Let us take a closer look at the Cloudflare bot protection bypass and how to set it up with the support of our Server management support services at Bobcares.
What is Cloudflare bot protection bypass?
Cloudflare is a corporation that is known for its online performance and security. On the security front, they provide customers with a Web Application Firewall (WAF). A WAF may protect applications against a variety of security risks, including cross-site scripting (XSS), credential stuffing, and DDoS assaults.
Cloudflare’s Bot Manager is one of the major components is present in their WAF. Its primary purpose as a bot security system is to reduce assaults from harmful bots. In the attacks the impact on regular users is less.
Cloudflare recognizes the importance of specific bots. No website, for example, wishes to prevent Google or other search engines from scanning its website. Cloudflare has an allow list of recognized good bots to account for this.
Unfortunately for web scrapers, any nonwhitelisted bot traffic is bad. So, without looking at the intention, it will not allow the bot access to a Cloudflare web page.
Scraping a Cloudflare-protected site may result in the following Bot-manager errors:
Error 1020: Access DeniedError 1010: The owner of this website has banned your access based on your browser's signature.Error 1015: You are being rate limitedError 1012: Access Denied
These errors appear with the HTTP response status code 403 Forbidden.
How does Cloudflare detect bots?
Cloudflare has two major types of bot detection technologies: Passive bot detection strategies rely on backend fingerprinting checks. The active techniques rely on checks done on the client side. Let’s have a look at some samples from each area together.
Cloudflare passive bot detection techniques
Here is a partial list of several passive bot detection strategies setup by Cloudflare:
1: Detecting botnets
Cloudflare keeps a list of devices, IP address, and natures connected with harmful bot networks. Any device that is in one of these networks will face an instant block or extra client side blocks.
2: IP address reputation
The properties such as geolocation, ISP, and reputation history decide the reputation of an IP address. IP address of a data center or a known VPN service will have a lower reputation than a home IP address. A site may also opt to block access from regions outside of the service area. This is because the traffic from genuine customers should never come from there.
3: HTTP request headers
Cloudflare determines whether we are a robot based on HTTP request headers. If we have a nonbrowser user agent, such as python requests/2.22.0, we can readily identify the scraper as a bot.
It will block the bot if it sends a request that lacks headers that would normally be present in a browser. Alternatively, if we have headers based on the user agent.
For example, for a Firefox user-agent, include a
sec-ch-ua-full-version-listheaderCloudflare active bot detection techniques
Cloudflare will perform many tests on the client side. It does this when we visit a website to detect if we are a robot.
CAPTCHAs
CAPTCHAs were the go-to approach to spot the bots. However, it will recognize that they degrade the user experience. Whether or whether Cloudflare delivers a captcha to the user determines numerous basis, including:
- The layout of the site. A website director can start a CAPTCHA all the time, only sometimes, or never at all.
- Level of danger. Only if the traffic is suspicious will Cloudflare offer a CAPTCHA. A CAPTCHA, for example, will display if a user browses a site using the Tor client but not if the user uses a regular web browser such as Google Chrome.
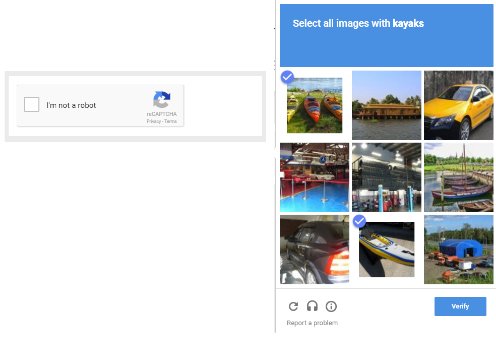
Cloudflare uses reCAPTCHA as its primary captcha supplier. However, as of 2020, they have fully used hCaptcha. Here’s an example of hCaptcha on a Cloudflare-protected site:
How to bypass CloudFlare bot protection?
First, we’ll register a domain and set up a Cloudfare account. After Cloudflare approves the domain, we must add at least one true DNS record that employs proxy mode.
Now we have to write a JavaScript worker to act as a reverse proxy. Make a new worker and put the contents of
worker.jsThen add the following route to the worker:
proxy.domain.com/If we try to access
proxy.domain.com[Need assistance with similar queries? We are here to help]
Conclusion
To sum up we have learned how to set up the Cloudflare bot protection bypass. With the support of the Server management support services, we have seen how to set up the Cloudflare bot protection bypass.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.







0 Comments