WordPress takes security very seriously. WordPress releases “minor” revisions regularly to address even vulnerabilities reported just hours before. Latest WordPress websites have automatic background updates to prevent any possible exploits.
Even with such a proactive approach towards security, news vines are flush with reports of WordPress sites affected with one vulnerability or another. So, what’s the deal here? How can you ensure a secure WordPress hosting for your customers?
In our role as Outsourced hosting support specialists for web hosts, our key priority is to help them provide a secure hosting environment for WordPress sites, which enables them to retain their customers better.
See how we help WordPress hosting companies
Checklist for a secure WordPress hosting
Listed here are the common ways in which WordPress sites are hacked.
-
- Exploiting unpatched WordPress vulnerabilities
- Exploiting unaddressed vulnerabilities in themes and plugins
- Exploiting undetected vulnerabilities in hosting environment
- Using stolen login credentials
Now let’s address each of these issues one by one and look at the solutions available to mitigate them. I’m going to lay off using plugins as much as possible because even security plugins are known to have vulnerabilities.
We’ll employ defense in depth (or multi-layered defense), security by obscurity (denying target information), access restriction and penetration testing in this checklist.
1. Securing WordPress core
As mentioned earlier, WordPress is serious about security, and come bundled with a lot of security options that works out of the box. Along with it, we’ll add a few hosting level security to make your WordPress extra secure.
Use non-standard table prefix
By default WordPress uses “wp_” as a prefix for all tables. Mass SQL injection exploits depend on this prefix to work. So, we change this at installation time to something else, like “mysite_”, as a good hedge against undisclosed exploits.
Put wp-config.php outside document root
Due to vulnerabilities in hosting environment, hackers might be able to download wp-config.php, thereby disclosing the database login details. WordPress by default looks at the parent directory for wp-config.php. So, we move it out of there, for an additional layer of security.
Remove “admin” user
Most brute force attacks just focus on getting the password of “admin” user. We work around this angle of attack by creating another user with administrative privilege and re-assigning all posts of “admin” to the new user and deleting the “admin” user.
[ You don’t have to lose your sleep over hosting security. Our expert hosting support specialists are online 24/7/365 to help you provide secure services. ]
Password protect “wp-admin” directory
Most brute force attacks depend on “wp-admin” folder being readily accessible. We password protect the “wp-admin” directory using .htaccess file, to blunt those attacks and thus provide a two-layer security to the admin interface.
Lock down files and directories
We conduct a detailed inspection in the server for insecure files and folders. Permissions of all files and directories are limited to 644 and 755 respectively. This helps us to shunt many malware upload attempts.
Replace default WordPress security keys
WordPress uses password “salts” to improve encryption in visitor’s cookies. It’s trivial for hackers to determine the default keys shipped with each version. So, we get a different set of keys and replace the old ones in the wp-config.php, as a security measure.
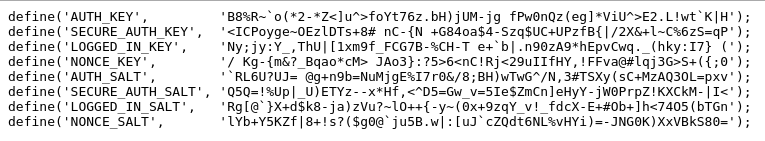
WordPress secret key
Update WordPress on the release date
Do not wait till later. We upgrade the WordPress as soon as we see the message “WordPress XX.YY is available! Please update now” in the admin panel. Custom themes and plugins in some sites can get messed up with auto-update settings. To ensure zero downtime upgrades, we first test the upgrade in our staging server, before rolling it out into the live.
Disable file edit via admin panel
Plugin and theme editor in the WordPress admin panel is a favorite tool used by hackers to insert malicious code into websites. We disable that editor by updating the wp-config.php and allow only edits via restricted access.
Disable pingbacks and trackbacks
If not absolutely necessary to your service offering, we consider disabling pingbacks and trackbacks in the servers, as these can be used by attackers for DDoS attacks against your sites.
Enable comment moderation
Some kinds of attack relies on directing visitors to a malicious website through a comment link. Holding the comments for moderation is a good hedge to that.
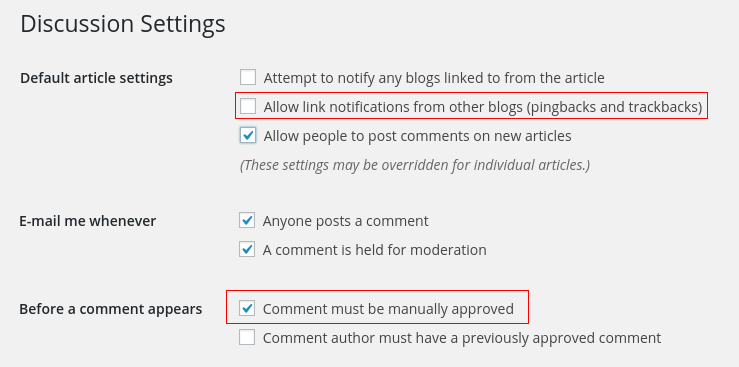
Disable pingback requests and moderate comments
Clean out docroot and user list regularly
It is common to see .sql files, .tgz files, backup files, etc. in document root, and they are an easy way for hackers to gain critical information or even access to your database. By auditing the servers periodically, we detect and delete all files and accounts that aren’t essential.
[ Use your time to build your business. We’ll take care of your servers. Hire our hosting support experts to maintain your servers secure and stable 24/7 . ]
2. Securing WordPress themes and plugins
A look at the OSVDB WordPress vulnerability list shows that 554 out of 562 vulnerabilities reported in 2015 are from a third party theme or plugin. That’s 98.6% of all WordPress vulnerabilities. It’s an indicator of how big a security risk it is when you decide to install an additional theme or plugin in your site. Let’s take a look at how you can mitigate the risk from third party integrations.
Minimize third party integrations
Keep the number of themes and plugins installed in your site to a minimum. We audit the plugin features and recommend only the best suited ones for the server security and performance. With our custom security scripts, we’ve been able to by-pass some plugins that can tamper with the security.
Use only professional, reputable, well-maintained plugins and themes
Keeping a piece of software is hard work. It takes time and effort. As a site maintainer, it’d be safe for you to use only those themes and plugins that meet the criteria below:
- That is published in WordPress.org. This makes sure that the theme or plugin won’t have malware.
- That is updated frequently. If it hasn’t had an update in the past 6 months, think twice about using it.
- That doesn’t have a long history of vulnerabilities. Just google for “[plugin name] vulnerability”, and see the list for yourself.
- That is recommended by a lot of people. The more reputable a plugin is, the more the programmer has a stake in ensuring its quality.
- That is paid and supported by a reputable group.
Update on the day of patch release
I can’t stress this enough, but I guess you get the point. We keep a close watch on the available updates, and upgrade the plugins and themes as soon as a patch is available. For sites without custom codes, we configure auto-updates for critical security releases.
3. Hosting environment security
If you are a webmaster with access to a VPS, cloud instance or a dedicated server, or if you are a hosting service provider yourself, this section is applicable to you. We’ll go through all that we do at the hosting level to improve security.
Review general server security
There’s a lot that can be said about general server security, the main points here that needs to be checked off are:
- Strict server update regime. As soon as an update it available it should be installed.
- A well configured firewall. Something like CSF or APF would do.
- Turn off server signatures to deny access to server software information.
- Brute force attack detection and prevention. Something like BFD should do.
- DoS mitigation steps. Something like mod_evasive should be OK.
- Configure webserver to limit the access of one user is limited one docroot. Eg: Use SuPHP or mod_ruid2.
- Anti-spam security that prevents open relay, mail rate limit, outgoing filtering and incoming filtering.
- Basic network and file system security. Proper permissions to make sure people get to only those places they are supposed to.
At Bobcares, our server security specialists follow a detailed checklist that covers all aspects of server security and provide a 360 degree protection to your WordPress hosting services.
Secure your database access
Selecting a complex username and password for the WordPress database and granting access to the user with only the minimum required privileges – SELECT, INSERT, UPDATE and DELETE – are two security measures for DB access.
Disable dangerous PHP functions
There are a few favorite PHP functions used in exploits. We disable them to prevent execution of malware. These include:
disable_functions=exec,passthru,shell_exec,system,proc_open,popen,curl_exec,curl_multi_exec,parse_ini_file,show_source allow_url_fopen=Off allow_url_include=Off
Block malware uploads using scanners
Open source malware scanners go a long way in detecting malware before it can pose a threat to your site. ClamAV and Linux Malware Detect (LMD) are a couple of good ones we use. After clubbing the virus databases of these together, we even beef them up with custom security rules for enhanced protection.
Block exploit attempts using a Web Application Firewall
A properly configured WAF such as mod_security, will block a lot of exploit attempts, brute force and comment spam before they reach your site. To make it even more secure, we link it up with a malware scanner enginer (like ClamAV) so that each upload will be scanned for malware signature.
Block XMLRPC attacks
We block XMLRPC attacks by adding specific rules in mod_security in the web server.
Monitor file changes
We use “Real-Time Monitoring” features such as Linux Malware Detect (LMD), to monitor the files in your WordPress docroot, and notifies when a file is changed. This helps us to detect and delete malware uploads via stolen FTP passwords.
Configure backup, verify integrity daily
We configure a reliable backup system to backup the files and database at least once a day. Using test restores on a periodic basis, we confirm the backups are reliable and complete.
Scan for vulnerabilities
We take a pro-active approach in detecting vulnerabilities with your website, using scanning tools like WPScan and Nikto. For example, a sample WPScan output looks like this:

WordPress vulnerability scanning using WPScan
There’s more that can be done, like blocking out all no-referrer accesses, enabling two factor authentication, blocking IP ranges, etc. But, we’ll limit our hardening steps to what doesn’t have negative side effects.
4. Mitigating user level vulnerabilities
It is said that security is only as strong as the weakest link, and we’ve seen that users with inadequate awareness of security is a big risk. As a webmaster or service provider there isn’t a lot that you can do to prevent your users falling prey to phishing, or getting key loggers installed in their laptops.
But with a combination of server policies and education, you can mitigate a few of those risks. We’ve covered some of that in earlier sections, like automatic core updates, file upload scanning, etc. We’ll cover the rest here.
Educate about strong passwords
The oldest, yet one of the most vulnerable hacker entry points is user access. People tend to choose passwords they can easily remember, and that’d usually be a variation of their username, publicly available information or dictionary words.
From v4.3, WordPress generates a strong password for the user by default. We always encourage customers to use that.

Generate strong passwords in WordPress
Educate about phishing and computer security
Put up a page on your site listing the common phishing scams and how hackers can install keyloggers and RATs on laptops. Encourage them to update their software frequently and to use a personal firewall + anti-virus on their system.
Enforce SSL
One common way for hackers to get passwords is by snooping on insecure WiFi hotspots. You can blunt that by enforcing SSL for admin access.
Restrict plugin installs
If your business model can afford it, restrict new installs of plugins and themes. In services like managed WordPress hosting, this is possible.
That’s about it. With these points, you can ensure a pretty secure WordPress installation for your customers. There’s of course more than can be done to beef up security even further (security plugins, third party malware monitoring, etc.), but doing the above should lock down your WordPress pretty tight.
Bobcares server administrators routinely help webmasters and service providers keep their servers secure and responsive. Our server management services cover 24/7 monitoring, emergency administration, periodic security hardening, periodic performance tuning and server updates.
If you’d like to know how to secure your WordPress hosting infrastructure, feel free to contact us.





If we go for Cloudways Platform, these Security are already assembled in it. Bob try Cloudways Platform.
Thanks for the heads up Fahad. Do you have specific information on file upload monitoring?