Learn how to resolve the X-Authentication-Warning in Sendmail. Our Sendmail Support team is here to help you with your questions and concerns.
How to Resolve X-Authentication-Warning in Sendmail
The X-Authentication-Warning is a special header inserted by Sendmail to highlight potential security concerns during email transmission. This warning appears when Sendmail detects actions that could indicate unauthorized email manipulation.
Today, we will look at its causes and solutions to help prevent email delivery issues and maintain security.
What Triggers the X-Authentication-Warning?
This warning occurs when PrivacyOptions includes `authwarnings`, and certain actions occur, such as:
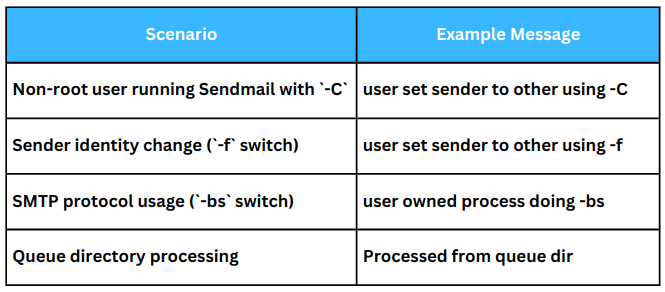
- A non-root user runs Sendmail with the `-C` switch to specify a custom configuration file.
- A user changes the sender’s identity using the `-f` switch.
- A user processes mail from a different queue directory.
- A user uses the `-bs` switch to receive mail via the SMTP protocol.
Understanding the Warning Format
The warning typically follows this structure:
X-Authentication-Warning: hostname: message
Here, Hostname is the canonical name of the host inserting the header. The message is the details about the authentication concern.
Common Message Variations
Causes and Fixes for X-Authentication-Warning
1. Non-Root User Running Sendmail with `-C` Switch
A non-root user attempts to run Sendmail with a custom configuration file.
Click here for the Solution.
This can be solved by adding the user to `/etc/mail/trusted-users` and adjusting permissions for the configuration file.
- Open `/etc/mail/trusted-users` with root privileges.
- Then, add the specific username.
- Set file permissions: `chmod 640 /etc/mail/trusted-users`.
- Then, add `FEATURE(use_ct_file)` in `sendmail.mc`.
- Restart Sendmail to apply changes.
2. Sender Identity Change with `-f` Switch
A user changes the sender’s identity without being in the trusted users list.
Click here for the Solution.
This can be solved by adding the user to the trusted users list and modifying the Sendmail configuration.
- Edit `/etc/mail/sendmail.cf` and add the user using the `T` configuration command.
- Then, add the username to `/etc/mail/trusted-users`.
- Verify with `sendmail -bt -d0.1`.
- Finally, ensure proper file permissions and ownership.
3. SMTP Protocol Usage with `-bs` Switch
A user or program receives mail via SMTP without proper authorization.
Click here for the Solution.
This solution involves adding the user to the trusted users list, modifying `PrivacyOptions` to exclude `authwarnings` and ensuring proper SMTP configuration.
- First, add the user to `/etc/mail/trusted-users`.
- Then, modify `PrivacyOptions` in Sendmail’s configuration.
- Use `authwarnings` strategically.
- Finally, verify SMTP daemon settings.
4. Processing Mail from a Different Queue Directory
A non-root user processes mail from an unauthorized queue directory.
Click here for the Solution.
This solution involves granting appropriate permissions and configuring consistent queue directory access.
- First, set queue directory permissions using `chown` and `chmod`.
- Then, create a specific group for mail processing.
- Add users to this group.
- Finally, modify Sendmail’s configuration to recognize alternative queue directories.
5. Hostname Mismatch in SMTP Conversation
The remote host specifies a canonical name that does not match DNS or system configuration.
Click here for the Solution.
This solution involves verifying DNS settings, configuring the `$j` macro in Sendmail, and ensuring consistent hostname resolution.
- First, check `/etc/hosts` and DNS settings with `nslookup` and `dig`.
- Configure `$j` in Sendmail.
- Then, validate reverse DNS (PTR) records.
- Finally, use `hostname -f` to confirm the fully qualified domain name (FQDN).
6. Email Clients (e.g., Pine) Triggering Warnings
Email clients like Pine invoke Sendmail with specific options that trigger warnings.
Click here for the Solution.
Here, we will remove the `user-domain` value in the client configuration, adjust client SMTP settings and configure Sendmail to use default masquerading.
- First, remove `user-domain` from Pine configuration.
- Adjust SMTP settings in the email client.
- Then, set `FEATURE(masquerade_entire_domain)` in `sendmail.mc`.
- Finally, verify SMTP authentication settings.
Prevention Strategies
To prevent X-Authentication-Warning issues in the future:
- Regularly update Sendmail configurations.
- Also, implement strict access controls.
- Use robust authentication mechanisms.
- Additionally, monitor mail logs consistently.
- Maintain accurate trusted user lists.
Key Recommendations
- Always use root or trusted user identities for email transmission.
- Also, implement proper authentication mechanisms.
- Additionally, regularly audit email configurations.
- Furthermore, use secure, encrypted communication channels.
[Need assistance with a different issue? Our team is available 24/7.]
Conclusion
Understanding the X-Authentication-Warning header and applying these fixes can improve the email system’s security and prevent unnecessary alerts in Sendmail logs.
In brief, our Support Experts demonstrated how to resolve the X-Authentication-Warning in Sendmail.







0 Comments