Secure DigitalOcean Droplet help us ensure the app’s security and usability.
As part of our Digitalocean managed service, Bobcares responds to all inquiries, no matter how small.
Let’s take a closer look at the important steps our Support team used to Secure the DigitalOcean droplet.
Important Ways to secure DigitalOcean Droplets
On top of virtualized hardware, DigitalOcean Droplets are virtual machines (VMs) with a Linux operating system. These virtual servers are brand-new droplets. These virtual servers must be set up so that the application is secure and easy to use.
Basic security measures are always crucial at the beginning of any project, and it is advantageous to develop a more specialized security strategy over time that fits the particular requirements of your environments and applications. Here are some fundamental security precautions we take when setting up and deploying your DigitalOcean droplet.
Step 1: Utilize SSH KEYS
A Popular encrypted protocol for connecting to servers is Secure Shell (SSH). Making a private and public key pair for authentication with SSH keys is possible. The user must maintain the privacy and security of the private key, but they are free to distribute the public key. We have two choices when interacting with Digital Ocean droplets. either passwords or SSH keys.
Of these two, the SSH key is more secure because:
- The bit length of SSH keys is longer.
- Passwords typically have 8 to 16 characters, which makes them simple to crack.
- SSH keys are 4096-bit characters long, making them challenging to decipher.
- All SSH keys are random.
- SSH keys have a large number of prime numbers, making them difficult to socially engineer.
- We must physically access someone’s computer in order to obtain their SSH key.
Connecting to a Server with SSH Keys
To configure SSH key authentication, the public SSH key must be kept on the server in the appropriate directory. The server will request evidence that we possess the associated private key when our client first connects to it. The SSH client receives a randomly chosen value. The SSH client will then use the private key to encrypt the response before trying to send the encrypted response to the server. The server then uses the public key to decrypt the client’s response. If the server can decrypt the random value, it can connect to us without requiring a password because it means that our client has a private key.
ssh-keygen
Our key pair is kept in the default location on Linux, which is ~/.ssh, while on Windows and macOS, it is in /Users/our_username/.ssh. Simply copy the public key, which by default has the filename id_rsa.pub.
- Firstly, locate the SSH keys section on the Security tab, under the Account section.
- Then, click Add SSH Key to bring up the window for a New SSH key.
- Finally, give it a name, paste the public key into the SSH key content field, and click Add SSH Key.
Step 2: Firewalls
Although firewalls only provide minimal security, they are crucial for protecting the DigitalOcean Droplet by limiting port access. Firewalls prevent access to specific IP addresses. This makes it much simpler to grant ssh and MySQL access. Additionally, it aids in preventing specific users from particular nations from gaining access to the droplet or website. We can set up firewall rules to assist in opening and closing ports to the outside world.
Simply follow these steps to configure the droplet-level firewall.
- Firstly, open the create menu by clicking Create in the top right corner of the DigitalOcean control panel.
- Then, to access the firewall creation page, click Cloud Firewalls.
- Type inbound-ssh-only into Name.
- Finally, keep SSH’s single default rule in Inbound Rules.
- Keeping layers secure is the key to security. Therefore, select both rather than just one.
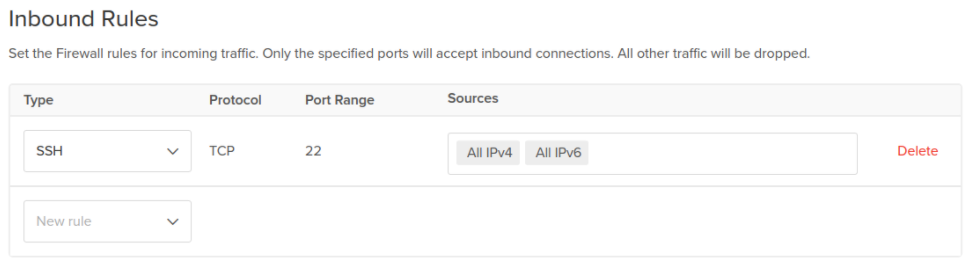
Step 3: VPCs ( Virtual Private Clouds )
Virtual private clouds have features that enable all droplets to have a large outer casing. It is technically not a firewall, but rather an additional layer that aids in the protection of servers. Rather than applying firewall rules to individual droplets, rules are applied to the group as a whole.
Keep the default rules in Outbound Rules, which allow all traffic to any destination on any port.
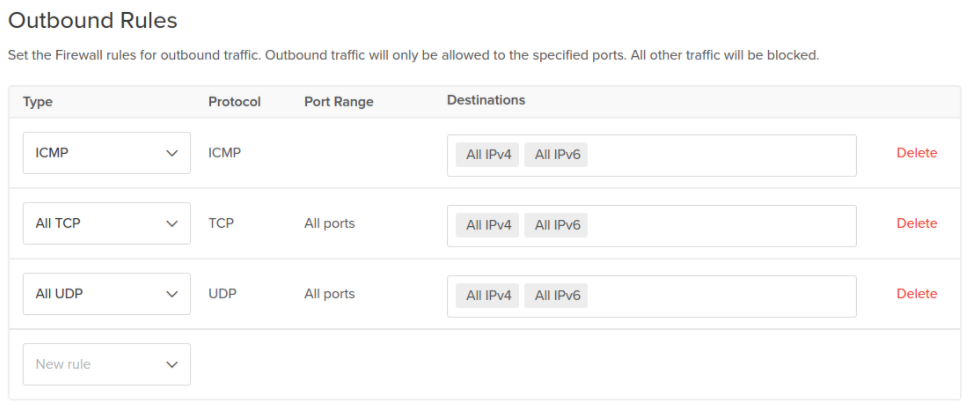
Click Apply to Droplets, then enter the tag we made with the new Droplet. When we create additional Droplets in the future, adding the same tag to them will automatically add them to this cloud firewall, simplifying future scaling.
Step 4: Unattended Updates
This method has a disadvantage. If we enable auto-update, it will update a large number of packages, which may break any library. In this case, determining what caused the problem will be nearly impossible. Before beginning the update process, keep in mind to update all libraries and packages.
Step 5: Backup
We regularly take backups, but we frequently forget to test them. A theory is an alternative that has never been tried. Not having a disaster recovery plan is taking backups. If a backup doesn’t work when it’s needed despite our best efforts, we will have two issues. Put no faith in a single entity. Take your backup offsite. It’s essential to perform external backups.
Step 6: SSL/TLS Encryption
Apps, businesses, and platforms all collect data. Various businesses purchase these data. We must employ some kind of secure internet communication method in order to reduce such illegal activities.
The SSL/TLS protocol encrypts internet traffic, allowing for secure user-to-user communication. These encryption techniques shield raw data from outsiders.
Step 7: Isolated Execution Environment
Isolated execution refers to a software reference implementation of the security through the isolation concept. It provides a contained environment where malware can run without affecting the entire system, rather than attempting to prevent malware from running or prevent its insertion into the user’s computer.
- This execution strategy has a good track record.
- It is preferable to separate each component.
- The database server and the application server ought to be kept apart.
- For instance, even if the application server is compromised, we can still protect the database server without intervening.
- The public network is the application server.
- The private network is the database server.
- Avoid making the database accessible to the public online.
Step 8: Service Auditing
A new vulnerability could still harm the server even with all the best security measures in place. Regular monitoring can help with this.
Service auditing and security auditing are methods for keeping an eye on and analyzing server activity. It is crucial to have audit policies that outline the events, system logs, history, and audit frequency that we want to monitor.
[Looking for a solution to another query? We are just a click away.]
Conclusion
In conclusion, security is a crucial factor. To prevent security breaches, it’s crucial to keep the Droplets safe from malicious hackers. These are the eight ways we can secure the DigitalOcean Droplet.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.




0 Comments