Sometimes, we may need to hide web.config when using directory browsing in IIS. As part of our Server Management Service, Bobcares provides answers to all of your questions.
Overview
- Understanding Directory Browsing in IIS
- Protecting Sensitive Files in IIS: Focus on web.config
- Best Practices for Secure IIS Configuration
- Conclusion
Understanding Directory Browsing in IIS
Directory Browsing in IIS (Internet Information Services) is a powerful yet potentially risky feature. When enabled, it allows users to view the contents of a directory in their browser if no default file is specified in the URL. However, its use requires careful consideration, as it can expose sensitive files, such as the web.config, to prying eyes.
In this article, we’ll explain how Directory Browsing works, the risks involved, and how to protect critical files like web.config while maintaining secure IIS configurations.
Directory Browsing enables a web server to display the contents of a directory to users. For example, if users access a folder without a default file (like index.html), they’ll see a list of all files in that folder. By default, Directory Browsing is disabled in IIS. If a user attempts to access a directory without a default file, IIS returns a 403 Forbidden error.
If enabled, users might inadvertently see sensitive files, such as web.config, which could expose critical application configurations.
Protecting Sensitive Files in IIS: Focus on web.config
Even when Directory Browsing is enabled, IIS includes safeguards to block direct access to web.config. However, additional measures can further secure the setup.
1. Default Protection for web.config
IIS automatically applies rules to block access to web.config, ensuring:
Requests for web.config return a 403 Forbidden error.
This protection is in place regardless of Directory Browsing settings.
2. Strengthening Security for Sensitive Files
Confirm web.config Access Denial
Open IIS Manager.
Select the site or application.
Navigate to Request Filtering > Hidden Segments.
Ensure web.config is listed as a hidden segment, preventing it from being displayed or accessed via the web.
3. Use Authorization Rules
Open the web.config file and include rules to restrict access. Example:
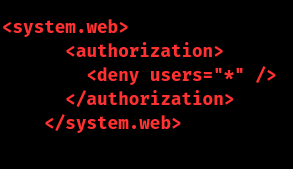
This ensures only authorized accounts can access the file.
4. Disable Directory Browsing If Not Needed
If Directory Browsing isn’t essential, it’s best to keep it disabled:
Open IIS Manager.
Select the site or directory.
Go to Directory Browsing and click Disable.
5. Restrict File System Permissions
Navigate to web.config in the file system.
Right-click > Properties > Security tab.
Set permissions to allow only authorized accounts (like the application pool identity) access.
6. Verifying the Configuration
After implementing these steps, test the setup to ensure web.config and other sensitive files are protected:
Attempt to access web.config directly through a browser. A 403 Forbidden error should appear.
If Directory Browsing is enabled, confirm that sensitive files aren’t listed in browsable directories.
Best Practices for Secure IIS Configuration
1. Disable Directory Browsing: Only enable it if absolutely necessary and ensure no sensitive files are exposed.
2. Leverage Built-in IIS Protections: Use features like Request Filtering and Hidden Segments to safeguard critical files.
3. Apply Granular Permissions: Limit file system access to essential accounts and roles.
4. Monitor and Audit: Regularly test the configurations to identify and fix vulnerabilities.
[Searching solution for a different question? We’re happy to help.]
Conclusion
Managing Directory Browsing in IIS requires a balance between functionality and security. While enabling it can be helpful in specific scenarios, it’s crucial to safeguard sensitive files like web.config. By leveraging IIS’s default protections and implementing additional security measures, we can ensure a secure and reliable hosting environment.







0 Comments