Are your servers a possible target of sudo vulnerability? Fix it now!
The latest sudo vulnerability CVE -2019-18634 allows hackers to execute commands as the root user. Here, it uses the sudo feature pwfeedback as the backdoor.
At Bobcares, we always strive to keep the servers secure against all the known vulnerabilities as part of our Server Management Services.
Today, let’s see how our Support Engineers deal with this sudo vulnerability.
What is this sudo vulnerability?
Let’s now check more details on the vulnerability reported with sudo on January 30, 2020.
This is the one that allows the attackers to gain access to our root privileges. Further, the hacker can execute the programs with the security privileges of a superuser.
This is dangerous. The sudo package version from 1.7.1 to 1.8.30 is under risk. Fortunately, it affects servers that have the pwfeedback feature enabled.
The affected server list will be big since sudo is a default package that comes with most server distributions.
What is this pwfeedback option for?
Now comes the question of why we need a pwfeedback option in sudo.
This option is used for providing visual feedback for users. It prints an asterisk for each key when a user is inputting his password.
Unfortunately, “pwfeedback” works as the door for the hackers to enter on vulnerable servers.
Hackers make use of this option and trigger a stack-based buffer overflow in the privileged sudo process. Finally, the malicious attacker can execute any program they need just like the most privileged user on the server.
Is my server under risk?
Yes, maybe.
Luckily, there is no need to waste too much time to confirm the risk for the sudo package. Here is the way we use to check whether the servers are safe.
1. Check for pwfeedback option
As we already saw, it all depends on whether the server uses the pwfeedback option. If the pwfeedback option is set in your /etc/sudoers file, then yes your servers are at risk.
Upgrading the sudo package to 1.8.30 and above helps to tackle this vulnerability.
Today, let’s discuss how our Support Engineers mitigate sudo vulnerability and check whether our servers are safe.
We recently found that one of our customer’s server was under risk. We tested this by checking whether the pwfeedback option is enabled or not.
sudo -l
It was enabled and got an output like the one shown below:
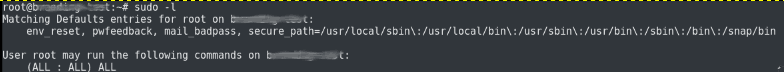
In such cases, we have to check our sudo version and confirm whether it is 1.8.30 or above.
2. Verify sudo version
Here, the customer was having an Ubuntu server. For checking the sudo version, we used the command below:
apt-cache policy sudo
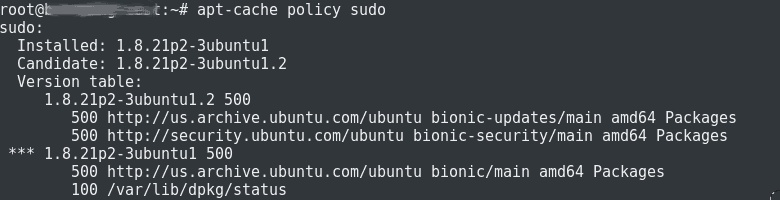
Here, the version shows as 1.8.21p2-3ubuntu1 with the pwfeedback enabled. Then, our Engineers confirmed that the server was at risk.
The solution here is to either disable the pwfeedback option or upgrade the server. As the customer wanted pwfeedback option enabled, we upgraded his server using:
sudo apt-get update
However, when the customer does not need the pwfeedback option, we always make sure to disable it in sudo by using the command,
visudo
Then we change:
Defaults pwfeedback To: Defaults !pwfeedback
That protects the server from the sudo vulnerability.
[Clueless about the sudo vulnerability status of your server? Our experts can help you.]
Conclusion
In short, we can resolve sudo vulnerability by disabling pwfeedback and upgrading the sudo package. Today we saw how our Support Engineers keep up the server against known vulnerabilities.







0 Comments