Let us take a close look at centos faillock in detail. We can also look at how to set it up and manage it. At Bobacres our server management support can give you a detailed guide on the whole process.
What is centos Failback?
Faillock acts as a utility or tool for viewing and editing authentication failure record files. The synopsis for the faillock is as follows:
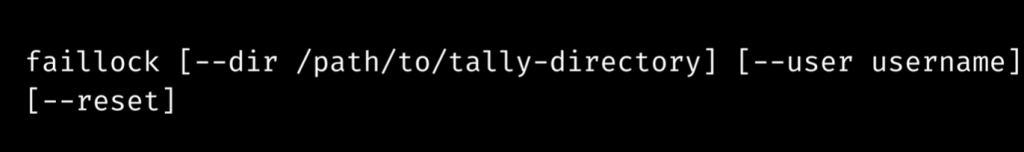
The pam
faillock.soThe faillock command is a program to inspect and edit the contents of tally files. It can reveal the username’s most recent failed login attempts or erase the tally files for all or specific usernames.
OPTIONS --dir /path/to/tally-directoryThe default is
/var/run/faillock. --user username FILES /var/run/faillock/*How to Lock User Accounts After Multiple Failed Login Attempts with centos faillock?
Now we’ll look at how to lock a system user’s account after a particular number of failed login attempts in CentOS, RHEL, and Fedora. The purpose here is to enforce basic server security by locking a user’s account after several failed authentication attempts.
This is done by utilizing the pam faillock module, which assists in temporarily locking user accounts in the event of several unsuccessful authentication attempts and preserves a record of the incident. Failed login attempts are saved in per-user files in the tally directory, which is usually
/var/run/faillock/.pam_faillock is part of Linux PAM (Pluggable Authentication Modules) is a dynamic framework for establishing authentication services in applications and different system services.
How Do we Lock User Accounts After Multiple Failed Authentications or apply centos faillock?
By adding the items below to the auth section of the
/etc/pam.d/system-auth/etc/pam.d/password-auth files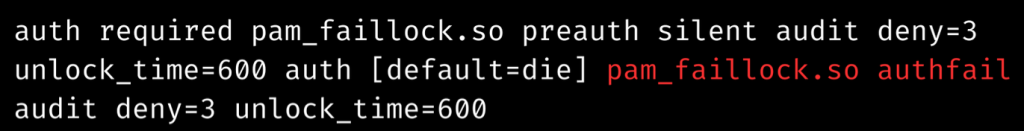
where:
– Allows for user auditing.audit
– used to specify the number of tries (3 in this example) before locking the user accountdeny
– specifies the amount of time (300 seconds = 5 minutes) for which the account should be locked.unlock_time
It is vital to note that the sequence of these lines is critical; incorrect setups might result in the locking of all user accounts.
The following content should be in the ‘auth’ section of both files, in the following order:
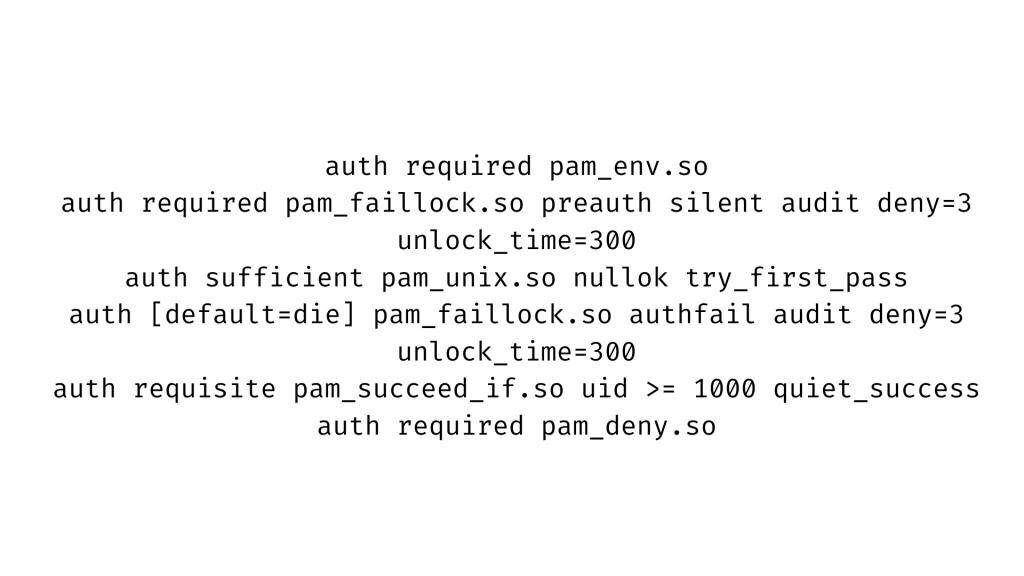
Now we have to open these two files and we can use any editor to complete the process.
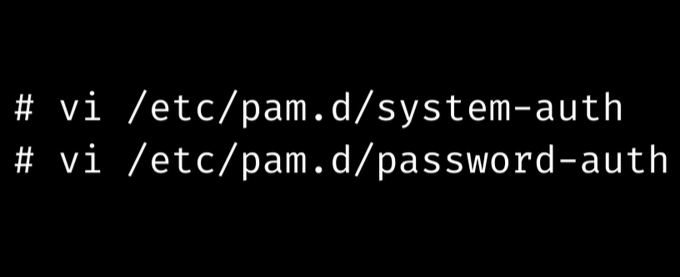
Both files’ default entries in the auth section look like this.

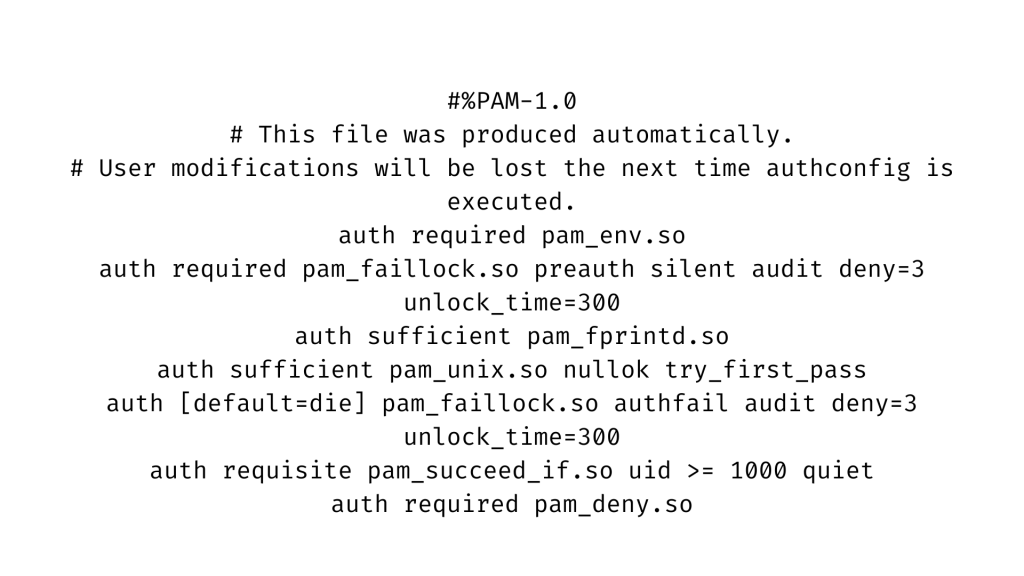
Then, in both of the files above, add the highlighted entry below to the account section.
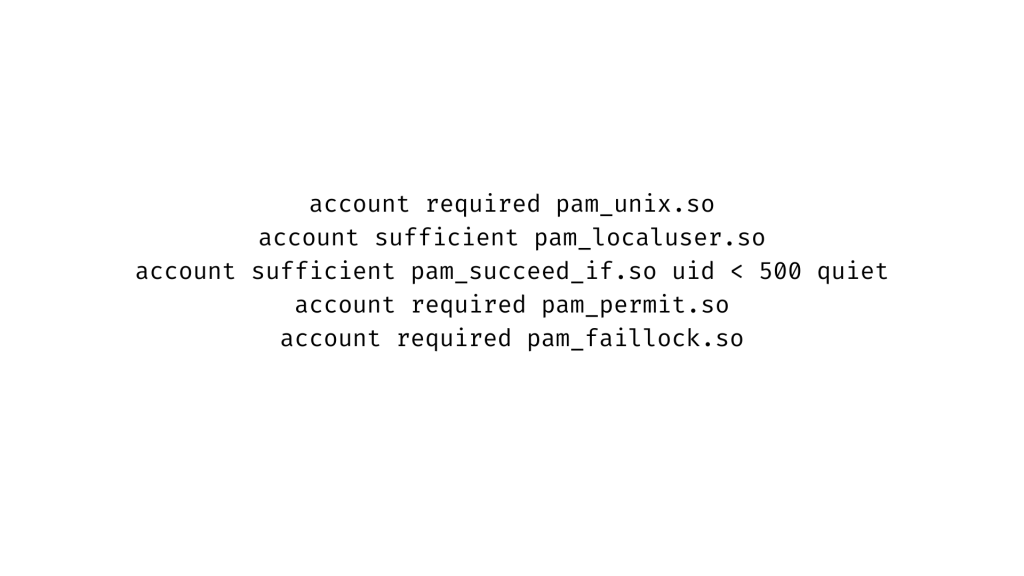
How Do We Lock My Root Account After Multiple Failed Login Attempts?
Add the even deny root option to the lines in both files in the auth section like this freezing the root account after unsuccessful authentication attempts.
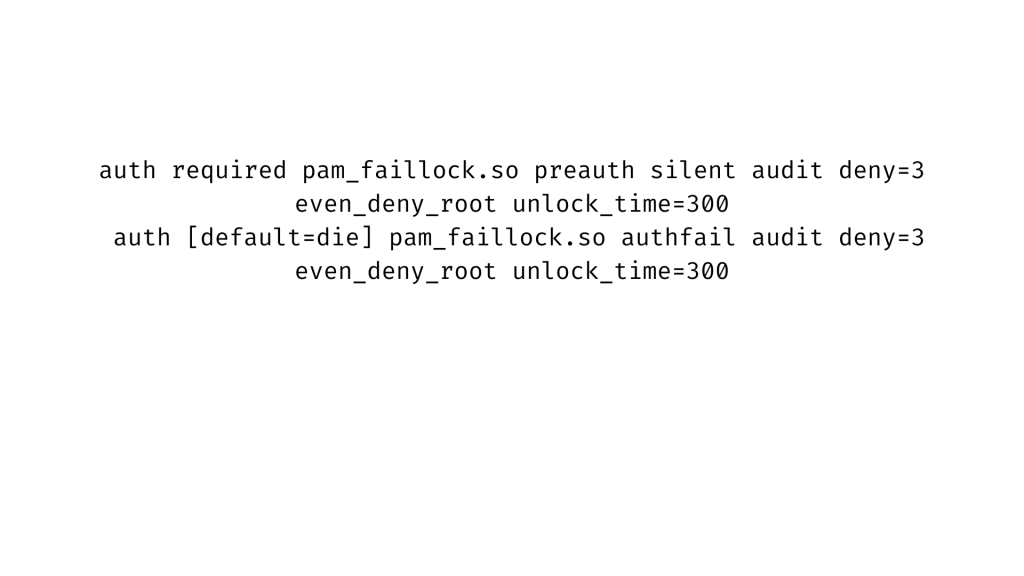
When we’ve finished configuring everything. If users will connect to the server using ssh, we can restart remote access services such as sshd for the aforementioned policy to take effect.
# systemctl restart sshd On SystemD
# service sshd restart On SysVInitHow to Test Failed SSH Login Attempts?
We can setup the system to lock a user’s account after three failed authentication attempts using the parameters described above.
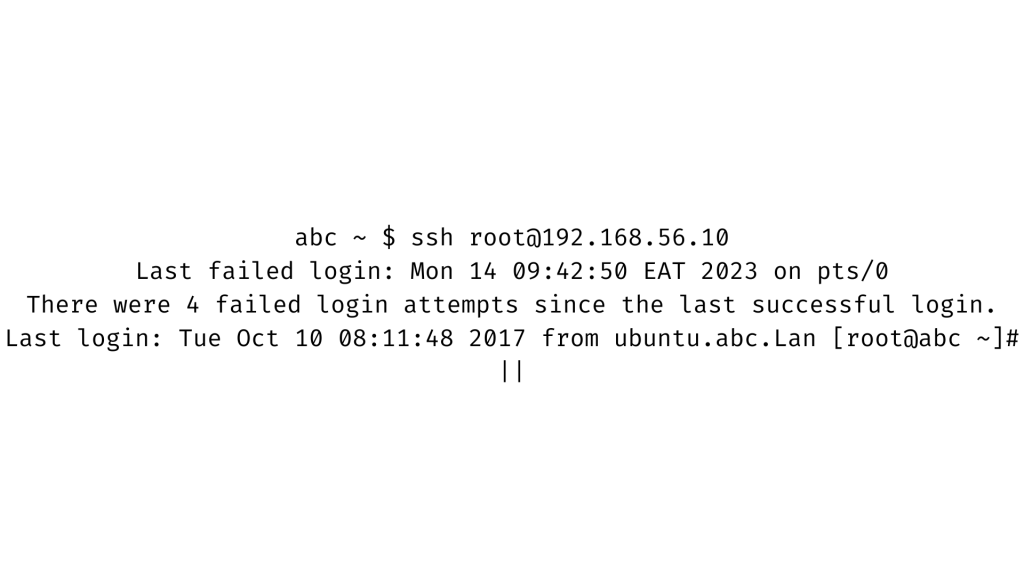
In this case, user abc attempts to switch to user abcd, but after three failed logins due to incorrect passwords, by the “Permission refused” message, the user aaronkilik’s account is locked. indicated by the “authentication failure” message from the fourth attempt.
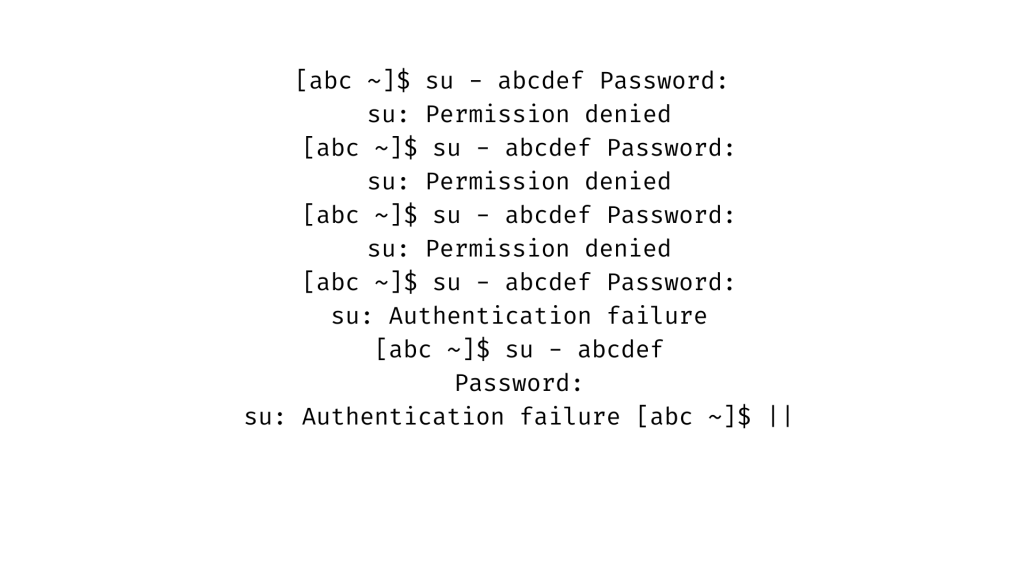
As shown below, the root user is also aware of failed login attempts on the system.
[Need assistance with similar queries? We are here to help]
Conclusion
To sum up, we have now seen more about centos faillock, its usage, setting it up, and how to use it. With the support of our Server management support services at Bobcares.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.







0 Comments