Are you a website owner? Do you have Magento shopping cart in your site? Is your server running an insecure version of Linux kernel?
If the answers to these questions are ‘yes’, then you’d be noticing a ‘Dirty COW vulnerability’ alert in your Magento admin dashboard.
What is Magento dirty cow vulnerability alert?
Magento is an open source shopping cart software that accounts for 29.1% of market share now. Magento sites mostly run on Linux servers.
Since Dirty COW vulnerability is a bug in the Linux kernel, it affects all servers that run Linux OS flavors – such as RedHat, Ubuntu, CentOS, etc.
Website owners who manage the Magento cart would see this message upon login to the admin portal as the ‘admin’ user at http://magento-site.com:8096/admin/ –
'Latest Message: Dirty COW Linux OS Vulnerability – 10/25/2016 Read details'
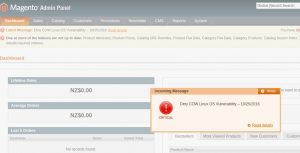
Dirty COW vulnerability alert in Magento
Why is Magento dirty cow warning critical?
Further inspection of this alert message shows that it is a critical warning and the solution is to update the OS in your server to secure kernel version without delay.

Magento dirty COW vulnerability message
Dirty COW (CVE-2016-5195) is a privilege escalation vulnerability in the Linux Kernel that can allow a local user to gain root access to the server.
Exploiting a race condition that handle kernel’s memory operations, an attacker can execute malicious code and compromise the whole server.
If your website has Magento store setup for online transactions, the attackers can steal confidential information such as credit card details, once they gain root access.
As Dirty COW vulnerability allows hackers to obtain super user privilege to the server and do anything in it, this is a critical exploit that has to be fixed without delay.
To know more about the vulnerability and the OS versions that are affected, read our post on Dirty Cow vulnerability.
How to fix Magento dirty cow vulnerability alert message
Since the exploit is related to the kernel and not the Magento software as such, this alert message cannot be fixed by upgrading the software.
The only way to resolve this exploit alert is to update your server’s kernel to the latest available secure version.
The fix for the dirty cow vulnerability depends on the OS your server is running on. The first step is to identify the OS and kernel version using ‘uname’ command.
Here’s how to update the Linux kernel in various OS flavors:
To update RedHat and CentOS with the secure kernels, use 'yum update'. Reboot the server after update. In Ubuntu and Debian servers, use 'apt-get update' command to update the OS and reboot the server after that.
To know more about updating kernels in different servers to fix dirty cow vulnerability bug, read our post ‘How to fix Dirty Cow vulnerability in CentOS, RedHat, Ubuntu, Debian, CloudLinux and OpenSuse Linux servers‘
To summarize..
Though the error message here is relevant to Magento, this bug is related to the kernel and not the software. As a result, its impact is wide-spread and affects the entire server.
Kernel updates have to be done with utmost caution, as broken updates can crash the server. In some servers with custom kernel, manual recompilation may be required.
At Bobcares, our 24/7 security expert team keeps track of the vulnerabilities and apply patches to our customers’ servers pro-actively, to minimize exposure to exploits.
If you’d like to know how to secure your servers with the best security practices and to ensure 24/7 pro-active administration, feel free to contact us.








0 Comments