Read the article to find out the method of configuring HAProxy from letsEncrypt using Ansible. Bobcares, as a part of our Server Management Services, offers solutions to every query that comes our way.
How to set up HAProxy from letsEncrypt using Ansible?
We must install an SSL/TLS certificate to bind HAProxy to HTTPS port 443 and pass it to port 8001. Let’s Encrypt provides me with a free SSL/TLS certificate. Through Certbot, the certificate request executes automatically. Certbot may also use Apache and nginx to automatically install the certificates. A unique plugin helps with the installation and the Greenhost: HAProxy plugin for Certbot from Let’s Encrypt will provide it.
Installing Certbot is the first step. They will be in an Ansible role as usual. Certbot’s configuration is very closely related to HAProxy’s configuration, so don’t build a separate role for it; instead, append the installation instructions to the bob_haproxy role.
Setting up HAProxy from letsEncrypt via Ansible
Move the first three commands for installing and configuring HAProxy from
roles/happy1_haproxy/tasks/main.ymlCopy Coderoles/happy1_haproxy/tasks/install_haproxy.ymlCopy Code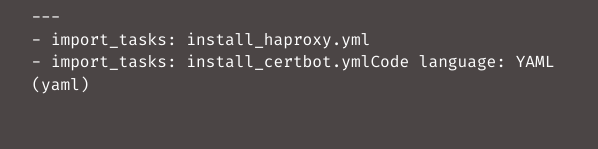
Then create the file
roles/bob_haproxy/tasks/install_certbot.ymlCopy Code
The following command should now run in accordance with Certbot’s HAProxy plugin instructions:
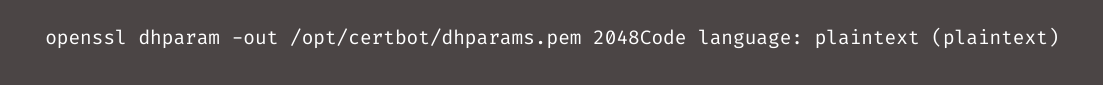
The Ansible module
openssl_dhparamCopy Codeinstall_certbot.ymlCopy Code/opt/certbotCopy Code
Now, we have to create the user certbot and launch Certbot as a user with no privileges. Then immediately remove the Create Certbot directory command and create the user before creating the dhparams.pem file because the Ansible module user also generates the home directory. Now create the following three directories:
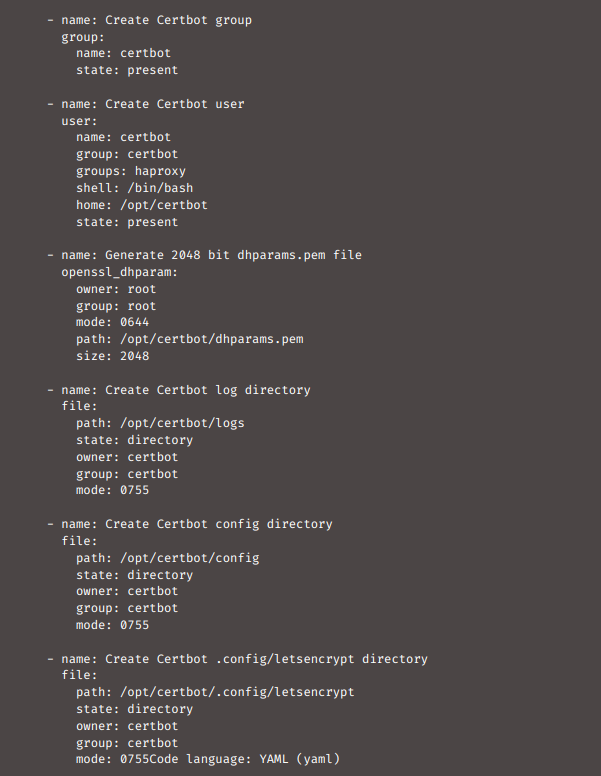
The configuration file
/opt/certbot/.config/letsencrypt/cli.iniCopy Coderoles/happy1_haproxy/files/cli.iniCopy Code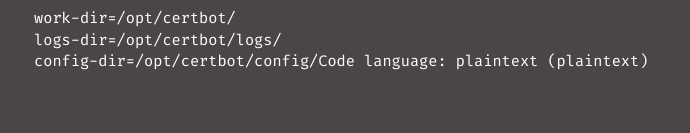
Then add the below code to the tasks definition file in order to copy the file to the server:
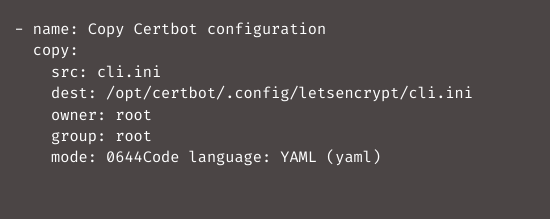
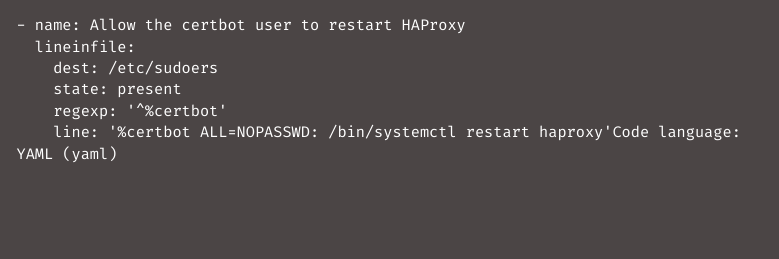
Next, restart HAProxy after the certificate renewal. It is quite simple to grant the certbot user access to this by adding a line to the /etc/sudoers file:
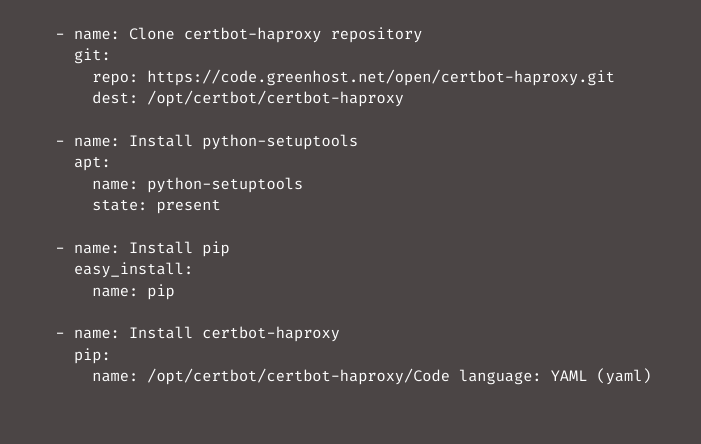
Now install the certbox-haproxy module:
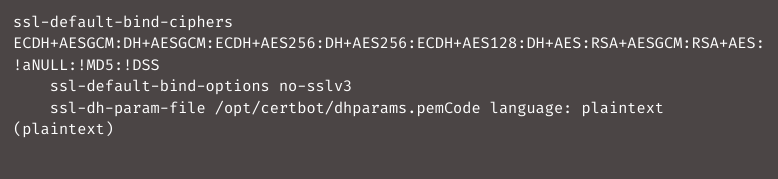
Now, we must modify the haproxy.cfg.j2 file. Enter the file by Ansible, dhparams.pem first by adding a line to the end of the global section, which reads as follows:
The certbot-haproxy module with the port 8000, must also receive requests from the Let’s Encrypt server, whose path starts with /.well-known/acme-challenge. Therefore, add the following to the frontend section:

And at the end of haproxy.cfg.j2, provide the backend certbot:

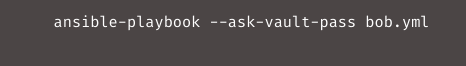
Since the password query is defined in the bobcares_wordpress backend, the Let’s Encrypt server’s challenge requests via the path /.well-known/acme-challenge are not affected. This completes the Certbot installation tasks, and it’s time to run the Ansible playbook:
[Looking for a solution to another query? We are just a click away.]
Conclusion
To conclude, the article explains about the steps to set up HAProxy from letsEncrypt using Ansible.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.




0 Comments