Recently we came across a support request regarding Duplicity restore full backup as a part of our Server Management Services.
Duplicity is a common application to generate backups. A full account restoration would be necessary to recover and to get the business going again after an unpredicted catastrophic event.
Today, let us discuss in detail Duplicity and how our Support Engineers perform restorations with Duplicity.
What is Duplicity?
Let’s start with a basic understanding of Duplicity. We can use it to generate digitally signed, encrypted incremental backups. It works well with Unix like operating systems.
Duplicity backups can be stored locally as well as in remote locations like S3, SFTP, and WebDAV. Deja-dup is the graphical user interface for Duplicity in Ubuntu.
Installation of Duplicity Backup
We can install Duplicity easily using the following command in the terminal window:
sudo apt-get install duplicity
Sometimes we need the NcFTP package to use the Duplicity FTP backup. To install the same, we run:
sudo apt-get install ncftp
In addition, we need to create the backup directory at the remote server.
mkdir -p /remote_backup_directory
Generally, our Support Engineers uses SFTP to transfer the Duplicity backups to remote locations.
SSH keys need to be set up with both the servers to perform a password-less transfer.
To set up an extra layer of security, we can use GPG. To generate the key, we run:
gpg –gen-key
It will ask for a few details like the type of key, name, email address, and optionally, a comment associate with this key. It also asks for a passphrase, which we should set to ensure proper encryption.
Once the key is generated, it displays the public key on the screen. We can also retrieve it by using the command:
gpg –list-keys
Duplicity full backup setup
The syntax to generate backup using gpg is as follows:
PASSPHRASE=”passphrase_we_set_for_GPG” duplicity –encrypt-key public_key –exclude /proc –exclude /sys –exclude /tmp / sftp://root@backupdomainhost//remote_backup_directory
Once this is done the backup folder in the remote server will fill with the backups as shown below:
The script below may help if we prefer a full server backup with no encryption via rsync.
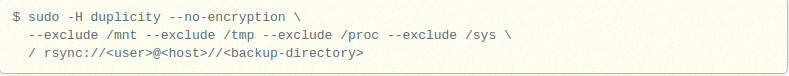
The above command by default generates incremental backups. To make it generate a full backup of the server, we can use the option full with it.
duplicity full –no-encryption –exclude /mnt –exclude /tmp –exclude /proc –exclude /sys / rsync://username@domainname.com//<backup-directory>
Then to run these backup tasks periodically, a cron job can be set at the source server end. We can use either of the options to remove older backups from the remote backup host:
remove-all-but-n-full count: Delete all backups sets that are older than the count. If the count is 2, it retains only 2 recent backups and deletes all others.
remove-older-than time: Delete all backup sets older than the given time. Old backup sets will not delete if backup sets newer than time depend on them
Duplicity restore full backup
Restoration from the Duplicity backup is easy. We just need to interchange the remote and local parameters. A restore with backup can perform using the command below:
PASSPHRASE=”passphrase_we_set_for_GPG” duplicity sftp://root@domainname.com//path_of the_backup
To restore a single file using duplicity, we can go for the command below:
PASSPHRASE=”passphrase_we_set_for_GPG” duplicity –file-to-restore /path/to/file sftp://root@domainname.com//path_of_the_backupfile /path/to/restore/file
By default, the files already present in the server won’t be restored. Alternatively, for the restoration to complete successfully, either delete the file prior to running the script or use a different path or file name.
[Couldn’t finish the backup? We’d be happy to assist you]
Conclusion
In short, Duplicity is an efficient backup application. Today we discussed simplified steps to configure Duplicity backup and how our Support Engineers perform a Duplicity-restore full backup.







0 Comments