Quick solutions for failed to fetch service account token gcp authentication issues. Our Google Cloud Support team is ready to assist you.
Failed to Fetch Service Account Token GCP
When an application cannot fetch a service account token, it cannot authenticate with cloud services or APIs. This often happens due to expired tokens, incorrect permissions, or network restrictions. Modern Kubernetes environments use short-lived tokens, and misconfigurations in Google Cloud can also block access.
Failing to retrieve a token can cause errors, delays, or service interruptions. Identifying the root cause and applying the right fixes ensures smooth authentication and reliable cloud operations.
Understanding the Error
When you see the message failed to fetch a servicedont account token it means your application cannot access the credentials it needs to authenticate. This usually occurs because the token has expired, permissions are not correctly set, or network settings prevent the application from reaching the server that provides the token. In modern Kubernetes environments tokens are short-lived, so applications expecting older long-lasting tokens may run into this problem. Similarly, in Google Cloud services network restrictions or IAM misconfigurations can block token access.
When the token cannot be fetched your application may fail to connect to APIs, which can disrupt services or slow down operations. To fix this issue you need to identify the cause by checking permissions, verifying network access, or regenerating the token. Addressing the root problem ensures your application can authenticate smoothly and continue running without interruptions.
Impacts on GCP Services
When a service account token cannot be retrieved in Google Cloud Platform, applications that rely on authenticated access may stop working as expected. API requests can fail, which interrupts essential workflows and can cause downtime for critical services. In cases where applications attempt multiple retries, delays increase and system resources are used inefficiently, affecting overall performance.
This problem also affects users who depend on these applications, as they may face errors or slower response times. Teams managing GCP environments need to spend extra time troubleshooting, which can impact other priorities. Additionally, misconfigurations causing this issue can create security vulnerabilities, making it important to carefully monitor permissions, service accounts, and network settings to maintain reliable and secure cloud operations.
Common Causes
- Insufficient permissions where the service account lacks required roles to access APIs or create tokens.
- Expired or invalid credentials, especially if the service account key has been regenerated or is no longer recognized.
- Network issues preventing the application from reaching the metadata server due to firewall rules or misconfigured routing.
- Changes in Kubernetes or Google Cloud services that require short-lived tokens instead of long-lived credentials.
- Misconfigured Workload Identity setups causing the service account to fail when impersonating other accounts.
- Exceeded API quota limits that block further token requests.
- Errors in project or service account configuration that restrict token generation or API access.
Step-by-Step Fixes
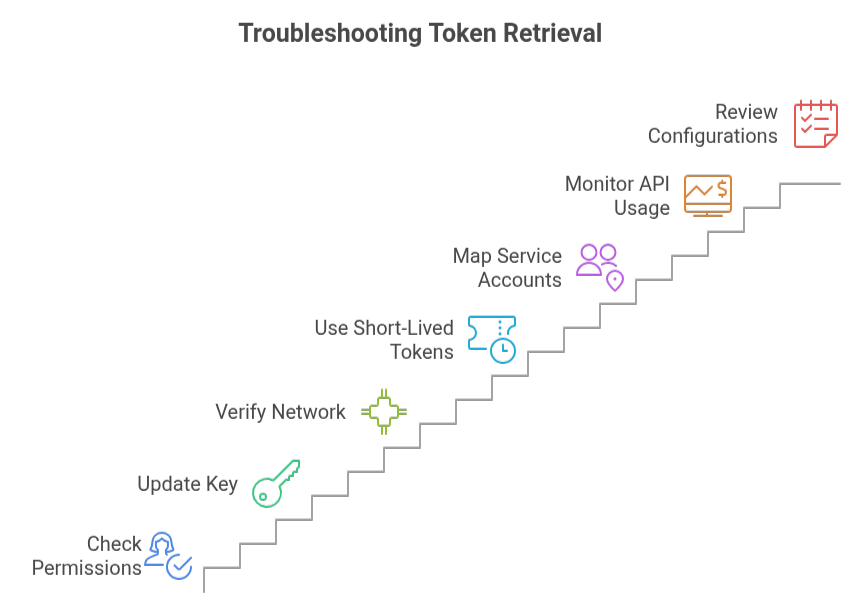
- Start by checking that your service account has all the required roles and permissions to access the resources it needs. Update the IAM settings if any permissions are missing.
- If your service account key is invalid or expired, generate a new key and make sure your application uses this updated credential.
- Confirm that your network allows connections to the metadata server or required API endpoints. Adjust firewall rules or routing if necessary.
- For Kubernetes versions 1.24 and newer, ensure your application is configured to use the projected short-lived service account tokens instead of older static secrets.
- If using Workload Identity, double-check that the Kubernetes service account is properly mapped to the corresponding Google Cloud service account.
- Monitor your API usage to ensure you are not exceeding quota limits. Request an increase if required.
- Finally, review your project and service account configurations to catch any misconfigurations that might block token retrieval.
Prevention Strategies
- Regularly review and audit the roles and permissions of all service accounts to ensure they are correctly configured.
- Keep service account keys secure and rotate them periodically to avoid expired or compromised credentials.
- Monitor API usage and errors to catch issues early and prevent service disruptions.
- Maintain clear documentation of service account configurations and any changes applied to the environment.
- Use infrastructure as code tools to enforce consistent configurations across all environments and reduce manual errors.
- Test network connectivity and firewall rules to ensure uninterrupted access to required APIs and metadata services.
- Stay updated with platform changes, such as Kubernetes or GCP updates, to adapt your authentication and token management practices accordingly.
[Need assistance with a different issue? Our team is available 24/7.]
Conclusion
Experiencing a failed to fetch service account token gcp can disrupt application access to essential APIs and services. By carefully reviewing permissions, network settings, and service account configurations, you can resolve the issue and prevent future occurrences. Regular monitoring and proactive management ensure your applications continue to run smoothly without authentication interruptions.
In brief, our Support Experts demonstrated how to fix the “554 5.7.1 : Relay access denied” error.







0 Comments