services as well.
-

This rate limit uses a kernel module called “xt_connlimit”. Load it as shown here.
-
Block port flooding
If you run many services (like mail, web, DNS, etc.) on the same physical server, a DoS attack on one of the services will bring down all others.
So, it is important to limit the number of connections that can be allowed into one port to contain the damage caused by such an attack.
Here’s how connections to port 80 (web server) can be limited to 1000/min.
root@www [~]# iptables -I INPUT -p tcp -m tcp --dport 80 -m state NEW,ESTABLISHED -m recent --set -j ACCEPT root@www [~]# iptables -I INPUT -p tcp -m tcp --dport 80 -m state --state NEW -m recent --update --seconds 60 --hitcount 1000 -j DROP root@www [~]# iptables -A OUTPUT -p tcp -m tcp --sport 80 -m state --state ESTABLISHED -j ACCEPT
Note : These rules may need to be customized for your server
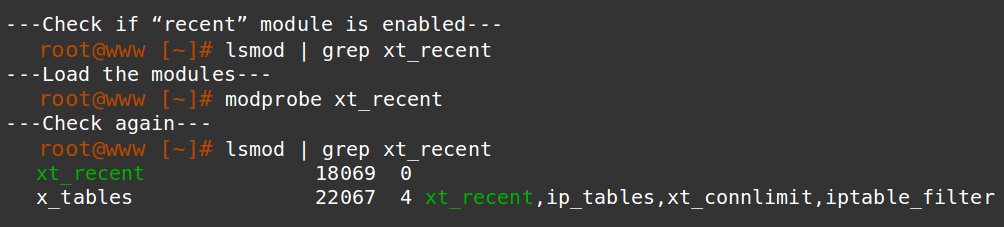
For this block to work, “xt_recent” module should be loaded in the kernel.
For as low as
$74.99/server/mo
Get full spectrum infrastructure management services – including setup, monitoring & maintenance.
Never again face a critical business downtime. We keep your servers secured, optimized and updated at all times. Our engineers monitor your servers 24/7 and fix issues before it can affect your customers.
6. Block abnormal packets
What we’ve discussed till now is to block connections based on known ways in which network packets can be forged.
A better way is to block any network packet that does not conform to a normal pattern. A normal network packet falls into one of these:
- SYN signal (flag) followed by SYN ACK, and then an ACK flag.
- All packets except the first will have an ACK flag. They might also have PSH or URG during a conversation.
- FIN ACK followed by FIN is used to close a connection. PSH FIN ACK is also used.
- RST or RST ACK is used to terminate a connection.
So, if the firewall is configured to strictly enforce this rule, a good deal of attacks can be blocked before it reaches any application.
However, this is an advanced setup, and could cause service errors if not customized for your environment. So, tread cautiously.
7. Setup a brute force monitor
A firewall inspects each network packet to see if it should be dropped or not. That needs a lot of processing power.
If a tool can be setup to look at recurring blocks, and blacklist the offending IP, processing power can be saved. That’s what a brute force monitor does. It is an essential addition to a firewall.
To explain the function and configuration of a brute force monitor is beyond the scope of this article, but there are a few good ones like BFD and LFD that you should take a look at.
In short..
The internet is infested with a lot of bad traffic. A well configured firewall can block a vast majority of those undesired traffic. Here we’ve explained what are the threats your Linux firewall should be protected against, and a few best practices that’ll help you along.
Bobcares helps online businesses of all sizes achieve world-class security and uptime, using tried and tested solutions. If you’d like to know how to make your server more reliable, we’d be happy to talk to you.
For as low as
$74.99/server/mo
Get full spectrum infrastructure management services – including setup, monitoring & maintenance.
Never again face a critical business downtime. We keep your servers secured, optimized and updated at all times. Our engineers monitor your servers 24/7 and fix issues before it can affect your customers.








0 Comments