Let us learn more about installing and configuring Mod_Security on Windows Server. With the support of our Server management support services at Bobcares we will now learn how to set up mod_security.
How to install and setup Mod_Security on Windows Server?

ModSecurity is an open source web application firewall that has been widely setup on Apache-based web servers to protect web applications against security vulnerabilities.
It was recently made available in a stable version for IIS-based servers starting with version 7.X.
Installing and configuring Mod_Security on Windows Server
Follow the steps given below to install the mod.
- Firstly, connect to the Windows Server through RDP, open a browser, and save Microsoft’s Web Platform Installer (WebPI)
- Install the following Visual Studio 2010 Runtimes before setting up the ModSecurity:
A: If the user has a 32-bit operating system (Windows Server 2008 or IIS7), only the 32-bit runtimes will be installed.
B: * Nevertheless, if the user is running a 64bit operating system and running both 32bit and 64bit application pools, the user should install both the 32bit and 64bit versions.
- After that, ModSecurity had a missing dependancy “Wlanapi.dll” This was installed by installing the “Wireless LAN Service” as follows:
A) Launch Server Management.
B)Choose Features | Insert Feature
C)Choose Wireless LAN Service
D)Install, shut off, and call it a day.
- Finally, launch Microsoft’s Web Platform Installer (WebPI) and install ModSecurity. The user must load the webpage and ensure that it loads.
The user should also examine the application log and ensure that mod security is enabled. Administrator Tools >> Event Viewer >> Windows Logs >> Application.
If not, just restore the user’s applicationhost.config file. Remove the three ModSecurity lines, or go to c:inetpubhistory and restore the most recent backup of the applicationhost.config file into c:windowssystem32inetsrvconfig. This patches up the first major step in installing and configuring Mod_Security on Windows Server.
Setting up the ModSecurity Ruleset
- Place the ModSecurity ruleset in the directory c:inetpubwwwrootowasp crs.
- In the above-mentioned folder, open modsecurity.conf and change the first line from SecRuleEngine DetectionOnly to SecRuleEngine On.
- Next, build a test rule. SecRule ARGS, “zzz” phase:1,log,deny,status:503,id:1 and add it at the end of the modsecurity.conf file.
Activating ModSecurity on our website
- Administrator privileges are required to access IIS.
- Enable the VPS local host.
- Launch the Configuration Editor.
- The user must now utilize the Configuration Editor to enter their Websites webconfig file and add the following rule.
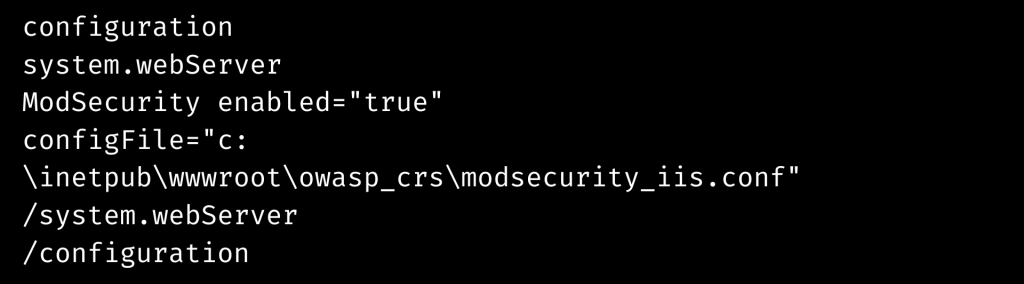
Finally, relaunch the local host. Now move to the next step in installing and configuring Mod_Security on Windows Server.
Verifying ModSecurity’s loading and finding problems
- After setting up the ModSecurity, the user may test its loading by using our test rule. The user may verify this by visiting http://www.mydomain.com/index.php?a=zzz.
- When the website loads, the user receives the notice “The service is unavailable.”
- Access server users can inspect the application log (Administrative Tools – Event Viewwer – Windows Logs – Application).
- The user will receive the following information:
This is the final step in setting up the Mod_Security on Windows Server.
[Need assistance with similar queries? We are here to help]
Conclusion
To sum up we have now seen more on setting up the Mod_Security on Windows Server. With the support of our Server management support services at Bobcares we have now gone through the whole setup process.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.







0 Comments