The OWASP CRS Sampling Mode safeguards web apps from a large range of attacks. As a part of our Server Management Services, Bobcares provides solutions to your queries.
In this article, we’ll look into the steps to apply the OWASP CRS Sampling Mode with ModSecurity or compatible web application firewalls. We also look into the way to fix the rollback in case deploying CRS in large service ends up with the rollback of the deployment.
OWASP CRS Sampling Mode
The OWASP core rule set sampling mode can be used when we need to deploy ModSecurity and CRS on an existing, but poorly defended service for the first time. We can only use the sampling mode to perform CRS on a small portion of the traffic. The remaining traffic will evade the set of rules. Therefore, only about 1% of the traffic will be impacted if ModSecurity is trying to kill or if the rules are too severe for the server. And that shouldn’t do much damage, especially if we monitor the logs and roll back the deployment as soon as the alarms start to build up.
How To Apply OWASP CRS Sampling Mode?
1. In the crs-setup.conf configuration file, find the rule id 900400 which defines the Sampling Mode / Sampling rate.
2. Uncomment this rule and enter the desired value in the variable tx.sampling_percentage.
3. Restart the server after that, and ideally send out a few requests with a payload that resembles an exploit.
$ curl -v http://localhost/index.html?test=/etc/passwd
4. Now apply the rule. The anomaly threshold is less than or equal to 10. We’ll receive a 403 error. The error message looks like this:
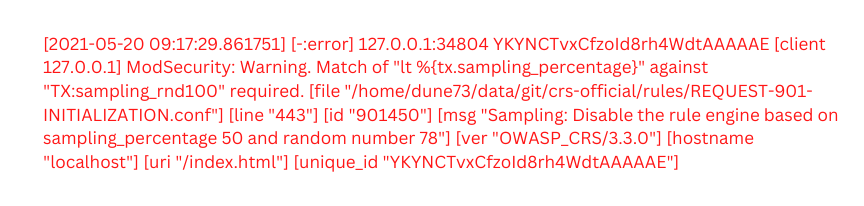
According to CRS, the rule engine was disabled because the random number exceeded the sampling threshold. We choose the sample percent, the rule set creates an integer random number in the range of 0 to 99, and if the result exceeds the percentage, the WAF is disabled for the remaining requests. Therefore, be aware that any other rule sets we may have placed will also be disregarded.
We will receive a valid response with a status of 200 if the sampling mode engages and the rule set is overridden. We receive a log record from 901450 for requests where the rule specified is bypassed. The rule set is used generally for the other requests, those that do not contain a 901450 entry.
Apply the following directive after the CRS include the statement or in RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf to quiet the rule if we believe 901450 is spamming us or that it is already burdening the logs.
SecRuleUpdateActionById 901450 "nolog"
How To Rollback OWASP CRS Sampling Mode?
Sometimes deploying CRS in large service often ends up with the rollback of the deployment. We also have an easy way to fix it. If we set tx.sampling_percentage as 0, then all the requests will bypass the WAF. This is effective after a web server reloads only. Now that ModSecurity and CRS have been installed, they are ready to use, but we have entirely turned them off.
[Looking for a solution to another query? We are just a click away.]
Conclusion
We’ve provided the steps from our Support team to run and apply the OWASP CRS Sampling Mode in this article, along with the way to rollback OWASP CRS Sampling mode.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.




0 Comments