Learn how to restrict SFTP user to a specific Folder. Our Server Management Support team is here to help you with your questions and concerns.
How to Restrict SFTP user to a specific Folder
With security being utterly important in today’s digital world, restricting access to our server via SFTP helps minimize risk.
In other words, we can avoid data breaches and unauthorized access. Today, we are going to take a look at how to set up a secure SFTP environment with OpenSSH’s Chroot Jail mechanism.
By default, SFTP users cannot write to the root directory within a chroot environment. So, we need to direct them to a writable subdirectory or create the necessary folders beforehand. We can do these via either one of these methods:
- For Multiple Users:
We can restrict multiple users to their home directories and then set each user’s home directory to a custom folder.
- For a Single User:
If we need to restrict a single user, we can specify the folder directly in the `sshd_config` file.
How to Set up SFTP Access
- First, we have to create an SFTP group to manage user access:
sudo addgroup sftprestricted - Then, create a new user without a home directory:
sudo adduser --no-create-home USERNAME - Now, we can set the user’s home directory as seen here:
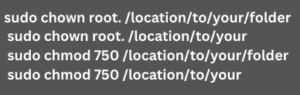
sudo usermod -d /location/to/your/folder USERNAME - Then, make sure we set the correct ownership and permissions:
- Next, we have to disable the user’s shell to disallow SSH shell access:
sudo usermod -s /sbin/nologin USERNAME - After that, we have to add the user to the SFTP restricted group:
sudo usermod -g sftprestricted USERNAME - Additionally, it is a good idea to use key-based authentication for SSH and SFTP connections.
- First, we have to generate a new keypair:
ssh-keygen -t rsa - Then, create the `authorized_keys` file and add the username to it in a directory of our choice:
sudo nano /etc/ssh/user_keys/authorized_keys_USERNAME - Next, ensure proper permissions:
sudo chown USERNAME:USERNAME authorized_keys_USERNAME
sudo chmod 640 authorized_keys_USERNAME - After that, we have to edit the `sshd_config` file to specify the location for the key:
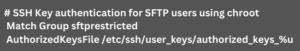
Furthermore, we can use user-specific keyfile location by replacing `Match Group GROUPNAME` with `Match User USERNAME`.
- First, we have to generate a new keypair:
- Then, replace the SFTP subsystem in the `sshd_config` file to use `internal-sftp`:
# override default of no subsystems
#Subsystem sftp /usr/libexec/openssh/sftp-server
Subsystem sftp internal-sftp
This ensures that the SFTP server runs under SSH, improving security.
How to set up the Chroot Jail?
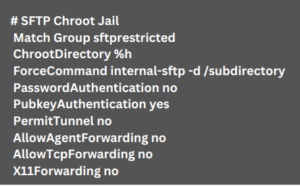
First, configure the Chroot Jail by adding the following lines to the `sshd_config` file:
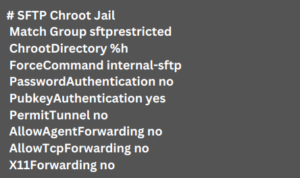
The `ChrootDirectory` directive restricts users to their home directory, and `ForceCommand internal-sftp` ensures that no other commands can be executed. Additionally, this configuration enforces key-based authentication and disables tunneling and forwarding.
How to Permit Users to Write to the Chrooted Folder
If we need users to write to their root folder within the Chroot Jail, we can modify the `sshd_config` like this:
Let us know in the comments if you need further help with restricting SFTP user access to a specific folder.
[Need assistance with a different issue? Our team is available 24/7.]
Conclusion
In brief, our Support Experts demonstrated how to restrict SFTP user to a specific Folder
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.







0 Comments