We can quickly fix the “Kubernetes x509 Certificate has Expired” error with this latest blog. As part of our Kubernetes Support, Bobcares provides answers to all of your questions.
Overview
- Resolving “Kubernetes x509 Certificate has Expired” Issues
- Understanding the Causes
- Step-by-Step Solution
- Preventative Measures
- Conclusion
Resolving “Kubernetes x509 Certificate has Expired” Issues
Kubernetes clusters rely heavily on x509 certificates to authenticate and secure communication between components like the API server, etcd, and kubelets. If these certificates expire, we may encounter errors like:
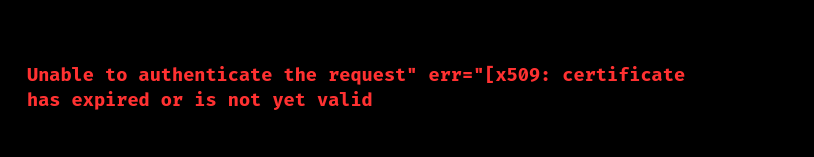
Such issues can disrupt the cluster’s functionality. This guide will walk us through the causes, solutions, and preventative measures for handling expired Kubernetes x509 certificates.
Understanding the Causes
1. Kubernetes API Server Certificate Expiration:
Certificates used for authenticating API server requests are stored in /etc/kubernetes/pki.
They may expire if not rotated or renewed periodically.
2. etcd Certificate Expiration:
etcd, a key component for Kubernetes data storage, uses certificates for communication.
Expired etcd certificates lead to cluster communication breakdowns.
3. CA Certificate Expiration:
If the root CA certificate expires, all certificates it signed become invalid.
Step-by-Step Solution
1. Identify Expired Certificates
Check which certificates have expired using kubeadm:
kubeadm certs check-expiration
For detailed expiration information, use OpenSSL:
openssl x509 -in /etc/kubernetes/pki/apiserver.crt -noout -text | grep 'Not After'
Or inspect certificates across the /etc/kubernetes/pki directory:
find /etc/kubernetes/pki/ -type f -name "*.crt" -print | xargs -L 1 -t bash -c 'openssl x509 -noout -text -in {} | grep "Not After"'
2. Renew Expired Certificates
Using kubeadm
Renew all certificates in one command:
kubeadm certs renew all
If we want to renew a specific certificate, refer to:
kubeadm certs renew --help
Manual Renewal
Manually regenerate expired certificates. For instance, to renew the API server certificate:
openssl genrsa -out apiserver.key 2048 openssl req -new -key apiserver.key -out apiserver.csr openssl x509 -req -in apiserver.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out apiserver.crt -days 365
3. Restart Components
Restart key services to apply the renewed certificates:
sudo systemctl restart kubelet
If we’re using etcd, ensure it restarts too:
sudo systemctl restart etcd
4. Update Configuration
Update the Kubernetes configuration with the new certificates:
mv ~/.kube/config ~/.kube/config.old cp /etc/kubernetes/admin.conf ~/.kube/config sudo chown $(id -u):$(id -g) ~/.kube/config
5. Test the Fix
Verify certificate updates using kubectl:
kubectl get nodes
Ensure there are no errors related to expired certificates.
Preventative Measures
1. Use kubeadm to periodically renew certificates:
kubeadm certs renew all
We can also automate this process via a cron job or CI/CD pipeline.
2. Regularly check the expiration status with tools like Prometheus or custom scripts.
3. Replace old kubeconfig files in CI/CD pipelines with updated ones after renewing certificates.
4. Adjust validity periods during certificate generation to reduce frequent renewals:
kubeadm init --certificate-key --cert-dir=/etc/kubernetes/pki --csr-only
[Need to know more? Get in touch with us if you have any further inquiries.]
Conclusion
Dealing with expired x509 certificates in Kubernetes can be challenging but manageable with proper diagnosis and tools like kubeadm. Regular monitoring and automated renewal processes ensure the cluster stays operational and secure.
By staying proactive, we can avoid downtime and ensure seamless cluster performance.







0 Comments