From credit card details to health records, everything is stored in a database these days. For a hacker, a database is a gold mine. In fact, the purpose of a majority of cyber attacks is to get access to a database.
The security of a database server depends a lot on operating system hardening, network security and physical security. It’s a big list, but since we’ve already covered it in a previous post, today, we’ll take a more focused look at how to secure database server.
Read : A complete list of how to secure a server
1. Enforce a strong password policy
Configure your database to REQUIRE a strong password while creating a user. Some servers like MSSQL has built-in password validation features, while others like MySQL requires you to install additional plugins (eg. validate_password plugin).
Enforce a password policy that sets a password length of 20+ characters, and blocks dictionary words.

There are utilities like “mkpassword” in Linux servers that can help you generate strong passwords
Read : How Bobcares achieves high uptime and security in Linux servers
2. Remove all default users and demo/test databases
Almost all database servers come with a few demo databases and users. These details are public information. So, anyone can login to your server using these details to collect database or user information.
Delete these users and databases as soon as you create your databases.
Read : How to detect un-authorized login using an Intrusion Detection System
3. Change the name of the admin user
If attackers know the administrator username, they only need to guess the password. For many database servers, the administrator username is set by default. For eg. for MySQL it’s “root”.
Change the admin username for additional security.

Who said admin usernames have to be short? You should be using password managers anyway.
Read : How to detect vulnerabilities in your server using OpenVAS
4. Restrict user privileges to only what’s needed
It is common practice to create database users with access to all tables in a database. This is really not needed in all cases.
Give access to only minimum required tables, and limit privileges (SELECT, INSERT, etc.) to only that’s needed by that user. It’ll prevent data loss even if an exploit is attempted.

Limiting user permissions will prevent data loss – unlike how it happened here
Read : How to test your web applications for security vulnerabilities
5. Disable public network access to database servers
Databases are store houses for business applications. There’s no real world situation where end users need to directly access databases.
So, unless you’re a database hosting provider, block all public network access to database servers. For your remote administrators, setup gateway servers (such as SSH tunnels or VPN).
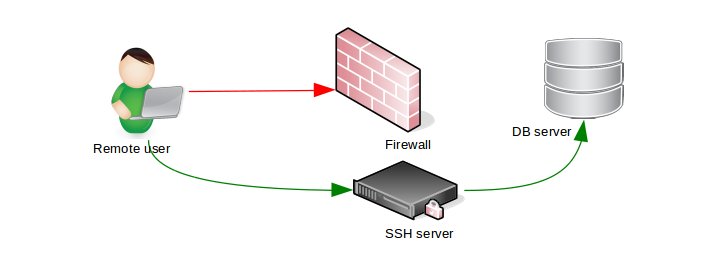
Use non-standard ports and 2 factor authentication on the SSH server for added security
Read : An easy way to enable firewall in Linux servers
6. IP Restrict and enforce SSL/TLS on remote connections
If you are a database hosting service provider, you may need to open up remote connections. In such cases, restrict connection by IP, and enable SSL/TLS encryption on database ports.
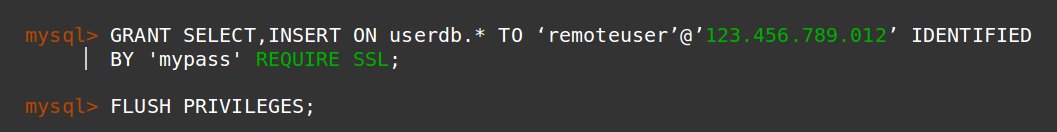
ENFORCE connection over SSL. For eg. in MySQL servers, encryption can be made mandatory like this.
Read : How to optimize MySQL servers
7. Lookout for database dumps in public locations
This is an all-too-common mistake. Application owners take database backups (prior to debugging, upgrades, etc.) and leave them in public accessible locations such as web folders, temporary partition, etc.
Setup your monitoring system to detect SQL dump files in public folders.
Read : How 24/7 monitoring from Bobcares helps maintain security and uptime
8. Consider encrypting your application files and backups
Your application’s configuration files have database access information. If an attacker gets access to the configuration file via an application vulnerability, they can get into the database.
To prevent this, consider encrypting all application files, and their backups.
Read : 7 best practices in maintaining server backups
9. Use a Web Application Firewall and malware scanner
Database servers are often the “back end” for a public facing web application. So, web application exploits are the most common way used by attackers to gain access to databases.
Web Application Firewalls like ModSecurity, NAXSI, etc. can be setup to block all known web application exploits. In addition, they can be integrated with malware scanners (like ClamAV) to prevent sophisticated attacks launched from within the server.
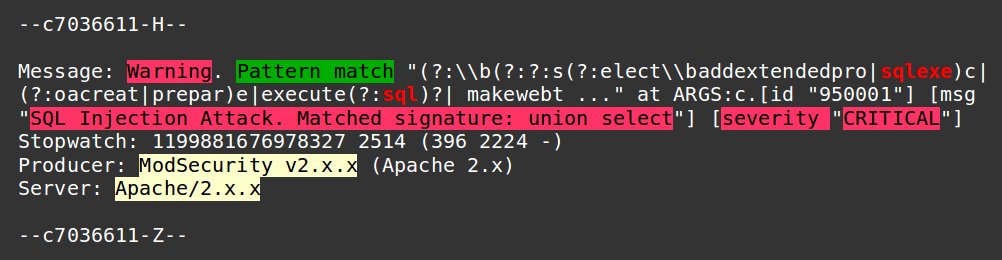
If maintained properly, web application firewalls can block SQL Injection attacks such as this
Read : How to secure your web server
10. Keep all software updated
Well, this would seem a no-brainer. But consider this – Google detects 11,000 infected websites every day, and a vast majority of these infections happen through application vulnerabilities.
So, it’s worth repeating what we already know – Install an update as soon as you get a notification.
Read : How to keep your servers / websites updated and patched
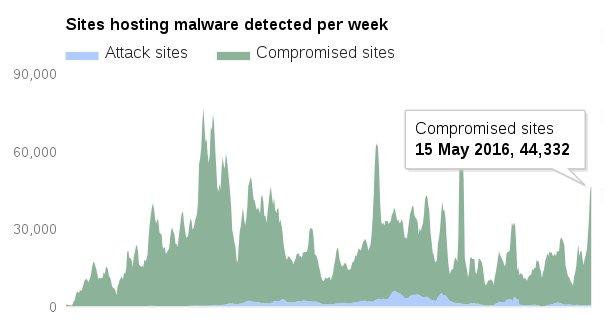
Remember this graph. 11,000 webmasters who thought they’ll update their site “later”
In short..
Cyber criminals craft their attacks to get access to databases. That’s where credit card details and user identities are stored – things that are worth a lot of money. Today we’ve discussed the top 10 ways on how to secure database servers.
Bobcares helps online businesses of all sizes achieve world-class security and uptime, using tried and tested solutions. If you’d like to know how to make your server more reliable, we’d be happy to talk to you.







0 Comments