Cloudflare access for AWS SSO allows users to sign in once with a single set of credentials and gain access to all enabled apps.
Bobcares responds to all inquiries, large or small, as part of our AWS support service.
Let’s look at the details of Cloudflare access for AWS SSO.
Cloudflare access for AWS SSO
AWS SSO does not typically require any additional apps, certificates, or complicated installations; everything is done through a web browser. Furthermore, SSO simplifies the job of administrators by providing a centralised system for managing user accounts, assigning and removing access to specific apps, and monitoring risk.
Cloudflare Access for SaaS enables us to layer additional network and device posture policies on top of our identity provider’s existing identity authentication. In this example, Okta is used as the identity provider, but any supported identity provider can be used.
Configure AWS
- Firstly, login to the AWS admin panel.
- Then, search for SSO.
- Then, link the AWS account to AWS Single Sign On.
- Select an identity source by clicking the Choose an identity source button.
- Then, switch the identity provider to External Identity provider.
- Then, select Show individual metadata values from the drop-down menu. These are the fields that will be included in the Cloudflare Access for SaaS app.
- Finally, copy the AWS SSO ACS URL.
Configure Cloudflare
- Firstly, open the Zero Trust Dashboard.
- Then, go to Access > Applications.
- Then, to begin creating a SaaS application, select SaaS as the application type.
- Copy the following AWS account fields and paste them into the Zero Trust application configuration:
AWS value.
Cloudflare value.
URL for AWS SSO ACS.
Assertion Consumer Service URL
URL of the AWS SSO Issuer
Entity ID - Email must be selected as the Name ID Format.
- The IdP can then pass additional Attribute Statements to AWS SSO.
- Then, Copy and save the Cloudflare IdP metadata values for the final AWS configuration.
- Then, Click Next
- Make an Access policy to control who has access to our application.
- Finally, return to the AWS SSO dashboard after saving the policy.
Complete the AWS configuration
- Firstly, Copy the Cloudflare IdP metadata and paste it into the AWS account with these mappings.
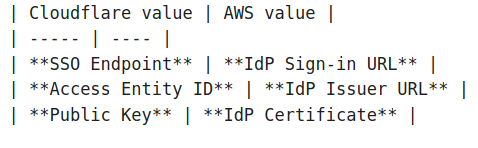
- Then click the Next: Review button.
- Finally, set Provisioning to Manual.
Check the connection
The user should now be able to log in successfully. Open the user portal URL to test the connection.
[Looking for a solution to another query? We are just a click away.]
Conclusion
To sum up, our Support team went over the details of Cloudflare access for AWS SSO.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.







0 Comments