Have you heard of PHP passthru() exploit and it’s bad effects?
Improper way of using the PHP passthru function mess up with the server data at an unimaginable level. It makes the server vulnerable to hacking.
That’s why at Bobcares we receive many requests to disable the passthru() function in PHP as part of our Server Management Services.
So today, let’s get deep into the passthru() function and discuss how our Support Engineers disable it for our customers.
What is PHP passthru exploit?
Have a vague idea about it? Let’s make it clear.
We usually use the passthru() function to execute a command.
void passthru ( string command [, int &return_var] )
It runs the external program specified in the first parameter and prints out all the output it generates. Also, it sends the raw output from this program to the output stream with which PHP works.
A typical application of passthru function will be the PHP scripts that output images directly.
But, taking the user input and passing it to the passthru() function can often be fatal. This is because users can bypass security and can do nasty things with the server. For instance, if some hackers give ‘cat /etc/passwd‘ inside the passthru() function, it will run on an existing file and prints out the content of the system password file.
So, the dangerous passthru() function can create a pinhole to hacking attacks.
How we prevent passthru exploit?
We now know the bad effects that vulnerable PHP functions create on the server.
But, how can we prevent PHP passthru exploit?
Let’s check on the various methods that our Support Engineers do on our servers.
1. Disabling passthru function
One of the best methods to protect the server is to avoid the usage of PHP passthru function. Therefore, we usually disable certain PHP functions including passthru for security reasons.
As we have already said, the passthru() function is one such function that is dangerous when used with unsanitized input values.
We can easily disable it via Control Panel or by modifying the PHP configuration of the server.
a) From command-line
To completely disable passthru fuction for all domains on the server, we edit the main PHP configuration file at /etc/php.ini and add the selected functions to the variable disable_functions.
A list of disabled functions on one of the servers we manage appear as:
[root@xxx ~]# php -i | grep disable_functions disable_functions => show_source, system, symlink, getmyuid, link, eval, fput, passthru, exec,
b) In cPanel
To modify it from cPanel, we do the following steps.
- Firstly, we log in to cPanel.
- Then, navigate to MultiPHP INI Editor.
- Next, click on Editor mode. We need to select a location to open the corresponding PHP configuration.
- Now, we edit the php.ini file. We locate the disable_functions directive to disable specific functions.
- Then, we add the passthru() function just after the disable_functions as disable_functions = “passthru”
- Finally, we click on the Save to make the changes.
That disables the passthru() function. And, we confirm it from the phpinfo page on the website.
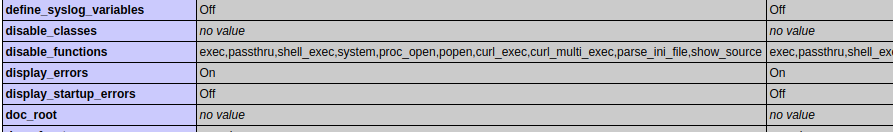
2. Using a web application firewall
In a similar way, the usage of vulnerable functions can be prevented by using web application firewalls like ModSecurity, CXS, etc.
These web firewall has loaded configuration that contains various rules to block suspicious links. Basically, it does a check on the user’s input. If the user tries to use commonly misused functions like “passthru”, “system”, “exec”, etc. it automatically blocks the links. Thus it would display an error on the website.
Moreover, such WAF blocks the request that contains file paths like “/etc/passwd”, “/etc/shadow“, etc.
[Need more help to disable passthru() function?- We are available 24/7 to help you.]
Conclusion
In short, the PHP passthru() exploit uses the user input and affects the server security adversely. Today’s write-up also discussed how our Support Engineers disable this PHP function effectively for our customers.







0 Comments