DNS is the basis of most internet applications – emails, messengers, web site browsing, etc. But we often tend to miss out the presence of this extensively used service. As a result, server administrators overlook the vulnerabilities in dns service and hackers easily exploit this aspect.
The security of a server includes securing all its server software and application software, file system, network and physical security. We’ve already covered the entire list in our previous post. Today, we’ll take a more focused look at how to secure dns server.
Read more at : How to secure a server

How to secure dns server
1. Protect server information
Every server software has a version number associated with it. Attackers can easily identify the DNS server version from a simple DNS lookup information and easily find the vulnerabilities of that version and attack the DNS server.
Hiding the software version information increases the effort a hacker would have to put, in order to attack the DNS server. This would make the attack a hard thing to do and thus help to protect the DNS server.
2. Limit recursive queries
A DNS server that handles recursive queries forwards the DNS queries to other DNS servers, if they don’t have the records with them. Too many recursive queries can hog the server memory.
An open DNS server accepts queries from everyone, which can lead to malicious users querying the DNS server. This often leads to risks such as DOS attacks and Cache poisoning.
DOS attacks cause network traffic to be clogged by sending too many requests to the DNS server, making it unresponsive. In cache poisoning, attackers send specific queries to DNS server and gains control over server traffic.
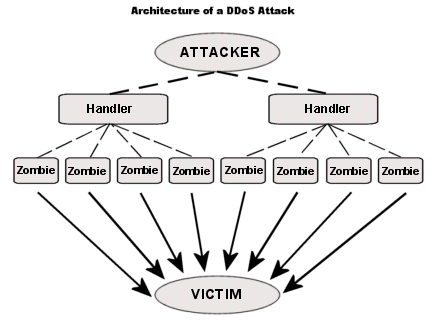
Attackers send multiple queries simultaneously to the victim server.
One way which we can limit recursive queries is by configuring a closed DNS server, which accepts queries only from a trusted set of clients. We can also limit the number of clients that are served concurrently by the DNS server or turn off recursive queries.
Read: Fix for DOS vulnerability in DNS servers
3. Run the server as non-privileged user
When a DNS server runs as a privileged user such as root, an attacker who gains access to the DNS server can crack other processes also by misusing the privileges of the super-user account.
To prevent such a misuse, DNS server is usually run as a non-privileged user. Therefore, even if the DNS server gets hacked, the hacker will be confined to DNS processes only and won’t be able to breach into other services.
4. Restrict zone transfers
By default, the DNS zones can be transferred from the dns server to other hosts. But this is a highly insecure practice that renders the zones public and vulnerable to attacks by outsiders.
DNS zone transfers should therefore be limited to only a certain set of trusted slave DNS servers and all other hosts should be prevented from doing bulk transfers.
Read: Avoid spamming using anti-spamming DNS records
5. Use DNS Security Extensions (DNSSEC)
An attacker who manages to hijack the DNS lookup process can redirect the user traffic to their malicious site and collect confidential information from users or provide them with fraud results. To protect from such attacks, a technology called DNSSEC is used.
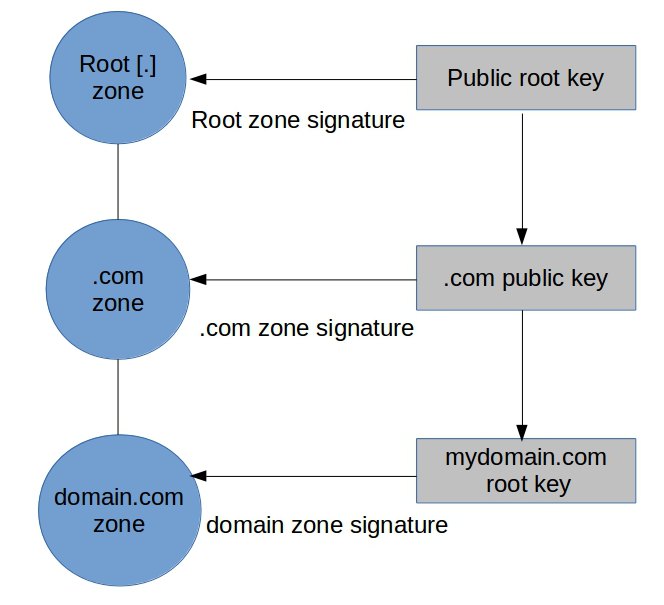
DNSSEC security extensions for DNS zones
In DNSSEC, the validity of DNS data is assured by digitally signing it. A third party signing authority such as ICANN can validate the DNS zones so that users can confirm its authenticity.
Deploying DNSSEC security extensions can help users to confirm that they are connecting to the right DNS server and thus prevent DNS spoofing.
Read: An introduction to DNSSEC
6. Update the server always
Any outdated software is often vulnerable to attacks. For instance, BIND DNS software versions 4 and 8 are highly insecure and prone to attacks. That makes it important to always update the server software.
New software versions that address the security risks of the previous versions should be tracked and installed in the server to wade off attackers. Subscribing to software security updates and other security mailing lists helps in prompt updates.
Read: How to keep the server updated
In short..
Thousands of servers get hacked every month due to software vulnerabilities. By protecting the DNS server with the 6 best practices as we discussed here, it is possible to secure the server from many attacks.
Bobcares helps online businesses of all sizes achieve world-class security and uptime, using tried and tested solutions. If you’d like to know how to make your server more reliable, we’d be happy to talk to you.
For as low as
$74.99/server/mo
Get full spectrum infrastructure management services – including setup, monitoring & maintenance.
Never again face a critical business downtime. We keep your servers secured, optimized and updated at all times. Our engineers monitor your servers 24/7 and fix issues before it can affect your customers.







0 Comments