On March 1, 2016, a new SSL vulnerability called DROWN (Decrypting RSA with Obsolete and Weakened Encryption) was disclosed by security researchers.
This vulnerability (aka CVE-2016-0800) allows attackers to decrypt even strong TLSv1.2 connections, if the server supports the obsolete SSLv2 protocol.
As reports filter in, it is known that even large websites such as Yahoo, Samsung, Alibaba, etc. are affected by this vulnerability. Your server might be affected if you have NOT EXPLICITLY DISABLED SSLv2.
Bobcares maintains server infrastructure of several small, mid-size and large online businesses. In these servers, we keep old protocols such as SSLv2 and SSLv3 fully DISABLED.
Since the last SSL POODLE vulnerability scare, SSL cipher strength check is a standard part of our daily security scans on the servers we maintain.
Are your servers vulnerable to attacks?
Today, all our security teams re-confirmed that none of the servers under our care is vulnerable to the DROWN attack. Here’s how we did the scans:
Are you vulnerable to DROWN attack? Find using SSLyze
For each each server, we listed all the public IPs in it, and all the open ports in it. Then we used an SSL scanning tool called SSLyze to check if SSLv2 ciphers are supported. We use this tool because we’ve seen that other ways of verifying weak ciphers (like openssl client connect, nmap, etc.) may not be 100% accurate.
The command is:
secsev # sslyze_cli.py --sslv2 203.0.113.25:443
In the servers we maintain it returned the below result:
SCAN RESULTS FOR 203.0.113.25:443 ------------------------------------------------------ * SSLV2 Cipher Suites: Rejected: TLS_RSA_WITH_NULL_MD5 TCP / Received RST SSL_CK_RC4_64_WITH_MD5 TCP / Received RST SSL_CK_RC4_128_WITH_MD5 TCP / Received RST SSL_CK_RC4_128_EXPORT40_WITH_MD5 TCP / Received RST SSL_CK_RC2_128_CBC_WITH_MD5 TCP / Received RST SSL_CK_RC2_128_CBC_EXPORT40_WITH_MD5 TCP / Received RST SSL_CK_IDEA_128_CBC_WITH_MD5 TCP / Received RST SSL_CK_DES_64_CBC_WITH_MD5 TCP / Received RST SSL_CK_DES_192_EDE3_CBC_WITH_MD5 TCP / Received RST
This means, all SSLv2 requests were rejected.
But, if a server is vulnerable, something like the following will be shown:
SCAN RESULTS FOR 203.0.113.77:443 -------------------------------------------------- * SSLV2 Cipher Suites: Preferred: SSL_CK_RC2_128_CBC_WITH_MD5 - 128 bits Accepted: SSL_CK_RC4_128_WITH_MD5 - 128 bits SSL_CK_RC2_128_CBC_WITH_MD5 - 128 bits SSL_CK_DES_192_EDE3_CBC_WITH_MD5 - 112 bits SSL_CK_DES_64_CBC_WITH_MD5 - 56 bits SSL_CK_RC4_128_EXPORT40_WITH_MD5 - 40 bits SSL_CK_RC2_128_CBC_EXPORT40_WITH_MD5 - 40 bits
This command command checks if SSLv2 is enabled in port 443.
In the servers we maintain, the same was repeated on all ports, such as 465 (SSL-SMTP), 993 (SSL-IMAP), 995(SSL-POP3), etc. A server is vulnerable to DROWN if ANY port in the server has SSLv2 available.
CLICK HERE TO PROTECT YOUR SERVERS NOW!
Are your servers vulnerable to DROWN?
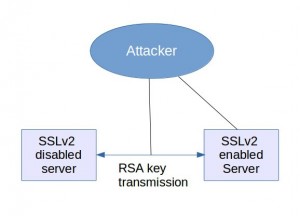
In using the above scan, if you found SSLv2 to be enabled in ANY service, you should consider your server, and any other server with the same private key – certificate pair as vulnerable. This is because, once the session key is obtained through a weak SSLv2 connection, any further communication between that client, and ANY other server with the same private key is open.
How to fix DROWN vulnerability?
Before we get into what can be done, its important to know that DROWN DOES NOT steal your private key. So you do not have to get a new certificate or a private key.
But you will need to make sure SSLv2 is fully disabled in all your servers and all your services. There are a couple of ways to go about it:
- Patch your OpenSSL, IIS (Internet Information Services) or NSS (Network Security Services) servers.
- Disable SSLv2 protocol in all your public facing services.
How to patch OpenSSL in Linux servers
OpenSSL in Linux servers need to be updated to version 1.0.1s or 1.0.2g as is applicable. For instance, OpenSSL 1.0.2 is upgraded to 1.0.2g and OpenSSL 1.0.1 to 1.0.1s. Note that individual vendors may name their OpenSSL packages differently.
In CentOS and RedHat server versions 5, 6, 7, you can do it using a yum update:
# yum update openssl
The packages in different CentOS versions are:
CentOS 5 : openssl-0.9.8e-39.el5_11
CentOS 6 : openssl-1.0.1e-42.el6_7.4
CentOS 7 : openssl-1.0.1e-51.el7_2.4
For SUSE and OpenSUSE servers, use the zypper command
# zypper patch
In Ubuntu and Debian servers, use the below command
# apt-get install --only-upgrade libssl1.0.0 openssl
In Oracle Linux, use the yum command
# yum update openssl
SECURE YOUR SERVERS IMMEDIATELY FROM ATTACKS!
How to fix DROWN in Apache, Nginx, Postfix, Courier, Exim and other services
In the servers we manage, we disabled BOTH SSLv2 and SSLv3, as these are old protocols known to have security issues. Here’s how we did it for the HTTP, FTP, SMTP, POP3 and IMAP services.
HTTP – Apache
Edit the Apache configuration file (/etc/httpd/conf/httpd.conf), and set the below configuration:
SSLProtocol All -SSLv2 -SSLv3 SSLCipherSuite EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256 SSLHonorCipherOrder on
Restart Apache.
HTTP – Nginx
Go to Nginx configuration (/etc/nginx/nginx.conf), and change the line
ssl_protocols SSLv2 SSLv3 TLSv1 TLSv1.1 TLSv1.2;
to
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
Restart Nginx.
SMTP – Exim
Edit Exim configuraiton file (/etc/exim.conf) and change tls_require_ciphers to
ALL:!aNULL:!ADH:!eNULL:!LOW:!EXP:RC4+RSA:+HIGH:+MEDIUM:!SSLv2:!SSLv3
Restart Exim.
SMTP – Postfix
Edit the Postfix configuration file (/etc/postfix/master.cf) and set the following configuration details:
smtpd_tls_mandatory_protocols=!SSLv2,!SSLv3 smtp_tls_mandatory_protocols=!SSLv2,!SSLv3 smtpd_tls_protocols=!SSLv2,!SSLv3 smtp_tls_protocols=!SSLv2,!SSLv3
POP/IMAP – Courier-IMAP / Dovecot
Edit mail server configuration file (/etc/dovecot.conf) and change SSL Cipher List to
ALL:!aNULL:!ADH:!eNULL:!LOW:!EXP:!RC4+RSA:+HIGH:+MEDIUM:!SSLv2:SSLv3
FTP – Pure-FTP / Pro-FTP
Edit FTP configuration files (/etc/pure-ftpd.conf, /etc/proftpd/proftpd.conf) and change the TLS Cipher Suite to
HIGH:!aNULL:!eNULL:!PSK:!RC4:!MD5:!TLSv1:!SSLv2:!SSLv3







Hey, when I try yum update it doesn’t show me the 1.0.1s update, it only shows the 1.0.1e update.
Any ideas which repo to use? (I’m on CentOS 6)
Hi Imad,
As per CentOS announcement:
https://lists.centos.org/pipermail/centos-announce/2016-March/021712.html
You need either openssl-1.0.1e-42.el6_7.4.i686.rpm or openssl-1.0.1e-42.el6_7.4.i686.rpm as per your architecture.
I’ve updated the article now.
thx a lot, the best part of your article is the tool available also for Windows (sslazy) and simple test. I have searched few hours for this kind of test tool. Thx!