67.8% of public servers run on Linux. This makes it a lucrative target for hackers. Attackers keep finding new ways to breach into Linux servers all the time, but with proper precautions you can keep hackers at bay.
Our Support Engineers help hundreds of online businesses (like web hosts, digital marketers, etc.) keep their servers rock solid and secure.
Here are the TOP 7 tips from our support diaries to keep Linux servers safe from hackers.
1. Keep your server updated
As per recent studies, 68% of attacks on servers were targeted on software vulnerabilities. So, the first step to secure your server is to keep all applications updated.
Setup your server and applications to send you a notification as soon as an update is available. Read the update descriptions and see if it contains any bug fixes. If so, apply the patches immediately.
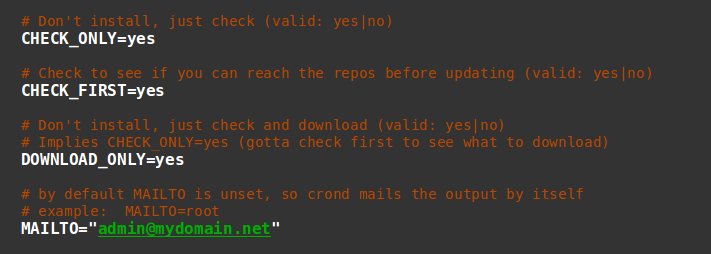
Yum-Cron is a utility that’ll notify you when updates are available
[ Running a hosting business doesn’t have to be hard, or costly. Get world class Support Engineers at $12.99/hour (bulk discounts available) ]
2. Enforce strong network security
All server attacks happen over the network. So, securing the network goes a long way in blocking hackers.
There are several ways to do it:
- Harden the Linux kernel parameters related to networking – This can be done by modifying the values in /etc/sysctl.conf.
- Restrict access to services such as SSH using TCP Wrappers – This can be done by editing /etc/hosts.allow and /etc/hosts.deny.
- Setup a strong firewall using IPTables – Here’s an in-depth post on how to configure firewall in Linux servers
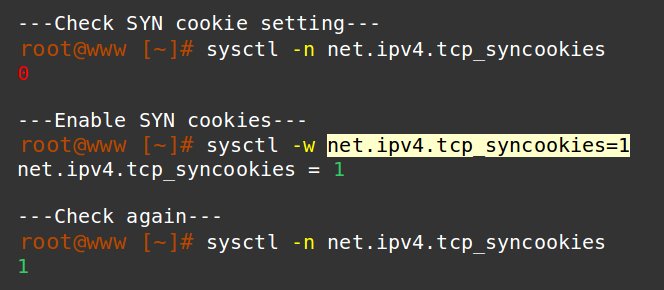
SYN cookie is a Kernel parameter that mitigates a popular attack known as SYN flood
[ Use your time to build your business. We’ll take care of your customers. Hire Our Support Engineers at $12.99/hr. ]
3. Implement a strong user login & password policy
The most vulnerable part of a server is often the users. Hackers use a wide range of attacks such as brute forcing, phishing, drive-by-downloads, etc. to steal valid login details.
So, securing the user logins should be a priority. A few essential steps are:
- Enforce use of strong passwords – Make the passwords at least 20 characters long, and encourage use of password managers.
- Prevent use of old passwords – This will block out anyone silently stealing data using old passwords.
- Lock account after login failures – If the login is locked after a few retries, brute force attacks will fail.
- Use IP restriction where possible – For sensitive services such as SSH or Database, limit the login to pre-approved IPs.
- Use 2-factor authentication if possible – For highly sensitive servers and logins (such as admin), 2-factor authentication is important.

Google authenticator is a free 2-factor auth system
4. Restrict user privileges using the filesystem
The filesystem controls the access privileges of each user. By hardening the filesystem settings, any malware that’s uploaded to the server can be blocked from being executed.
Here are a few tips:
- Prevent modification of core system binaries by making it Immutable (using chattr command).
- Limit access to /boot to only root user.
- Mount user-accessible directories such as web folders, /tmp, and other world-writable folders as “NoExec”
- Block “SetUID” and “SetGID” file creation in world-writable and web folders.
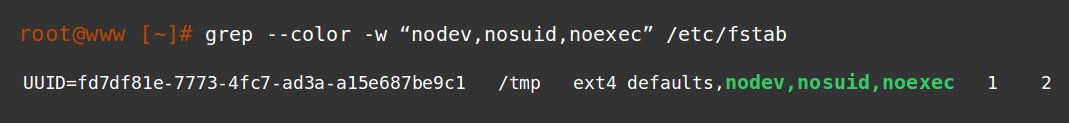
Adding “nodev”, “nosuid” and “noexec” to world accessible directories makes execution of malware quite hard.
[ You don’t have to lose your sleep to keep your customers happy. Our Support Engineers cover your servers and support your customers 24/7 at just $12.99/hour. ]
5. Harden the Linux kernel
It is hard to get into a fully patched and updated system. However, there are cases where attackers exploit un-published vulnerabilities and get access to servers. A strong precaution against such a possibility is to harden the Linux Kernel.
There are various solutions for this.
- Use kernel hardening patches such as ExecShield or PaX – Kernel hardening patches protect against common exploits such as buffer overflows, path name attacks, privilege escalation, etc.
- Setup Mandatory Access Control systems such as SELinux or AppArmor – This prevents users from doing any action other than what’s absolutely needed for their service. For eg. a web user won’t be able to access “/etc” configuration directory.
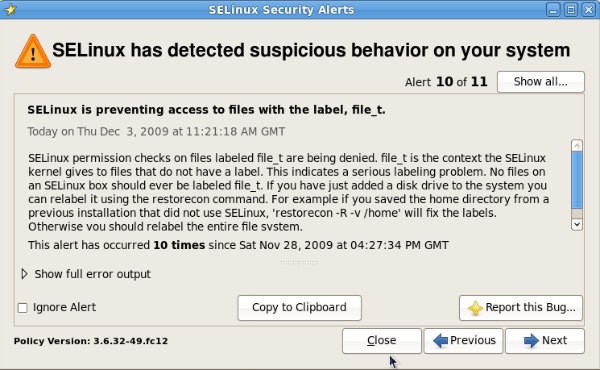
SELinux is the standard in RedHat compatible servers, and has a GUI configuration interface.
6. Enable malware scanning
Many server attacks start by uploading a malware to the server.
Setup malware scanning on all incoming and outgoing network traffic to block hack attempts. Here are some best practices:
- Integrate anti-virus tools with FTP and Web disk to scan incoming files.
- Use the “iNotify” feature of Linux file systems to trigger a scan when a new file is created.
- Use a Web Application Firewall + anti-virus to scan web traffic.
- Use multiple anti-virus signature databases to make sure no malware gets through your filters.
Read : How to protect your server from malware
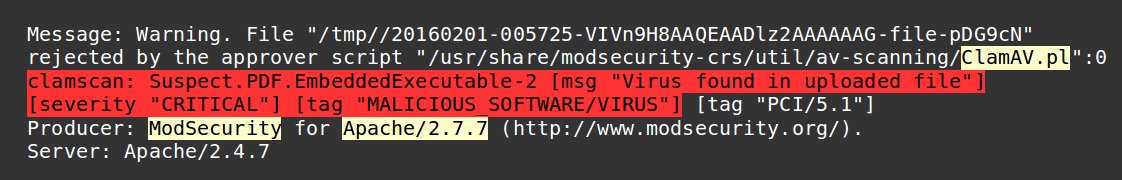
ClamAV anti-virus can be integrated with ModSecurity web app firewall to detect malware uploaded via web interfaces
7. Setup an intrusion detection system
Quick reaction to an intrusion or an intrusion attempt can help you limit any damage done on the server.
Intrusion detection systems (IDS) monitor sensitive directories, logs and processes to notify you of un-usual behavior. Here are the top things to monitor:
- Monitor for processes that’s executed from unknown files or unusual location.
- Monitor system libraries and investigate any change of those files.
- Monitor directories that only the administrator can access. Investigate any access that you do not recognize.
- Monitor network traffic for malware. Setup the system to automatically block malware sources.
Read : An introduction to different Intrusion Detection Systems
In short..
Linux is the most popular server operating system, which makes it a prime target for hackers. Today we’ve seen the top 7 ways in which you can protect your Linux server from hackers.
Bobcares helps online businesses of all sizes achieve world-class security and uptime, using tried and tested solutions. If you’d like to know how to make your server more reliable, we’d be happy to talk to you.







0 Comments