“DKIM-Result: fail (bad signature)” is an error reported by www.appmaildev.com – a DKIM validation website.
It means that the mail sender’s domain (say sender.com) failed an anti-spam test called DKIM, that is used to block fake or altered mails.
Here at Bobcares.com, we help hosting providers (web hosts, VPS hosts, etc.) resolve such errors as part of our Outsourced Tech Support services.
A typical error message looks like this:
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/simple; d=sender.com; h=subject:subject:from:from:to:reply-to; s=senderdkim; t=1536906841; x=1537770842; bh=ULXXzArVdLLQL8y+JLPkvBqQfg=; b=bJAhBd4F2fF5N0u+kd2eh4TbkrukJyzVlPrJ5Pf0uqKu5TGFjXtjitO53FCgl1zJzYIW401dP8ui6Y=Signed-by: user@domain.comExpected-Body-Hash: 5XCn6bdCwq7YPjOROULXXzArVdLLQL8y+JLPkvBqQfg=DKIM-Result: fail (bad signature)
What is the error DKIM-Result: fail (bad signature)?
DKIM enabled mail servers ensure that the mail contents are not altered and the sender ID is not fake through two layers of tests.
They are:
- Create a unique ID (aka Hash) for each mail – The mail server uses the parts of a mail (eg. Sender’s ID, Recipient’s ID, Subject, Time, etc.) to create a unique Hash. This will never be the same for another mail.
- Encrypt the code – This Hash is then encrypted using a secret Private Key which can be decrypted only via a Public Key. This public key is published as a DNS record of the sender’s domain.
For a mail to pass the DKIM test, the recipient server should be able to (1) decrypt the mail using the public key, and (2) be able to regenerate the Hash using the same parts of the mail the sender server used.
Unfortunately these tests sometimes fail, and lands the sender’s mail in spam folders.
When mail users query sites such as www.appmaildev.com to troubleshoot the issue, they see the error “DKIM-Result: fail (bad signature)”.
What are the causes of DKIM-Result: fail (bad signature)?
We’ve seen this error pop-up usually during a new DKIM setup, or after an application upgrade or after a server migration.
In almost all cases, we’ve found the issue was caused due to errors in generating Hashes or in setting up the public key.
Here are the top 3 issues:
1. Wrong or corrupted DNS records
The DKIM public key is published as a DNS record. It looks something like this:
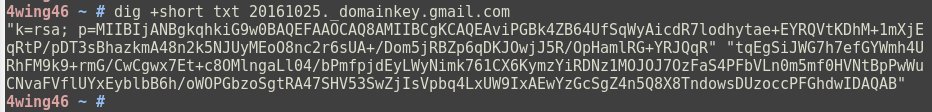
That long line of characters starting with “p=“is the public key. As you can see, the public key can span over several lines.
To set this DNS record, server owners copy-paste the key into the configuration window. In that process they often introduce whitespace or newline characters which breaks the public key.
We’ve also seen cases where webmasters use an old public key which doesn’t match the private key used to encrypt the message Hash.
Solution : The fastest way to fix this is to generate a new public-key private-key pair, and update the settings without syntax errors. This avoids a lot of digging around to find the right key pair, or to fix any missing characters in the existing key.
2. DKIM server config errors
Some DKIM implementations use an independent service such as OpenDKIM.
We’ve seen cases where the service either doesn’t run, or the mail server is unable to connect to it.
For eg. OpenDKIM communicates with the mail server through port 8891 in Ubuntu servers. But this connection can fail if OpenDKIM crashed for some reason or if the port is blocked by firewall.
When the mail server is unable to communicate to the DKIM service, message Hash will not be generated, and the verification will fail.
Solution : To solve this error, we look at exactly why the DKIM service is inaccessible. We setup auto-restart facilities to recover from service crashes, and fix firewall rules to make sure the DKIM port is always accessible.
3. App errors that insert chars or spaces
There are DKIM implementations where the DKIM header is inserted by a web application, and not the mail server.
We’ve seen some of these applications insert a white space or an extra character in the headers (for content wrapping) after the Hash ID is generated.
When the header is changed, the Hash will no longer match the mail, and the verification will fail at the recipient’s server.
Solution : Since this is a bug in the application, the fastest way to solve it is to disable DKIM generation until the app bug is fixed by developers. In cases where DKIM is mandatory, we’ve setup DKIM services at the mail server in place of the apps.
Conclusion
DKIM-Result: fail (bad signature) is an error that happens when DKIM signature doesn’t match the mail body. It can happen due to modified mail content or corrupted/wrong DKIM DNS records. Today we saw the top 3 causes our Support Engineers have seen, and the fixes for them.







0 Comments