Let us learn how to resolve the error loading sso token expired in aws with the support of our AWS support services Bobcares.
Error: Error loading SSO token expired in AWS
If a user finds problems when performing Amazon CLI commands, they should make sure they are using the most recent AWS CLI version.
In order for temporary security credential requests to reach AWS endpoint.
nts, the user must sue.
To establish credentials for a position, you must use an access key ID, a secret access key, and a session token. The AWS endpoint must receive requests within five minutes of their timestamp, or it will reject them
Resolve Error: error loading sso token expired in AWS
Using Profiles to assume an IAM Role
A profile with a name is a set of settings and credentials that we can use with an AWS CLI command. We must ensure that we are utilizing the proper credentials.
We can use the default profile credentials in the following AWS CLI command:
aws s3 lsThis example command makes use of the project1 profile credentials set in the.config file:
aws s3 ls --profile project1Using expired credentials as an example:
"An error occurred (ExpiredToken) when calling the ListBuckets operation: The provided token has expired."The profiles are in the.aws folder, which also contains the.credentials and.config files.
For Linux/macOS, the config file is at ~/.aws/config and for Windows users it is at C:\Users\%USERPROFILE%\.aws\config.
To verify the default profile credentials, use the following command:
aws configure list --profile defaultExample:
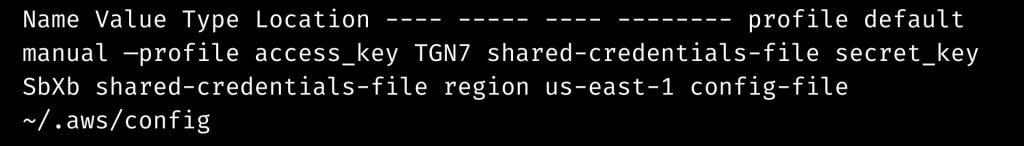
Run the following command to ensure that we use the same credentials for the profile project1.
aws configure list --profile project1Example:
Name Value Type Location ---- ----- ---- -------- profile project1 manual —profile access_key QN2X config-file secret_key LPYI config-file region eu-west-1 config-file ~/.aws/configPlease keep in mind that the default and project1 profiles may have distinct credentials as shown in the example output.
In the .aws/config file, we may construct a profile in the following format:
[profile project1] region = eu-west-1 aws_access_key_id = access-Key-for-an-IAM-role aws_secret_access_key = secret-access-Key-for-an-IAM-role aws_session_token = session-tokenThese credentials are sent to us when we execute the AWS STS assume-role command, which looks like this:
aws sts assume-role --role-arn arn:aws:iam:::role/Prod-Role --role-session-name environment-prodExample output:
{ "AssumedRoleUser": { "AssumedRoleId": "AROAXXXXXXXXXXXX:environment-prod", "Arn": "arn:aws:sts::account-number:assumed-role/Prod-Role/environment-prod" }, "Credentials": { "SecretAccessKey": "secret-access-Key-for-an-IAM-role, "SessionToken": "session-token", "Expiration": "2020-03-31T17:17:53Z", "AccessKeyId": "access-Key-for-an-IAM-role"}Note: Using the DurationSeconds option for the use case, we may enhance the maximum session length expiry for temporary credentials for IAM roles.
Following that, the new assume-role API call receives a new set of valid credentials. We must manually update the /.aws/config file with the new temporary credentials after the API request.
We can avoid having to update the configuration file every time a session expires.
In the /.aws/config or /.aws/credentials file, provide a profile for the IAM role and the person who assumes the role, similar to this:
[profile project1] role_arn = arn-of-IAM-role source_profile = user1 region = regionIt is worth noting that user1 is specified in the /.aws/credentials file in the following way:
[user1] aws_access_key_id=AKIAIOSFODNN7EXAMPLE aws_secret_access_key=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEYBy specifying the source_profile, we avoid having to change the temporary credentials in the /.aws/config or /.aws/credentials files.
The AWS CLI command listed below lists the Amazon Simple Storage Service (Amazon S3) buckets with credentials for user1 in the /.aws/credentials file.
aws s3 ls --profile project1Consider the AWS CLI with a source_profile attribute; the API call assume-role stores credentials in the.aws/cli/cache file.
In the.aws/cli/cache file, expired credentials are immediately updated. If we get an error about expired credentials, we may clear the cache using the commands:
Linux/macOS:
$ rm -r ~/.aws/cli/cacheWindows
C:\> del /s /q %UserProfile%\.aws\cli\cacheThe AWS CLI will generate new credentials in cache.
Create environment variables to assume the IAM role and then verify access
We may utilize IAM role credentials to generate three environment variables to assume the IAM role, as shown below:
For Linux/macOS:
export AWS_ACCESS_KEY_ID=RoleAccessKeyID export AWS_SECRET_ACCESS_KEY=RoleSecretKey export AWS_SESSION_TOKEN=RoleSessionTokenFor Windows:
C:\> setx AWS_ACCESS_KEY_ID RoleAccessKeyID C:\> setx AWS_SECRET_ACCESS_KEY RoleSecretKey C:\> setx AWS_SESSION_TOKEN RoleSessionTokenRun the following command to ensure that we have the right IAM role:
aws sts get-caller-identityThe get-caller-identity command returns details about the IAM identity that was used to authenticate the request.
Environment variables retain temporary cached credentials even after their expiration and lack automatic refreshing. To check if credential environment variables are set, execute the following commands.
Linux/macOS:
$ printenv | grep AWSWindows:
C:\set AWSThe following commands can be used to delete expired environment variables:
For Linux/macOS:
$ unset AWS_ACCESS_KEY_ID
$ unset AWS_SECRET_ACCESS_KEY
$ unset AWS_SESSION_TOKENFor Windows:
C:\set AWS_ACCESS_KEY_ID= C:\>set AWS_SECRET_ACCESS_KEY= C:\set AWS_SESSION_TOKEN=We can now use the assume-role API request to obtain new, valid credentials and reset the environment variables.
[Need assistance with similar queries? We are here to help]
Conclusion
To sum up we have now seen how to resolve the error loading sso token expired in aws with the support of our tech support team.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.







0 Comments