Install OSSEC Ubuntu with ease.
As a part of our Server Management Service, our Support Engineers provide solutions to every query that comes our way.
Let’s take a look at this in-detail tutorial by our Support Team on how to install OSSEC.
All About OSSEC
OSSEC is a host-based intrusion detection system used to keep an eye on server activity. It supports popularity used operating systems like FreeBSD, Linux, Windows, Linux, Solaris, and so on.
We can use OSSEC to monitor either a single server or multiple servers in server or agent mode. Additionally, it offers a real-time view of what is happening on the server.
Its cross-platform architecture allows you to monitor several systems from a centralized location.
Our Support Engineers are here to demonstrate how to install and configure OSSEC in order to monitor a local Ubuntu 16.04 monitor.
Install OSSEC Ubuntu: Prerequisites
- A newly deployed Ubuntu 16.04 server
- Hostname localhost should be set up on the server.
- Static IP address 192.168.15.189 has to be configured on the server.
Installing Dependencies
First, we will update the system to the latest stable version with the following command:
apt-get upgrade -y
We will also install gcc, libc, PHP, and Apache packages with the following command:
apt-get install build-essential gcc make apache2 libapache2-mod-php7.0 php7.0 php7.0-cli php7.0-common apache2-utils unzip wget sendmail inotify-tools -y
How to install OSSEC on Ubuntu?
First, our Support Engineers will download the latest OSSEC version from GitHub repository with this command:
wget https://github.com/ossec/ossec-hids/archive/2.9.0.tar.gz
Then, we will extract the downloaded file with this command:
tar -xvzf 2.9.0.tar.gz
After that, we will change to the extracted directory and then install OSSEC as seen below:
cd ossec-hids-2.9.0 sh install.sh
Then, we will be prompted to answer a few questions as seen below:
Select your language, if your language is English then type en and press Enter:
(en/br/cn/de/el/es/fr/hu/it/jp/nl/pl/ru/sr/tr) [en]:en
This will result in the following output:
OSSEC HIDS v2.9.0 Installation Script - http://www.ossec.net You are about to start the installation process of the OSSEC HIDS. You must have a C compiler pre-installed in your system. - System: Linux Node1 4.4.0-45-generic - User: root - Host: localhost -- Press ENTER to continue or Ctrl-C to abort. --
After pressing Enter, we will see the following output:
1- What kind of installation do you want (server, agent, local, hybrid or help)? local
Here, we will enter local in order to monitor the server the installation has taken place on.
After that, we will see the following:
- Server installation chosen. 2- Setting up the installation environment. - Choose where to install the OSSEC HIDS [/var/ossec]:</pre. Here we will select OSSEC install location and press Enter:
Installation will be made at /var/ossec . 3- Configuring the OSSEC HIDS. 3.1- Do you want e-mail notification? (y/n) [y]: y
Here, we will enter y and press Enter to see the following output:
- What's your e-mail address? root@localhost - We found your SMTP server as: 127.0.0.1 - Do you want to use it? (y/n) [y]: y
Then, we enter our local e-mail address and press Enter.
Installation: Integrity check daemon, rootkit detection, active response
3.2- Do you want to run the integrity check daemon? (y/n) [y]: - Running syscheck (integrity check daemon).
After pressing Enter of integrity check daemon, we will see the following output:
3.3- Do you want to run the rootkit detection engine? (y/n) [y]: - Running rootcheck (rootkit detection).
We will press Enter and see this output:
- Do you want to enable active response? (y/n) [y]: - Active response enabled.
After that, we will press Enter to enable active response.
Installation: Firewall-drop response, IP white list, Syslog
When we press Enter here, we will enable firewall-drop response as seen below:
- Do you want to enable the firewall-drop response? (y/n) [y]:
- firewall-drop enabled (local) for levels >= 6
- Default white list for the active response:
- 192.168.15.1
- Do you want to add more IPs to the white list? (y/n)? [n]: n
Here, our Support Engineers recommend entering ‘n’ since we don’t want to add more IPs to the white list.
3.5- Do you want to enable remote syslog (port 514 udp)? (y/n) [y]: - Remote syslog enabled.
We will then press Enter and enable remote Syslog:
- If you want to monitor any other file, just change the ossec.conf and add a new localfile entry. Any questions about the configuration can be answered by visiting us online at http://www.ossec.net . --- Press ENTER to continue ---
After this, we will press Enter in order to start the installation. After the installation we will see this output:
- System is Debian (Ubuntu or derivative). - Init script modified to start OSSEC HIDS during boot. - Configuration finished properly. - To start OSSEC HIDS: /var/ossec/bin/ossec-control start - To stop OSSEC HIDS: /var/ossec/bin/ossec-control stop - The configuration can be viewed or modified at /var/ossec/etc/ossec.conf Thanks for using the OSSEC HIDS. If you have any question, suggestion or if you find any bug, contact us at contact@ossec.net or using our public maillist at ossec-list@ossec.net ( http://www.ossec.net/main/support/ ). More information can be found at http://www.ossec.net --- Press ENTER to finish (maybe more information below). --- - In order to connect agent and server, you need to add each agent to the server. Run the 'manage_agents' to add or remove them: /var/ossec/bin/manage_agents
After OSSEC Installation in Ubuntu
After the installation, run the following command to start OSSEC:
/var/ossec/bin/ossec-control start
This results in the following output:
Starting OSSEC HIDS v2.9 (by Trend Micro Inc.)... Started ossec-maild... Started ossec-execd... Started ossec-analysisd... Started ossec-logcollector... Started ossec-syscheckd... Started ossec-monitord... Completed.
We will also receive an email alert at this point. We will use the mail command to check the email:
[– Message 3 — 27 lines, 663 bytes –]:
From ossecm@localhost Sat Jun 17 21:25:11 2021
Message-Id: <201706171555.v5HFtBJu004798@localhost>
To: <root@localhost>
From: OSSEC HIDS <ossecm@localhost>
Date: Sat, 17 Jun 2021 22:25:11 +0530
Subject: OSSEC Notification – localhost – Alert level 3
OSSEC HIDS Notification.
2021 Jun 17 21:23:57
Received From: localhost->ossec-monitord
Rule: 502 fired (level 3) -> “Ossec server started.”
Portion of the log(s):
ossec: Ossec started.
This ensures us that OSSEC is working fine.
Configuring OSSEC
According to our Support Engineers, the default OSSEC configuration works fine. We can locate the mail configuration file at /var/ossec/etc/ directory.
Next, we will open the main configuration file with this command:
nano /var/ossec/etc/ossec.conf
Here, we come across the E-mail configuration which can be changed when required:
yes
root@localhost
127.0.0.1
ossecm@localhost
Furthermore, OSSEC does not send an alert when we add a new file to the server. We can change this by adding this to the file:
<!-- Frequency that syscheck is executed - default to every 22 hours -->
79200
yes
By default, OSSEC also does not send real-time alerts. We can change this in the list of directories that OSSEC should check:
<!-- Directories to check (perform all possible verifications) --> /etc,/usr/bin,/usr/sbin /bin,/sbin
We will then replace the above two lines with:
/etc,/usr/bin,/usr/sbin /var/www,/bin,/sbin
Then, we will save the changes and close the file.
After this, we will modify the local_rules.xml file located in the /var/ossec/rules directory.
nano /var/ossec/rules/local_rules.xml
We will add these lines to the file:
ossec
syscheck_new_entry
File added to the system.
syscheck,
Finally, we will save the changes and close the file. We verify that the process was successful by restarting ISSEC with the following command and checking for errors:
/var/ossec/bin/ossec-control restart
How to install OSSEC Web UI
- First, we will download the latest OSSEC Wen UI version from the GitHub repository:
git clone https://github.com/ossec/ossec-wui.git mv ossec-wui /var/www/html/
- Then, we will install OSSEC Web UI with this command:
cd /var/www/html/ossec-wui ./setup.sh
- After that, answer the questions as seen below:
trap: SIGHUP: bad trap Setting up ossec ui... Username: admin New password: Re-type new password: Adding password for user admin Enter your web server user name (e.g. apache, www, nobody, www-data, ...) www-data You must restart your web server after this setup is done. Setup completed successfully.
- Finally, we will restart Apache with this command:
systemctl restart apache2
How to test OSSEC
Once OSSEC is up and running, it is time to check if it is working correctly.
We can also make changes to the /etc/aliase and /etc/network/interfaces, /etc/rc.local, /etc/fstab files .
You will receive an email alert after the changes are made. As mentioned earlier, you can check your email with the mail command.
You will see the following alerts while checking emails with Alert level 7:
Integrity checksum changed for: '/etc/aliases' Integrity checksum changed for: '/etc/fstab' Integrity checksum changed for: '/etc/rc.local' Integrity checksum changed for: '/etc/mail/aliases' Integrity checksum changed for: '/etc/mail/aliases.db' Integrity checksum changed for: '/etc/network/interfaces'
We can also check the OSSEC alert via the OSSEC Web UI. Our Support Engineers recommend accessing the UI via http://192.168.15.189/ossec through the web browser as seen below:

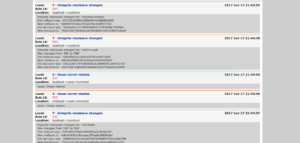
[Looking for further assistance with Server Management? Click here today.]
Conclusion
In short, we learned how to install OSSEC in Ubuntu under the guidance of the skilled Support Engineers at Bobcares.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.







0 Comments