List of VMware VMS Using Ansible
To use Ansible to get a list of VMware virtual machines (VMs), we would use a special tool called a module, which helps Ansible interact with VMware environments. One such module is community.vmware.vmware_vm_vm_drs_rule_info, which is part of a collection of tools specifically designed for VMware in Ansible.
This module functions similarly to a dedicated tool, enabling Ansible to collect crucial data regarding the VMs within the VMware setup. Thus, without having to manually find each one, we may quickly gather details about the VMs by using this module. It’s a method for using Ansible to automate and streamline the control of the VMware framework.
An Example
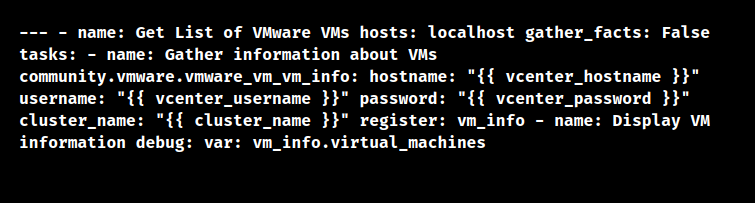
Here,
vcenter_hostname:
The VMware vCenter server’s hostname or IP address.
vcenter_username:
The username that was entered to log into the vCenter server.
vcenter_password:
The passcode is linked to the given username.
cluster_name:
The name of the cluster we would want to obtain VM details for.
The “community.vmware.vmware_vm_vm_info” module is used in this playbook in order to collect data on VMs within the specific cluster. The result is saved in the “vm_info” variable using the register keyword. Lastly, the playbook uses the debug module to print the VM’s details. We must set up the necessary Ansible VMware collection before running this playbook. We can use the following code to do this:

In order to interact with the VMware vCenter server, make sure we also have the required network connectivity and permissions. In accordance with the VMware config, modify the playbook variables.
[Looking for a solution to another query? We are just a click away.]
Conclusion
In conclusion, this article explains an Ansible module that we can use to get the details of a list of VMS in VMware.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.







0 Comments